In today's world, you need to be aware of where your company's sensitive data is located.
Why do you need to do this?
Because otherwise, you must protect everything within your environment to a very high level. This wastes valuable resources and increases the time and effort involved with finding breaches within the organization. If you know where the sensitive information is, then you can concentrate your resources on these locations and apply a lower security policy to the non-sensitive data.
Think of it this way: If you live on a river and there is a 2-mile section with a very high risk of flooding, does it make sense to build a low wall along 100 miles of the riverbanks on either side of this section, or build very strong defenses just for the section at risk?
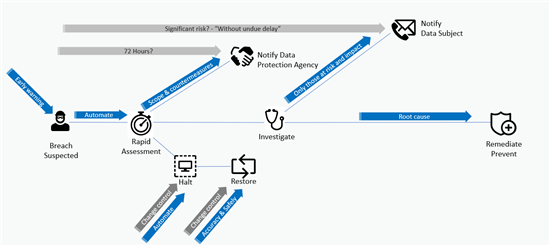
Develop a breach notification process
As part of your content security policy, you should also develop your breach notification process.
Below is a good basis to start, but this should always reflect your business requirements:
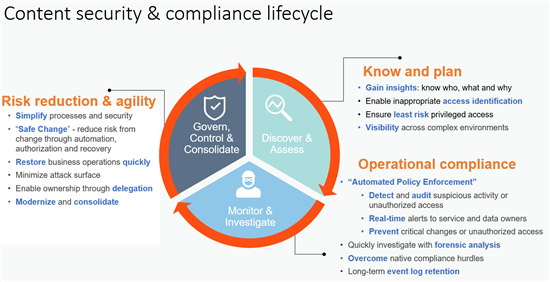
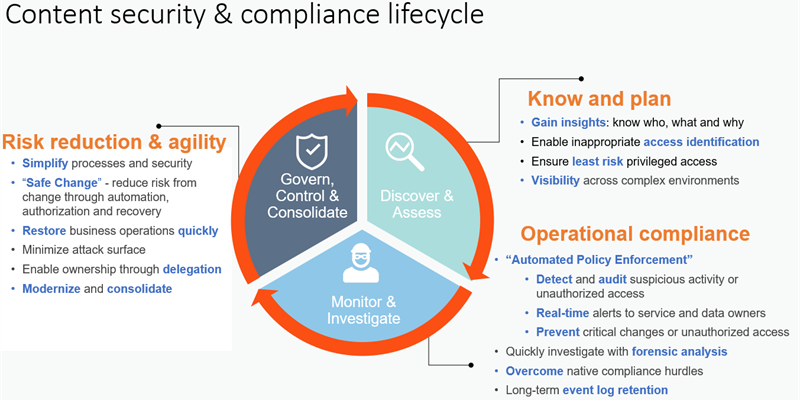
How to protect your sensitive information
Understand your risks, identify systems which contain sensitive data and make appropriate decisions on how to ensure that the content is secure. You should perform PIA (Privacy Impact Assessments) across all the systems that you run, as these will determine which systems have sensitive data and therefore need further investigation.
This model is a good place to start once you have processed the PIAs to then understand what the content is and where it resides:
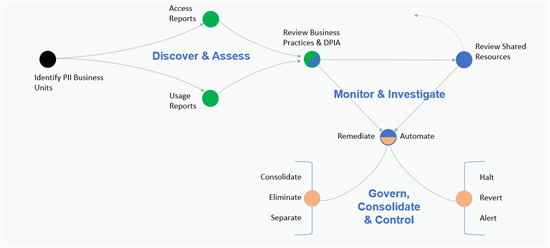
Once you understand the location of the sensitive data, use the appropriate model to reduce the risk:
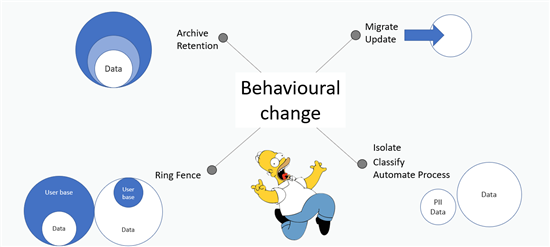
From this point we have made the discovery, implemented the behavioral change, and now it is a case of cycling through this process to check for new systems, updating/removing obsolete environments and monitoring your sensitive areas: