When you hear “endpoint protection” and “endpoint security,” do you think of your traditional devices, like PCs, printers and network devices? Or do you think of mobile device security for smartphones, tablets and whatever is coming next?
That kind of two-way thinking gives most IT administrators a Colossus-of-Rhodes problem (or maybe “Colossus of Nodes,” in network terms). The Colossus was a huge statue of the Greek sun god Helios erected on the island of Rhodes, usually depicted with one foot on each base at the mouth of the harbor.
The statue was a pretty cool idea, but it didn’t last very long. And trying to keep your traditional endpoint security separate from your mobile security solutions won’t last very long, either. Sooner or later, you’ll have to conduct all endpoint management uniformly instead of keeping your two feet in two separate worlds.
Managing endpoints means managing mobile devices too
The heart of your job is to keep your network safe from security threats while making it as easy as possible for users to access that network from all kinds of devices. Come to think of it, that is yet another way you have to keep two feet in two separate worlds. You end up with separate tools, separate consoles, separate reporting and a separate mindset about two things that will evolve inevitably into one thing.
We hear about these Colossus-of-Rhodes problems from our customers quite often, so we’ve published a white paper called Best Ways to Extend Endpoint Management and Security to Mobile Devices. It describes the process of extending endpoint management to cover mobile device management (MDM). Your users get the access they need and you get the endpoint security and enterprise mobility management you need.
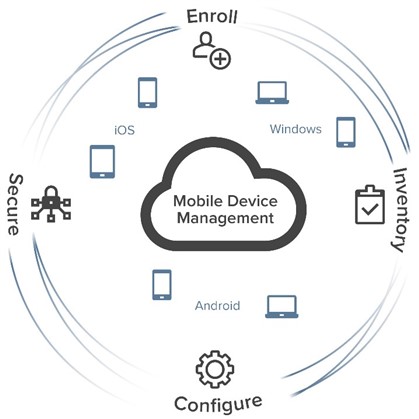
When you think about enterprise mobile device management, you realize that you have to extend four main administrative functions from traditional endpoint management to MDM:
- Enroll — Whereas you can enroll PCs with an agent, enrolling most mobile devices requires an app for a specific operating system.
- Inventory — A comprehensive inventory answers the question “How many devices of all kinds are in the organization, and who has them?”
- Configure — Like traditional endpoints, mobile devices should be accessible to administrators for installing updates, certificates and approved apps, without the need to touch each device manually.
- Secure — If you grant network access to a device, you want to make sure the device is secure, even if that means locking it, locating it, remotely wiping it or resetting it.
As you’ll see in the white paper, the optimal way to extend those four functions is by integrating mobile device management software with a traditional endpoint management system. The result is comprehensive endpoint security and mobile security that goes beyond MDM solutions to cover PCs, laptops, smartphones, tablets, servers, printers and network devices.
Colossus of Rhodes or comprehensive endpoint management? Get the white paper.
Read our white paper, Best Ways to Extend Endpoint Management and Security to Mobile Devices to see whether our enroll-inventory-configure-secure perspective applies to the way your organization looks at endpoints. If it does, then try KACE Cloud Mobile Device Manager for free and gauge the fit in your device landscape.
That poor Colossus of Rhodes lasted a measly 56 years until an earthquake wiped it out. Don’t wait for an earthquake, like the next innovation in endpoints (IoT? Virtual assistants for the enterprise?), to wipe you out.
After all, those who ignore the lessons of their high school Ancient History class are doomed to repeat its failures.
Photo credit: By en:User:Slof (en:Image:SevenWondersOfTheWorld.jpg) [Public domain], via Wikimedia Commons