Let me be very clear when I say that I do not advertise Foglight for Databases as a security auditing or intrusion detection solution. What is interesting to me is a scenario described by a customer working with Foglight to monitor his SQL Server databases. In a similar vein to my friend David Orlandi's post about user-level investigations using Foglight, this customer told me how he used Foglight to find that a user had done something he wasn't allowed to do.
This customer works for a large healthcare organization. As you might suspect, these organizations have strict controls of who can access data and how it can be used. In this organization, users require authorization to access data at specific times. To enforce this policy, the customer had built custom scripting that queries the access control database and sends an exception notification if an authorized user accesses the data at a time they are not authorized to do so.
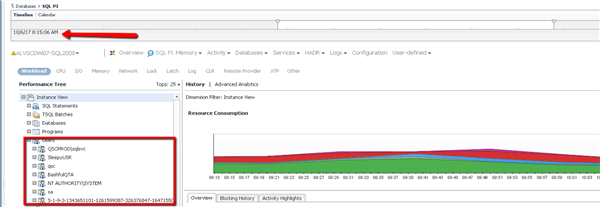
The customer received the exception and began his investigation. To verify the user's activity, he used Foglight for SQL Server's Performance Investigator to navigate to the time of the exception and then expanded the User dimension:
(FYI, this is NOT the customer's data. This is our demonstrative data being used to highlight the workflow)
As you can see, SQL PI (SQL Performance Investigator) lists the users that were active during the specific time interval in question. The customer then expanded the user to further understand the activity:
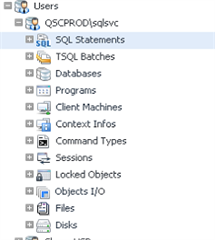
This is where things became interesting for our customer. As you can see, SQL PI (Performance Investigator), provides numerous details about this specific user's activities. Our customer was able to isolate the databases accessed by this user, the machine the user used for access, and the SQL statements the user executed (among other relevant points of data)! Our customer contacted the user and began asking questions about the unauthorized activity. When the user attempted to deny the activity, our customer was able to prove the truth of the matter. Accessing the data at unauthorized times is a violation of their policy so the event had to be reported. Our customer had the evidence he needed to support the violation.
When the customer told me this story, I couldn't help but smile. Please know that I was not smiling about the fact that their corporate policy had been violated. Rather, I was delighted that someone was kind enough to share how our solution was used in a manner that I hadn't conceived. In fact, this customer pointed out that none of our marketing highlighted this particular use case and thought it was important we knew about it. I love it when customers provide me with material for my blog!
For more information about Foglight, please continue to utilize this community or visit our product page.