Scalable, efficient unified endpoint management
Cybercriminals are savvier than ever. They understand that IT complexities create serious vulnerabilities, and these criminals are continually developing new ways to breach your organization's boundaries. That is why a proactive, unified endpoint management (UEM) strategy should be part of your organization's core business strategy.
Exploitation of IT vulnerabilities is escalating.
While total IT vulnerabilities
have been decreasing, the number
considered critical is on the rise
- and so are the number of exploits:
The increase in IT vulnerabilities determined to be critical since 2014.
The increase in exploits as a percentage of vulnerabilities since 2014
Learn about Managing All Devices with Unified Endpoint Management (UEM)
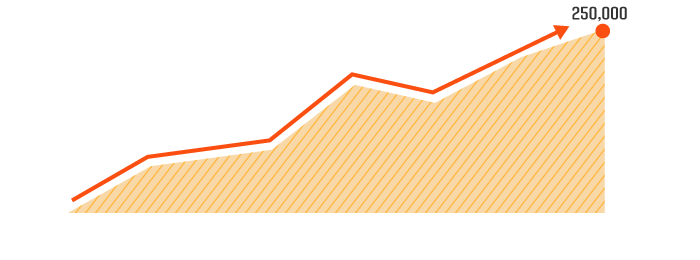
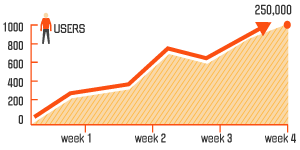
Complexity is also on the rise.
Take a look at the number of patches, updates, configuration changes a
mid-size enterprise of
1,000 users might see in a month's time:
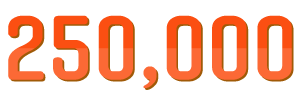
The median value of the number of changes to the endpoints over a one-month period 1
See how rapidly you can achieve ROI with our ROI calculator
Research ROI Calculator