One of the first items KACE administrators look at during the initial setup is Inventory. Everyone wants to see the details on what they have on their network and run reports to start managing the lifecycle of their devices, software, licenses, patching, etc… This is a great place to start, seeing the data pulled in from the KACE agent, and KACE agentless technology, gives administrators visibility to make decisions with quantifiable data to back up those decisions.
This blog post isn’t about that, this is about the ‘one off’s’ or ‘need to know now!’ situations. Below is an example, hopefully you can see how this type of inventory data can be used in many different scenarios.
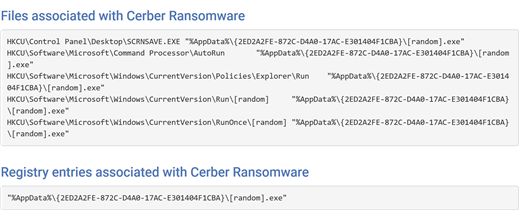
One of the biggest fears, and unknowns for Admins, is the presence of a virus/malware on the network. Many zero-day virus' remain undetected beyond zero day. In fact, the team at Target discovered their hack on a “hunch.” Someone just had a feeling in their gut they were compromised. If we look at the Cerber ransomware attack as an example, we know early on the AV companies quickly reversed engineered the attack. They found an published registry keys, files, file locations to their websites so their customers, and the world, knew where to look to see if they had been infected.
Below is the type of information your AV company will publish on Day 0. What they generally don’t publish is the identity (IDE, signature files etc..) to protect your systems. Hence the term Zero Day.
So what is an Administrator to do? Unplugged the network until my AV company releases an update? Rely on my AV company’s behavioral detection?
What I'm getting at here is defense in depth, the standard for protecting your networks through layers of defense. KACE should be, and can be, a layer in your defense strategy and here's how. By using the example above, we can run a KACE Custom Inventory Rule to ask the KACE agent to query the enterprise to see if any systems have the above registry key or files. For detailed instructions, see your admin guide.
As you can see from the screenshot below, KACE can find anything you ask it to. I really like shellcommadtextreturn for other adhoc reporting across Windows MAC and Linux. To create reports simply create a label to group the systems together.
In summary, the next time a manager, CSO, or CIO asks, "Are we sure we haven’t been infected? How do you know?" A good answer is, "Yes, and I have confirmed this through multiple sources (my layers of defense)."