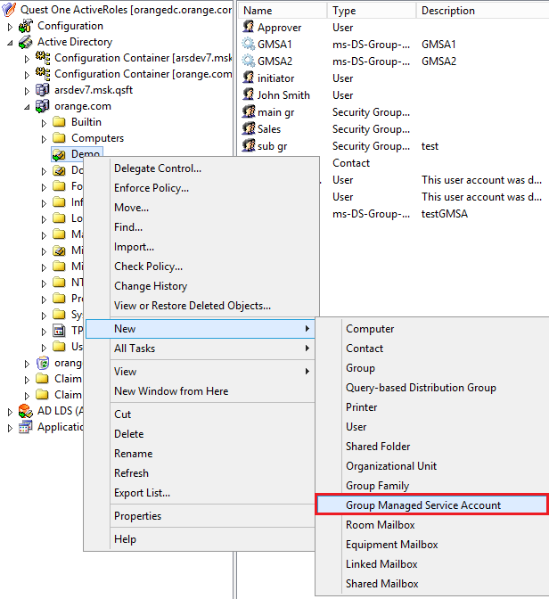
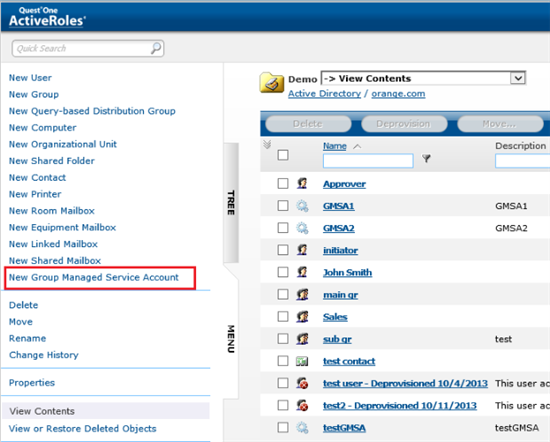
Now ActiveRoles 6.9 allows you to administer group Managed Service Accounts.
Introduced in Windows Server 2012, group Managed Service Account (gMSA) is a domain security principal whose password is managed by Windows Server 2012 domain controllers and can be retrieved by multiple systems running Windows Server 2012.
Group Managed Service Accounts provide the same functionality as Managed Service Accounts introduced in Windows Server 2008 R2 but extend that functionality over multiple servers.
To create and manage group Managed Service Accounts you can use both ActiveRoles snapin and Web Interface.
Ensure that the Active Directory domain in which you are going to create a group Managed Service Account (gMSA) meets the following requirements:
• The domain has at least one domain controller that runs Windows Server 2012 or later.
• The domain has the KDS Root Key created.
In order to check KDS Root Key, run these cmdlets, using Windows PowerShell:
Get-KdsRootKey - check whether the key is set or not
Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10)) - create the key (for more information use this link https://technet.microsoft.com/ru-ru/library/jj128430.aspx)
| ARS snapin | ARS Web Interface |
|---|---|
 |
 |
 |
 |
 |
 |
 |
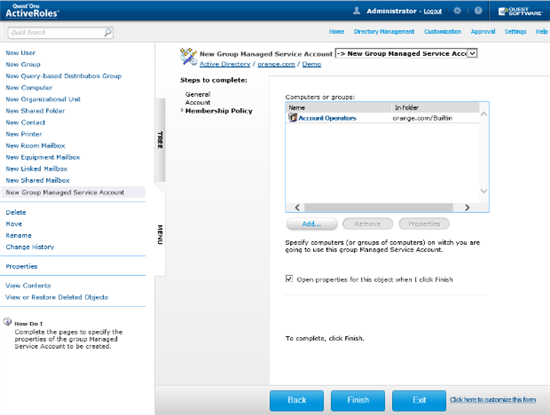 |
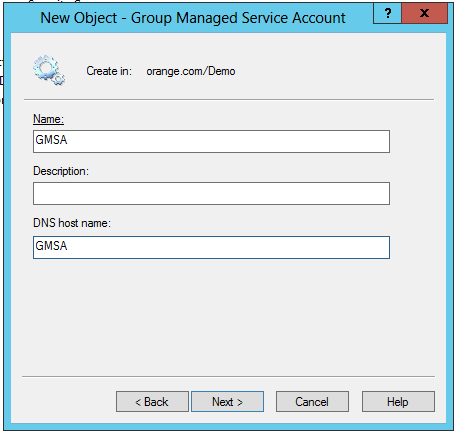
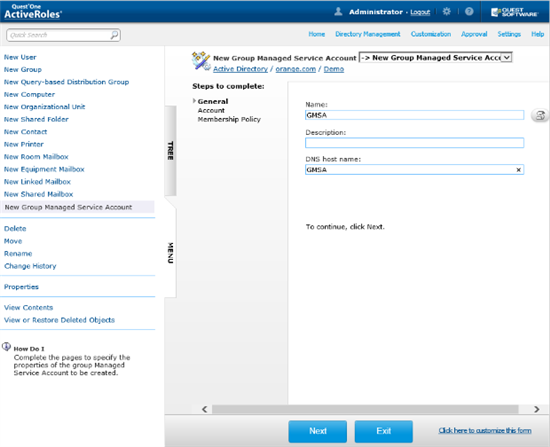
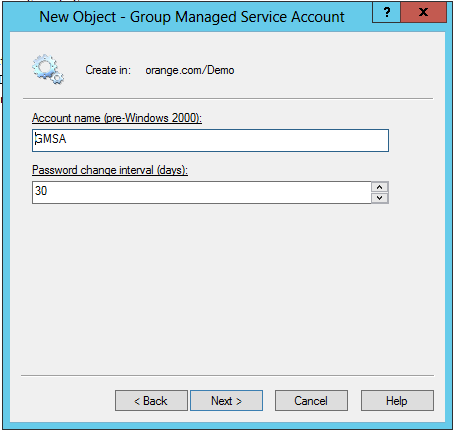
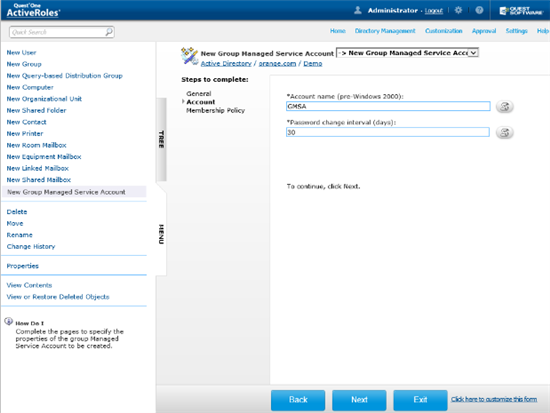
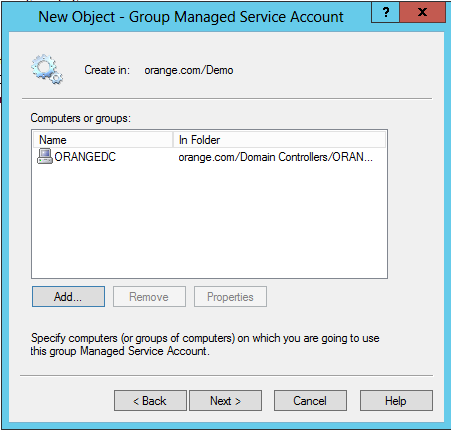
Once you have created a gMSA, you can view or change the account’s properties in the ActiveRoles console: right-click the gMSA and click Properties. This opens a dialog box containing the same fields as the account creation wizard, with the only difference that the Password change interval field is read-only. In addition, the Account is disabled check box on the Account page shows whether the account is disabled for logon, and allows you to disable and re-enable the gMSA.
To delegate administration of group Managed Service Accounts, use the appropriate Access Templates held in the Configuration/Access Templates/Active Directory container in the ActiveRoles console. The Access Templates you need for that purpose have the name prefix gMSA.


