On Demand Audit
Streamline security, compliance and change auditing for hybrid Microsoft environments. Powered by Azure AI and Machine Learning, On Demand Audit enhances your ability to track all configuration, user, and administrator changes across AD, Entra ID, file servers, network-attached storage, Exchange Online, SharePoint Online, OneDrive for Business, and Teams. Using AI-driven insights, this SaaS Microsoft 365 auditing tool identifies critical patterns, highlights security vulnerabilities, and detects anomalous activity with precision and speed.
As you move more workloads to the Microsoft cloud, your reliance on Entra ID will increase, and so will the risk and complexity in securing your hybrid environment. Microsoft 365 and Entra ID security logs don’t provide consolidated views of on-premises and cloud activity, and system-provided tools do not make it easy to identify exploits, vulnerabilities, and suspicious activity. On Demand Audit streamlines and enhances Microsoft 365 auditing by combining on-premises threat prevention provided by Change Auditor with dynamic vulnerability assessment, automatic anomaly detection and contextual visualizations to mitigate costly attacks and accelerate security investigations.
That’s not all!
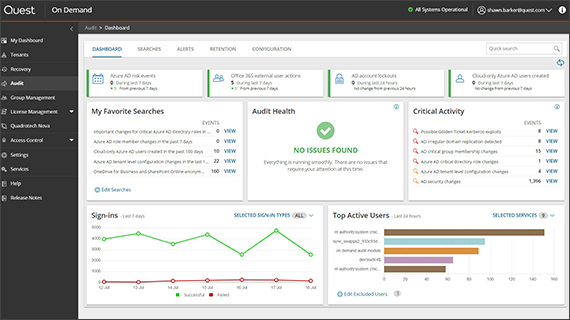
Interactive data visualizations
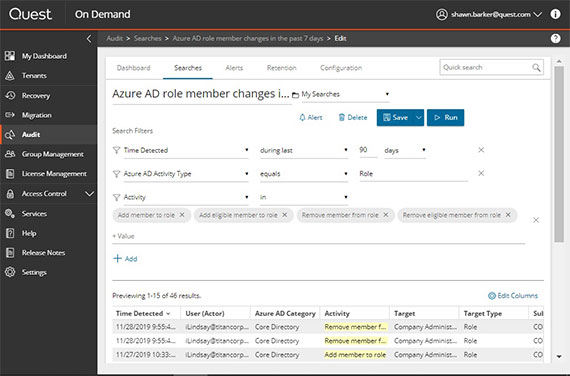
Transform millions of on-premises and Microsoft 365 audit events into interactive visual dashboards that help you simplify compliance reporting and investigate incidents faster.
Threat prevention
Integrate with Change Auditor to block attackers from lateral movement by stopping them from making changes to on-premises groups and GPOs or exfiltrating your AD database to steal credentials – regardless of the privileges they’ve hijacked.
360° security protection
From upfront vulnerability assessment to intrusion detection and monitoring of compromised accounts, Change Auditor has you covered at every step.
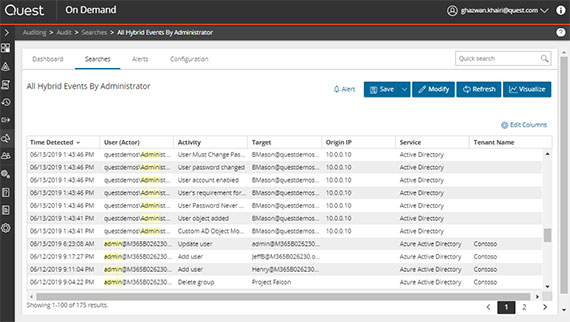
Normalized audit view
Unlike Microsoft 365 auditing using Microsoft-provided tools, On Demand Audit translates raw audit logs into a meaningful, normalized format. On Demand highlights the most important event details, including before and after values, so you can make quick decisions where your security is concerned.
Long-term storage
On Demand Audit stores audit history for up to 10 years at a fixed subscription price. This enables you to keep the audit data you need to satisfy security and compliance policies, without increasing your own Azure storage costs.
Granular, delegated access
In just a few clicks with On Demand Audit, you can give your security and compliance teams, help desk staff, IT managers and even external auditors and partners exactly the reports they need and nothing more. This Microsoft 365 auditing tool provides granular, delegated access to safely empower users to get the insights they need without making any configuration changes and or setting up additional infrastructure.
On-prem, cloud or hybrid? Quest has you covered!

For truly comprehensive Microsoft 365 auditing, upgrade to the On Demand Audit Hybrid Suite for Office 365, which includes On Demand Audit, Change Auditor for Active Directory and Change Auditor for Logon Activity. On Demand Audit consolidates and correlates Change Auditor’s in-depth, high-fidelity on-prem audit data together with cloud activity from Azure AD and Microsoft 365 workloads to get a single, hosted view of all changes across your hybrid environment.
