
Part 1 of my series explained why your efforts to secure your organization is a matter of national security – protecting the intellectual property (IP) that makes your company successful and bolsters your nation’s economy and ultimate security.
Now, in the next several posts in this series, I’ll dive into some specific Active Directory guiding principles that will help you secure your organization’s IP and the higher purpose of national security. Today’s post (part 2 of the series) focuses on cleaning up your Active Directory attack surface, while the rest of the series focuses on these topics:
- Part 3: Revisit group policy management often
- Part 4: CONSTANT VIGILANCE a.k.a. monitor and alert
- Part 5: Quickly investigate, remediate and recover
Your Active Directory attack surface and how it grows out of control
Most Active Directory networks are over twenty years old and most organizations migrated to Active Directory from Windows NT 4.0, Novell NetWare and even Banyan VINES. You can guarantee your AD has accumulated some clutter over that time, including user accounts that no one is using and computer accounts for long-gone equipment.
You’ve probably even lost track of many of the security groups tucked away in there. Sure you have some with clean owners and clear purposes. But I know you have WAY too many with no clear owners or purpose or even who the users are, if there are any in a particular group. I’ve spoken to several enterprises recently who’ve confessed:
“I just need to STOP THE BLEEDING. There is a proliferation of bad groups on premises.”
“We spent the last 5 years in a massive mapping exercise to try to clean up the 41,000 security groups in our domain.”
“We struggle cleaning up when people leave one role and move to another.”
User and group access is a major problem. Sean Metcalf, Microsoft Certified Master and AD Security expert, outlined eight avenues of compromise for Active Directory in his keynote address at The Experts Conference. Five of the eight had to deal with too broad of an attack surface due to access hoarding.
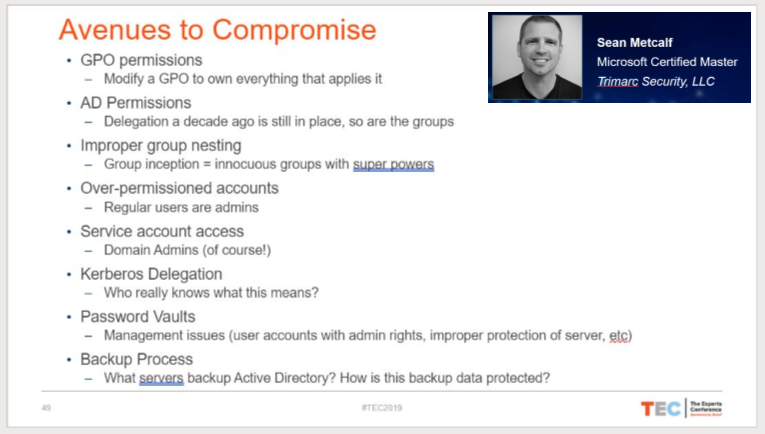
Watch the full recording of his keynote address at TEC here: The Status of AD Security.
Reduce your Active Directory attack surface
Step one: Clean up
The first step in reducing risk is cleanup. Begin with the IT environment itself: Reduce the number of forests and domains. Identify and remove duplicate and other unnecessary groups. Remove unnecessary software installed on domain controllers and sensitive servers.
Then reduce the ways that environment could be misused or exploited. Limit permissions of all users — especially privileged users — in strict accordance with the least privilege principle. Be sure to set account expiration dates when creating accounts for temporary staff such as contractors, interns and visitors. Reduce delegation across organizational units, and prevent domain controllers from accessing the internet.
Step 2: Harden access control to sensitive systems and credentials
To further minimize the risk that your most valuable data can be compromised, require multi-factor authentication on sensitive systems, and ensure admins use jump boxes when connecting using privileged accounts and that they log on only to hardened workstations.
Manage your privileged accounts using a hardened password vault solution. And instead of granting anyone permanent admin access to sensitive servers, use temporary group membership with automatic start and end date/time.
Step 3: Keep a close eye on Privileged Group Membership
Once your house is in order, you need to monitor the actions of everyone in it. Watching for privilege escalation should be at the top of your list. Monitor in real time not only direct changes to privileged groups (which can be tracked in native security logs), but also any additions of members to nested groups (which Windows servers do not log). Privileged groups to monitor include: Administrators, Print Operators, Network Configuration Operators, DHCP Admins, Backup Operators, Incoming Forest Trust Builders, Account Operators, Cert Publishers, Group Policy Creator Owners, Domain Admins, Domain Controllers, Enterprise Admins, Server Operators, RAS and IAS Servers, Schema Admins.
Next steps
These are just several ways to reduce your Active Directory attack surface. I highly recommend you watch Sean Metcalf’s keynote presentation at The Experts Conference earlier this year to get a better understanding of common AD security issues and mitigation steps/techniques. I also encourage you to watch the on-demand webcast that explores WHY all of this work is so important. CISSP and Strategic Systems Consultant, Bryan Patton, and I make the case for WHY your role in securing your organization is indeed a matter of national security. You can watch that here.
SOURCES:
- Photo by Marcin Szmigiel from Pexels.com



