Recovery Manager for Active Directory has long been an indispensable part of an Active Directory administrator's toolkit. Its ability to take full backups of Active Directory make it perfect for quickly reversing an ill-advised change, and its robustness make it an ideal part of back out plans for Change Management processes.
Recovery Manager for Active Directory has long been an indispensable part of an Active Directory administrator's toolkit. Its ability to take full backups of Active Directory make it perfect for quickly reversing an ill-advised change, and its robustness make it an ideal part of back out plans for Change Management processes.
But there is a use case that is not as often associated with Recovery Manager for Active Directory: detailed, forensic-style analysis of Active Directory changes.
Perhaps a software install such as Microsoft Exchange has made large amounts of changes to Active Directory that are important to document. Perhaps there is the potential that a threat actor has found their way into Active Directory, and it is critical to analyze any and all changes that have been made.
Most organizations rely on auditing to track changes to Active Directory. Sometimes this is done through native logging, sometimes through specialized tools such as Quest's Change Auditor. Auditing with these tools is extremely important as they capture critical pieces of information such as when an Active Directory change occurred, and who made the change.
But both native log auditing and Change Auditor share a weakness - if they are not configured to look for a change they will not audit it. This isn't necessarily a drawback as keeping the "signal to noise" ratio high is critical to effective day-to-day auditing. However, sometimes greater depth is needed.
This is where Recovery Manager for Active Directory can add tremendous value in reporting the differences between two Active Directory backups.
Using Recovery Manager for Active Directory for Comparison Reports
Recovery Manager for Active Directory can report on the differences between a backup and the live Active Directory database, or it can report on the differences between two backups.
From within the Recovery Manager for Active Directory interface, begin an Online Restore.
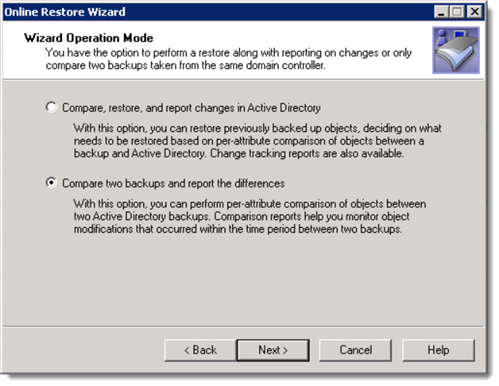
Either choose to compare the live Active Directory database with a backup, or choose two different backups. In this example, we will be comparing two different backups.
Choose the first backup to compare.
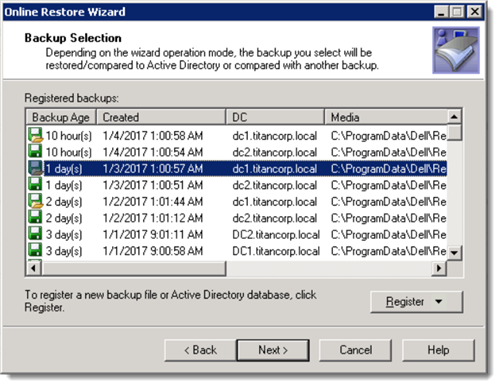
Next, choose the second backup. Recovery Manager for Active Directory will only show other backups from the same Domain Controller for the second selection.
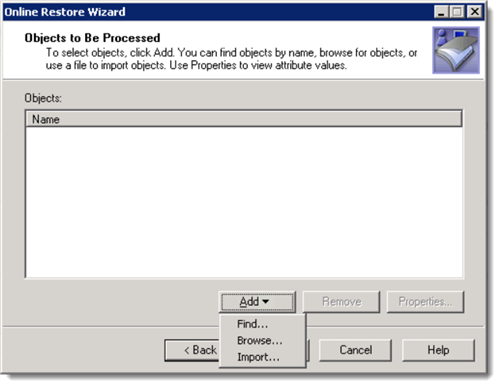
Recovery Manager for Active Directory will ask for objects to be processed. This is where we determine the scope of what Recovery Manager for Active Directory will report on.
Choose Browse… Take note of the Show advanced objects toggle in the lower left corner. This will expose the entirety of Active Directory. From here, you may select up to an entire Naming Context to report on. In this example we have chosen the Configuration Naming Context.
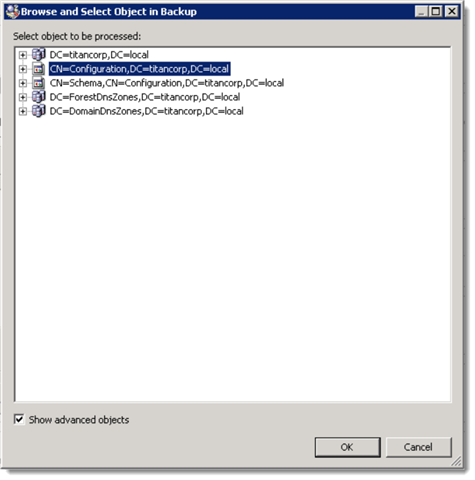
There are several options not shown here on how to further filter the report, such as only including certain object classes.
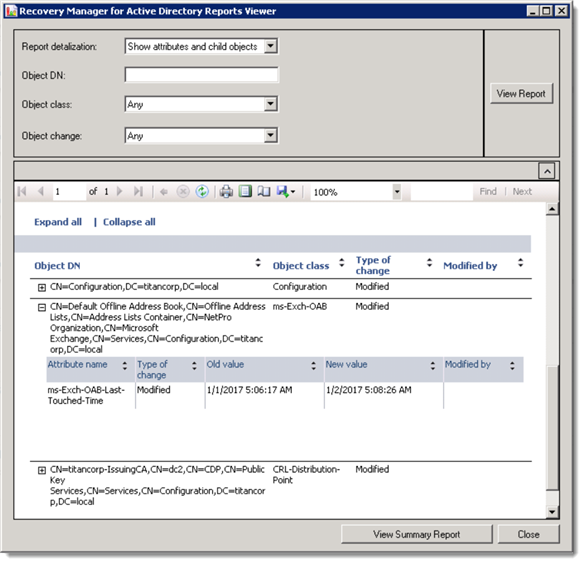
And finally, the finished report. This report can be easily filtered and analyzed as well as exported. While it doesn't include the user that initiated a change or the exact time that a change occurred, it is unrivaled in demonstrating every single change that occurred in Active Directory between the two backup times.
Learn more about Active Directory backup and recovery and Active Directory auditing.