Quest InTrust is a very powerful log management framework which also contains a lot of possible ways to notify about triggered alerts:
- Email alerts
- SCOM connector
- Alert Reports in SRS
- Alerts in SQL DB
- Web Interface for Alert management - InTrust Monitoring Console
With latest 11.4.1 Update 1 we've added one more - Event Log notifications, which also means integrating security alerts into SIEM
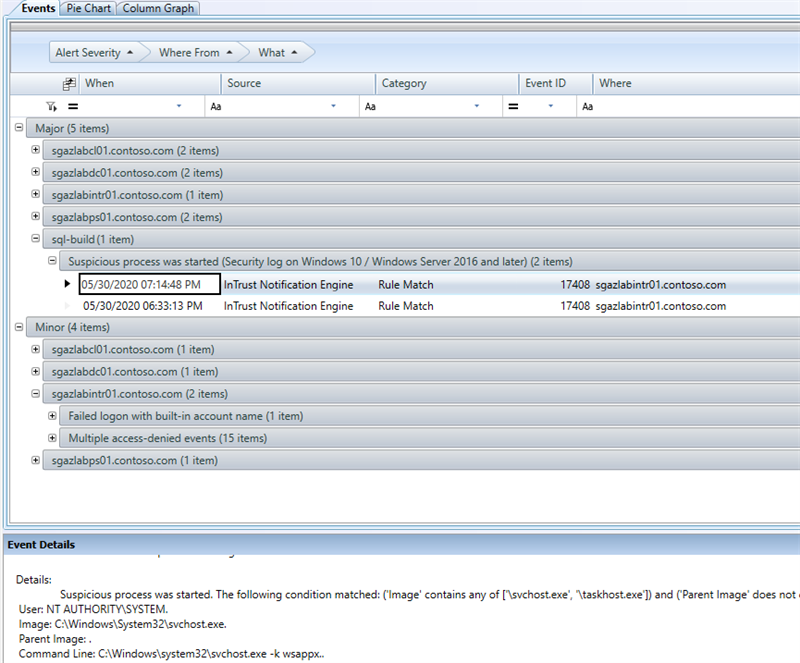
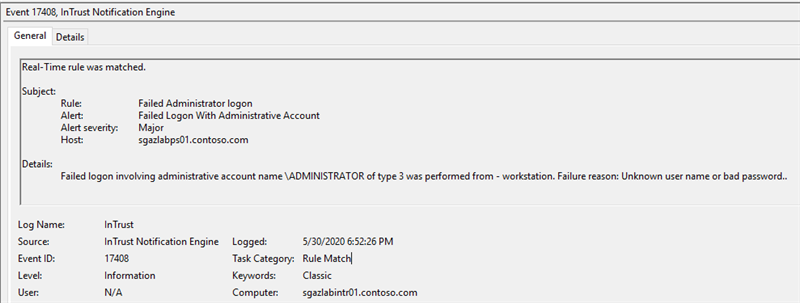
Once an alert is triggered, InTrust will create an event in the InTrust Server event log
Contents of the event can be modified in a couple of ways: modify the alert text or modify the event notification text. To add a notification you need to do the following:
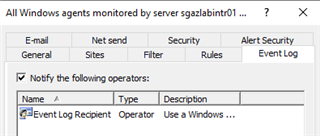
Add event log to the corresponding notification channel of the real-time monitoring policy
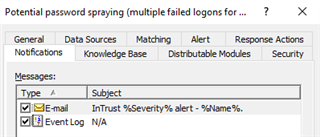
