[MUSIC PLAYING] 95 million Active Directory user accounts are under attack every day. Patch management tools can help you limit exposure, vulnerability management tools can help you meet the long checklists of industry best practices, and detection and response tools are important to alert you to suspicious activity. All three are important to a defense in depth plan, but one critical strategy that is often overlooked is attack path management. While other approaches reduce vulnerabilities, attack path management brings visibility to the paths that attackers might use to take control of your most critical tier zero assets, giving you the knowledge you need to block the most likely attack paths.
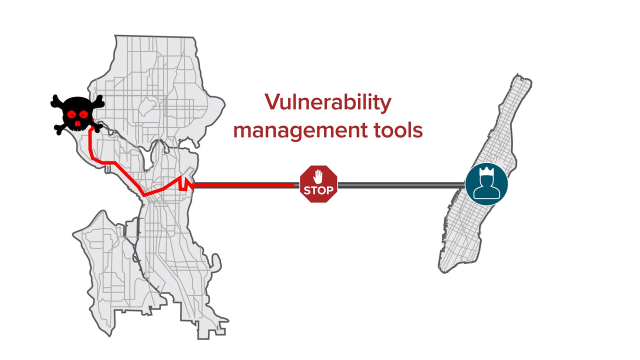
Let's say an attacker wanted to drive from Seattle to Manhattan where the valuable files are located. GPS apps will recommend a handful of options based on optimal time and distance, but there are thousands or millions of possible routes. To put this into Active Directory perspective, vulnerability management is like blocking off the main roads, but cyber attackers will find another route. The more roads you close, the fewer attack paths will be available, but it's impossible to eliminate all of the potential routes.
Because there are so many possible paths, it doesn't matter how many roads you close, cyber attackers will be able to find an open path. But rather than focusing on road closures, attack path management focuses on choke points, the last segment in the route. If you block the bridge to the attacker's destination, you've eliminated a choke point. It doesn't matter how many routes lead to the bridge, if attackers can't cross it, they can't get to the valuables.
Vulnerability management tools don't know where the bridges are. They only recommend closing streets without knowing where they lead. In Active Directory security terms, attack path management identifies all the path attackers can use to get from an ordinary user to your organization's most valuable AD assets.
In most Active Directory environments, there are thousands or even millions of attack paths. Remediating each segment of every path individually is time-consuming and impractical. The choke points are the last segment in an attack path to the most critical assets in your Active Directory. By remediating the choke points, you eliminate all the possible paths below it.
SpecterOps BloodHound Enterprise sheds new light on the thousands of attack paths that exist in your Active Directory environment, and provides practical guidance on how to prioritize and remediate them. Learn more about how Quest can help you reduce your attack surface and improve your overall security posture.
 02:44
02:44