Why Quest On Demand?
Fast, easy setup
Onboard with ease. Start auditing in minutes. No installation, no upgrades, no complex configuration — no sweat!
Secure and reliable SaaS
Quest On Demand delivers the security standards, service level and scalability that you need, backed by award-winning, global support ready to help you 24/7/365.
Rapid innovation
We keep pace with Microsoft updates so you don’t have to. Automatic updates deliver new features and security patches quickly and without any effort on your part.
ISO certifications
Quest On Demand is included in the scope of the Platform Management ISO/IEC 27001, 27017 and 27018 certification.
Specifications
Available in the following Microsoft Azure regions:
- Australia
- Canada
- North Europe
- United Kingdom
- United States
The following web browsers are supported with On Demand:
- Internet Explorer 11
- Microsoft Edge
- Google Chrome (latest version)
- Mozilla Firefox (latest version)
On Demand Audit supports integration with Change Auditor version 7.0.3 or later.
Industry recognition
Resources
Top 10 Security Events to Monitor in Azure Active Directory and Office 365
Discover how native auditing tools can help with cloud security — and how to overcome their shortcomings.
Five Ways to Improve Auditing of Your Hybrid Active Directory
Discover just five of the ways On Demand Audit Hybrid Suite for Office 365 helps you secure your hybrid AD environment.
Ultimate Cyber Resiliency: a guide to combatting AD security villains
This eBook highlights ways to achieve a full lifecycle of hybrid Active Directory cyber resiliency to mitigate risks before, du...
A journey to Zero Trust
Learn how to secure your on-premises Active Directory and enable a Zero Trust security model.
Energy company improves Active Directory security and cyber resilience.
Edison slashes risk with attack path management and auditing tools from Quest.
Seven Steps to Surviving the Active Directory Retirement Crisis
This infographic offers seven valuable tips to help your organization prepare for the impending Active Directory retirement cri...
What You Don't Know About Entra ID Backup and Recovery
In this e-book, learn how to deliver true enterprise-level Entra ID backup and recovery.
Mitigating the top 5 modern Active Directory threats
Discover the five key Active Directory security challenges that organizations are experiencing in the face of modern security t...
Videos
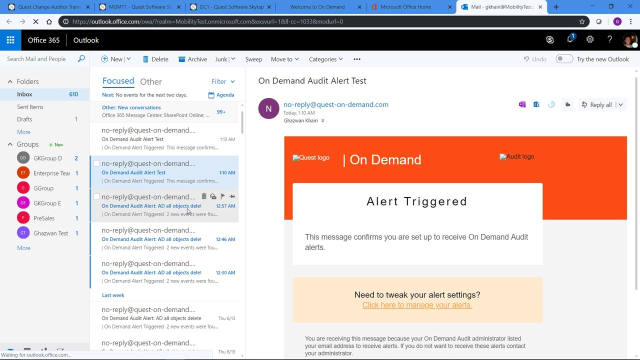
Real-time email alerts with On Demand Audit
Learn about real-time email alerts with On Demand Audit from Quest.
Hybrid AD auditing with Change Auditor and On Demand Audit
Learn about hybrid AD auditing with Change Auditor and On Demand Audit from Quest.
How to integrate Change Auditor with On Demand Audit
Learn how to integrate Change Auditor with On Demand Audit from Quest.
Detecting the use of Golden Tickets with Change Auditor for Logon Activity
Detect and alert on common Kerberos authentication vulnerabilities used during Golden Ticket / Pass-the-ticket attacks.
Blogs
The top activities to track when auditing Active Directory
Learn why auditing Active Directory is vital to security and business continuity, and what types of activity to track.
Ian Lindsay
Understanding Azure AD Sync: An overview of Azure AD Connect Sync and Cloud Sync
Learn about Azure AD sync, the difference between Connect and Cloud Connect sync and security factors to consider.
Susan Bradley
8 cybersecurity predictions for 2025
Check out our top cybersecurity predictions for 2025 to better prepare your organization for the year ahead.
Jennifer LuPiba
Defending your organization before, during and after a cyberattack
Discover key considerations and the essential steps to take before, during, and after a cyberattack to minimize its impact.
Matthew Vinton
Why IAM leaders must prioritize Identity Threat Detection and Response in 2024
Learn why IAM and security leaders must prioritize identity threat detection and response (ITDR) in 2024 and what that they should be focused on.
Richard Dean
What you need to know about Identity Threat Detection and Response (ITDR)
Learn how ITDR encompasses threat intelligence, its best practices and which tools to use for protecting identity systems.
Matthew Vinton
Get started now
Streamline security and compliance auditing of your hybrid Microsoft environment