In the real-time monitoring rule configuration, add event log notification and modify the text if necessary and make sure the rule is enabled, the policy is enabled and site for the policy contains target computers
Here is the event example
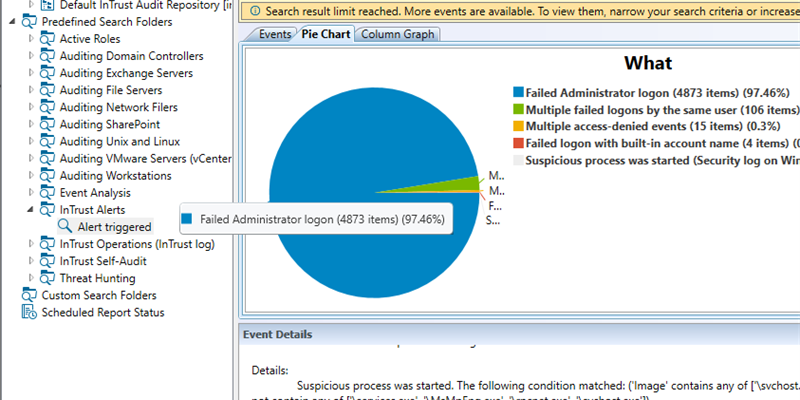
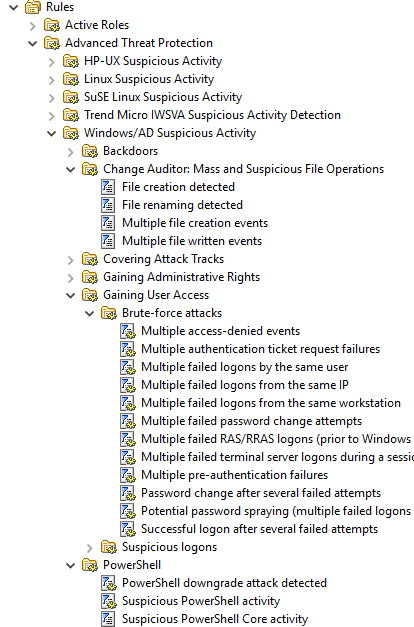
You can use the library of pre-built security and operations alerts to get notified via event log
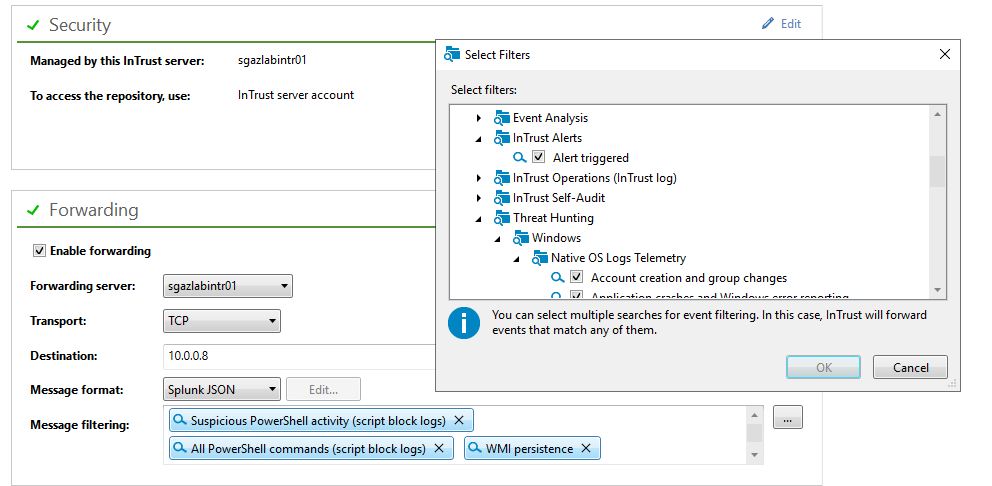
Because InTrust is a framework, you can use it to collect this log and forward alert notifications to SIEM, here is how it can be configured in the InTrust Deployment Manager.
Make sure real-time log collection is collecting the InTrust Server Log

Specify InTrust Alerts as a forwarding filter if there is another filter already (if you are forwarding everything - all events including alerts will be sent)
To help our customers batch-enable all event rules with the new notification action we've released a special support tool
When collected InTrust server event log with alert notifications can be used in Repository Viewer to see and investigate alerts