Active Directory (AD) is the beating heart of any Microsoft environment — authenticating users, authorizing access to resources and much more. A critical part of AD is Group Policy, which provides centralized management and configuration of operating systems, applications and user settings. For example, you can use Group Policy objects (GPOs) to prevent users from choosing overly simple passwords, prohibit the use of USB devices on user workstations and keep remote computers from connecting to a critical network share. Clearly, it’s essential for security and compliance to set up your Group Policy properly.
The good news is, you don’t have to figure out what that means from scratch. Instead, you can use security technical implementation guides (STIGs). The premise behind STIGs is simple: the default configurations for many systems and applications are inadequate for security and regulatory compliance; STIGs provide hardened configurations that make those applications more secure. There are STIGs for database applications, open source software, network devices, virtual software, and operating systems, including mobile operating systems.
In particular, a number of STIGs have been developed by the Defense Information Systems Agency (DISA), which is responsible for maintaining IT security at the U.S. Department of Defense (DoD). While it is mandatory for some U.S. federal government agencies to use these settings to harden their environments, there is nothing stopping you from getting a copy of the DISA STIGS and adapting them to meet your organization’s needs. In fact, you can download these settings as a Group Policy template from the DISA website.
Then what? Well, Quest® GPOAdmin enables you to easily import these settings, compare them side-by-side to your current Group Policy settings, modify them as required for your unique IT environment, test them to ensure they work as intended, and roll them out to your production environment. In short, GPOAdmin delivers the end-to-end GPO management you need to ensure IT security and compliance. Let’s step through the process.
First, we import the zip file containing the DISA GPOs:
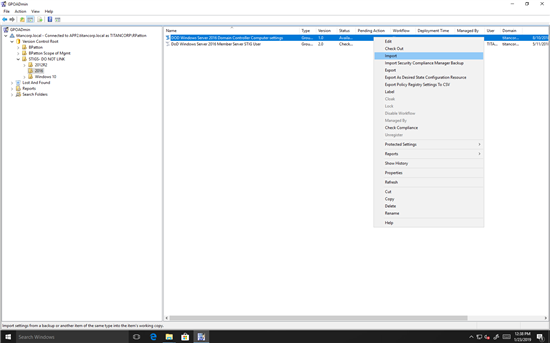
Figure 1. Importing DISA’s recommended domain controller settings
Next, we unzip the imported file. When we select the top folder, we can see the friendly names of the GPOs:
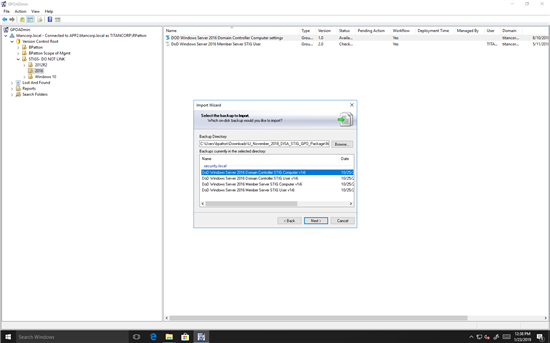
Figure 2. Unzipping the GPOs in the imported DISA STIG file
Then we can easily compare the imported GPOs to our live Group Policy. First, we choose the “Differences” report:
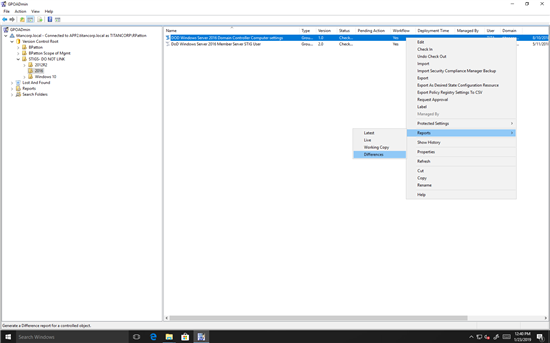
Figure 3. Running a report to highlight the differences between two GPOs
Then we select which GPOs we want to compare:
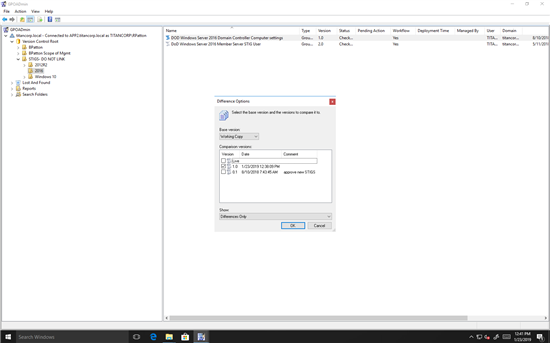
Figure 4. Choosing the GPOs to compare
Then we simply click OK to view the report, which automatically highlights which settings have been changed or removed:
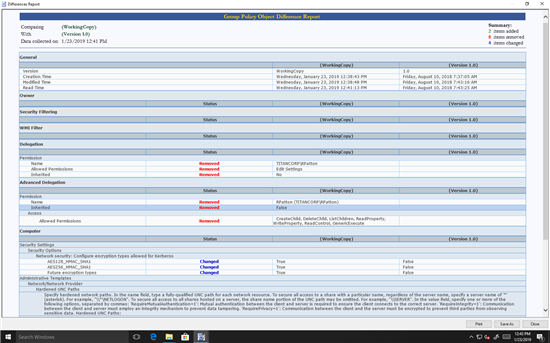
Figure 5. Report highlighting the differences between two GPOs or two versions of the same GPO
Once you’ve reviewed the differences and tested the GPO, you can easily schedule its deployment using GPOAdmin.
See for yourself how GPOAdmin simplifies Group Policy management by starting your free trial. And if you’d like to learn more about how to implement a layered security architecture that enables you to detect, alert on and prevent unauthorized access to GPOs, check out our white paper, “Governing GPOs with a Layered Security Framework.”

