Good morning. My name is Neil Belfour. I'm one of the solution architects with Quest Software.
Today we're going to demonstrate Security Explorer. Security Explorer is a management application that has the ability to manage multiple aspects of your infrastructure, ranging from NTFS security, share security, registry security, printer security, services, service accounts security, task management, groups and user management, ranging from active directory and local, SharePoint, SQL, and Exchange security.
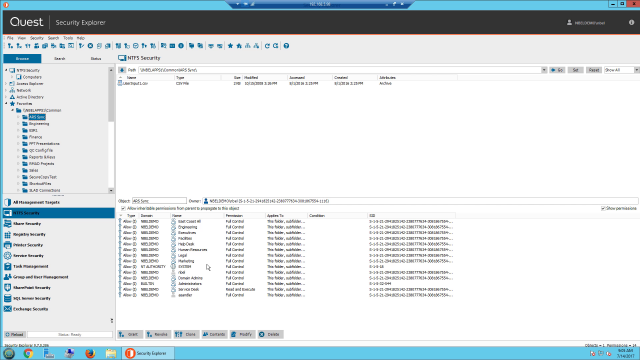
The application is real easy to install. It does not have many prerequisites associated with it. You simply choose the target of what you want to manage. When it comes to NTFS security, I have many features that are available. I can browse to the individual computer within my infrastructure. I can browse through Active Directory to get to it. I can also set up favorite places and even enterprise scopes. Think of those as ways to organize how you want to manage your NTFS security from a shortcut standpoint.
You can see I set up a favorite place here to a random server with a common drive. If I expand this drive and choose a folder within this subfolder, it's going to instantly enumerate what's inside that folder along with the permissions. So if I highlighted a specific directory called Engineering, I can see there are three subfolders and below are the permissions that are associated with it. We would be up to see if the permissions are inherited or explicit.
At this point, what else can I do simply from an NTFS standpoint? Well, when dealing with security, the first thing I would want to be up to do is grant permissions. If I wanted to grant permissions, all I have to do is-- everything is a right mouse click away. I can choose the individual user at this point, give them the permissions that I want to give them, and then add those permissions. And then it's going to ask me if I wanted to include protected object.
What is protected objects? Well, Security Explorer uses an administrative override feature within the application. It gives you the ability to see folders or files that may have been denied permissions if you simply are an administrator.
You can also revoke permissions. When revoking permissions, there are advanced features associated with it. And one of the biggest advanced features that customers take advantage of is the ability to revoke all unknown and deleted accounts. So all those unrecognized SIDs that we see would automatically be removed. You can also clone groups or users. So if you have intern one being replaced by intern two, you can easily clone their permissions.
Security Explorer, it's managing the security at all these different aspects-- from share permissions to even service security. Within service security, we give you the ability to change service accounts as well as logons on all your service across your infrastructure. Groups and user management, as mentioned, does take in active directory groups as well as local groups.
You can also do targeted searches. And you can choose any one of these platforms and simply do a targeted search for a specific permission for an individual user and/or group. You'll notice even at the top level, there is a reporting piece to it. Even though it is not SQL backended, it does reports from a real-time basis and enumeration.
Once again, Security Explorer is available to download from Quest.com. It does come unlimited evaluation for 30 days-- also unlimited tech support. If you have any further questions, please reach out to any one of our sales executives, and you can find out that Information at Quest.com. Thank you for your time today.
 04:21
04:21
