Modern security information and event management (SIEM) solutions can collected logs from every type of device including Active Directory (AD) so that companies can search through and analyze “everything”. The question we are often asked is if log collectors and SIEMs can capture “everything” why would anyone need Change Auditor for Active Directory?
The answer has to do with the definition of everything? SIEM solutions can do wide, heterogeneous event log correlation but if only collecting log information they are limited to the information in the native logs for Active Directory (AD). Quest wants to expand the definition of “everything” beyond native logs to provide even deeper auditing information. Furthermore, we can integrate with and complement a SIEM solution by filling in gaps SIEM solution cannot mitigate relating to AD logs.
Although native auditing in Active Directory maybe good enough for small, simple environments, large complex environments with compliance regulations and high standards of security, will find the native auditing gaps puts them in a high risk exposure situation because of the following security gaps in native AD auditing:
- Cryptic and often divided details make permission and configuration change events unusable
Many items that appear within the native event logs are difficult to interpret. A good example is permission changes made to Active Directory objects such as Organization Units. Microsoft codes permission changes in SDDL format. Many actions within Active Directory can generate several events within the event log. An administrator would need to understand these event relationships to interpret the numerous event log entries. Examples of such events include Domain Controller promotions and Global Catalog server promotions.
Change Auditor translates all changes such as permissions changes into human readable form. Including, before and after values, who made the change, where change was made exact setting that changed and where did change originate from. Change Auditor also correlates related events that are initiated through a single action into one meaningful event. Capturing the before and after values is a key Change Auditor advantage over native logs.
-
Inability to protect sensitive AD objects/attributes from being modified by Administrators
Using traditional native auditing and delegation, Administrators in active directory need to have full reign control to do anything in Active directory and its objects. This puts the organization in an unnecessary high risk exposure situation because these administrators can modify access to sensitive groups, computer, users and their attributes which can lead to potential compliance violations and or loss of sensitive intellectual property by accidental human error, malicious intent or by compromising one of the administrators accounts.
Change Auditor for Active Directory allows you to specify list of authorized users to make changes to sensitive security groups or AD objects and attributes regardless of them being domain administrators. It will also notify you in real time of the unauthorized attempt to modify these sensitive resources in Active Directory and keep an audit trail of attempted unauthorized modification which is essential for quick root cause analysis.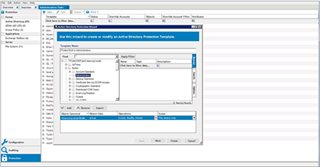
-
Lack of proper auditing detail and alerting for Group Policies affect not only AD itself but also dependent AD-applications needed to run the business
Group Policies are a critical security component of Active Directory. Among other things, Group Policy is used to lockdown workstations, deploy software and control audit settings for domains and servers. Native event logs only track that a GPO has been updated, but do not capture the specific settings changes within a GPO. In a large environment this lack of visibility can create several significant security and operational concerns, first because the time to understand when a GPO has changed is dramatically increased but also because there is no way to read auditing logs to understand exactly what setting got changed so that issue can be remediated and outage can be resolved.
Change Auditor for Active Directory allows you to in real-time understand what critical GPOs are being changed and it helps you clearly understand for each GPO that is changed, what specific settings have been modified, the before/after value of each changed setting, who made the change from where and what domain controller. Change Auditor will even capture GPO Link and Priority changes in an understandable way as opposed to native logs. Using this detailed auditing information, the outage can be reverted in mins. And a GPO protection policy can be put in place to prevent outage from happening in the future. This would allow an organization to tighten security and provide more targeted prevention based monitoring.
-
Log Tampering Risk- Compliance Red flag
The Native audit logs can be erased by an administrator, leading to the possibility of a rogue administrator making changes and then deleting the evidence. Alternatively, administrators may make changes on high volume domain controllers where they know the logs will rollover very quickly and be lost forever, or can make changes on branch office or other remote servers where they know event logs are not reviewed. Administrators could also turn off “Account Management” auditing and essentially creating a black hole to every user and group change happening in AD. This is a major auditing/compliance regulation gap as there is no continuous auditing records
Change Auditor for Active Directory is able to cache events both on the agent side of server and in a separate server which consolidates all events down to a central tracking database in real-time. Quest captures these events directly from Windows and does not rely on the event logs. Even if the main database server was down, the agent will cache this information until the database server is back operationally providing front end and backend redundancy and mitigating risk of having audit records gaps. And Change Auditor doesn’t rely on the native audit policy, so administrators cannot turn it off.
-
Incomplete auditing /alerting of AD Group nesting Changes
Auditing security groups direct and indirect changes and resulting effect is impossible using native auditing. In Active Directory users can be added to groups directly or through membership of embedded or nested groups. Tracking a person or group’s expanded membership can be a very complicated and cumbersome task as all members of a group (including embedded) groups must be expanded to see the resulting membership list. For example adding a user to a group called finance group may indirectly also give that user access to a highly privileged group without organizations realizing the true membership and exposed security risk of that change.
Change Auditor for Active Directory provides complete visibility for group membership by continuously tracking both direct and indirect membership changes.
In conclusion it is also important to note that Change Auditor for Active Directory audits ALL of Active Directory. This includes the Configuration Node, the Schema node (for attribute changes or the dreaded “Schema Extensions”), and other nodes like AD Integrated DNS. Quest innovation utilizes our deep understanding of Active Directory to “tune” this auditing and omit unimportant, high volume changes while we provide our customers several mechanisms to tune their auditing as well.
To learn more, visit https://www.quest.com/products/change-auditor-for-active-directory/
The Author would also like to recognize Alvaro Vitta and Brian Hymer for their contributions to this content.