Are you underestimating your endpoint security risk?
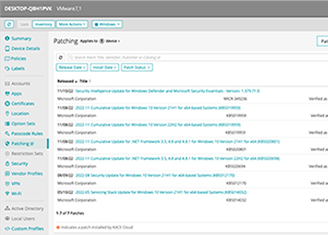
Are you underestimating your endpoint security risk? Learn 5 Steps to Battle Endpoint Cybercrime Clear visibility into all the devices connecting to your network. Automated patching and software deployment. Protection from threats such as unpatched operating systems and applications. Peace of mind that security compliance regulations are being met. Increase in ransomware attacks by 2025. Learn the 5 steps to building a unified endpoint security strategy that provides.