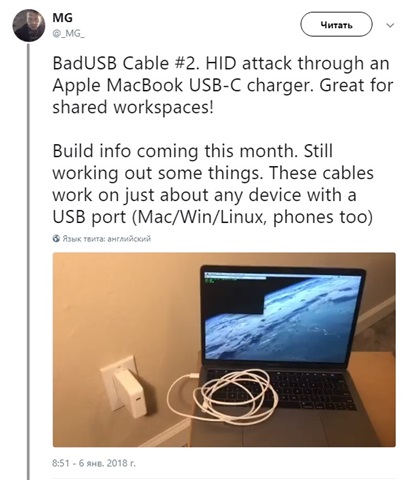
Ladies and Gentlemen, let me introduce to you a malicious USB cable. You probably met him during your last corporate conference in that nice hotel lobby... I'm kidding of course, or am I?
https://twitter.com/_MG_/status/949684949614907395
I have a feeling that something changed during past couple of years - a hacker's attack on your infrastructure is almost inevitable nowadays. Take the above Human Interface Device (HID) attack, aka USB Drive-By, for example. You can patch all your computers against the Meltdown and Spectre cyber security vulnerabilities, but how do you protect from someone using a malicious USB cable to charge their MacBook? I think we should accept the fact that this type of hack in one way or the other is inevitable. It's going to happen no matter what you do.
This doesn't mean by the way that you should drop your antivirus, firewall and any other means of protection. No, absolutely do not do that! That's like plugging your PC directly to the ethernet cable provided by your ISP. You could count the hours until your PC is under some heavy brute-force RDP Ransomware attack. Antiviruses, other endpoint protection solutions, firewalls, threat detection, UBA, SIEM solutions - all of that is extremely important to not being hacked immediately and to be able to do your business without constant DDoS and brute-force attacks.
However, once someone plugged such a malicious USB cable into their corporate notebook, you could be a victim of targeted campaign and extremely experienced hackers could be going after your valuable data. Therefore, you need a level of protection which helps if not catch them immediately, but at least increases the chances of being able to catch them by members of your IT Security team. Any movement, any inaccurate logon or launched process, should be recorded and saved for future analysis and response measures.
This creates a challenge to collect, store, analyze and search all this data. Luckily, this could be easily solved by Quest InTrust. It provides reliable and highly compressed storage for events and automatically indexes the data for future full-text search and correlation between events. This is especially easy with IT Security Search, which requires no training from your IT administration or security team. Just type something in a search string, or simply click search and filter out suspicious data. For example, you could pinpoint all events about USB mass storage devices connected in your environment yesterday, and you'll be able to see which computers and users done it the most and even continue your investigation drilling down for events for a particular workstation/account
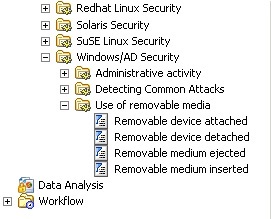
InTrust even has a special rule to detect USB devices connected to your workstation. You can easily set a response action, such as immediately downgrade permissions for the corresponding AD account or enable firewall, or just send an email to the logged on user and enable additional auditing.