Identity Manager - Data Governance Edition
Data governance that puts you in control of unstructured sensitive data
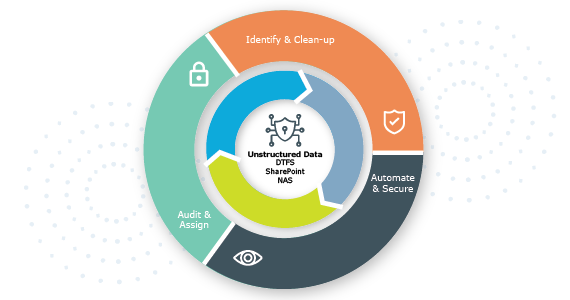
Identity Manager Data Governance Edition secures and enables your organization by putting a data access governance tool into hands of the business owner rather than the IT staff. Identity Manager Data Governance Edition provides a self-service portal to manage access to data using an approval, attestation and fulfillment engine, and enables the business owner to grant access to sensitive data. The power to analyze, approve and fulfill unstructured data access requests is granted to files, folders and shares across NTFS, NAS devices and SharePoint. Identity Manager Data Governance Edition ensures that sensitive, unstructured data is only accessible to approved users, increases security and reduces the burden on IT staff.