If managing Windows permissions is like driving a car, would you rather have a stick shift or an automatic transmission?
A stick shift is cool, and it makes you feel like a teenager again. Kind of like the Microsoft security tools you get inside Windows. “Looks like the guys in Finance are having trouble with inherited permissions,” you tell your colleagues importantly. “I’ll run subinacl on a few servers and find the problem.” Using those command-line tools reminds you that it’s cool to be an admin.
But like a stick shift, those tools can get to you when you’re in stop-and-go traffic, as you grind away your morning, then your afternoon, then your evening trying to track down and fix NTFS permissions, Windows file permissions and Windows folder permissions. After a few hours, you tell yourself it would be nice to have an automatic transmission – a nice Windows permissions tool for locating and managing access control, specifically in bulk across your whole environment.
Security Explorer – Managing Windows permissions with an automatic transmission
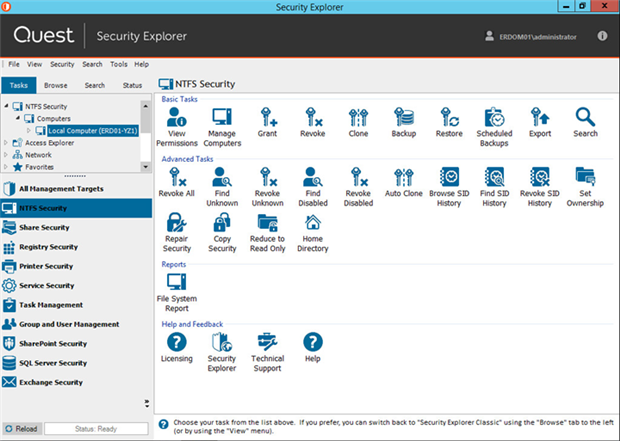
We’ve built Security Explorer like an automatic transmission for managing permissions all across your Windows network, as shown below:
As I mentioned in my post about managing Windows permissions from a single console, you can find and manage permissions for your files (NTFS permissions and Windows file permissions), shares, registry, printers, services, tasks, groups/users, SharePoint, SQL Server and Exchange Servers.
File and print servers: Manage security on NTFS, file/folder shares
No more stick shift (unless you want it).
Built-in utilities like Windows Explorer and command-line tools like icacls, xcacls and subinacl let you open multiple property windows to drill into, view and change permissions. And you can use those tools to make changes in bulk, such as granting, revoking or cloning access across multiple directories, or searching for access assigned to a user or group.
But they are effective only at the most granular level. They still have many limitations: they work on only one machine at a time, they do not account for group membership when searching, and they work only on NTFS permissions, not on share, registry or printer permissions.
And, they work only on Windows servers.
From the purely graphical UI of Security Explorer, you can manage access to Windows Servers, desktops and NAS/SAN devices, and manage permissions on NTFS, shares, Registry, printers, services and tasks. You can work across multiple servers, desktop machines and certain NAS/SAN devices at one time.
Services and tasks: Search and modify
One of the most popular features in Security Explorer is its ability to centrally manage service and task settings across the network – on both servers and workstations.
Whenever a service account password is changed, that password must be updated for all services and tasks that it is assigned across the network. Windows does not provide a way to do that without updating each affected computer.
Security Explorer can centrally search for services and tasks based on relevant criteria. Once you’ve identified a group of services or tasks, you can change properties such as logon name or account password on a large number of computers by selecting the services/tasks and choosing Properties.
Local Users and Groups
Do you know how many headaches you could save yourself by removing user admin rights? How about 94 percent of them?
User admin rights make even small breaches dangerous. With Security Explorer, you can search globally for local user accounts, including all accounts with user administrative rights. Then, you can easily change the account passwords, rename the accounts, change group membership settings and manage other account properties across the network in one operation.
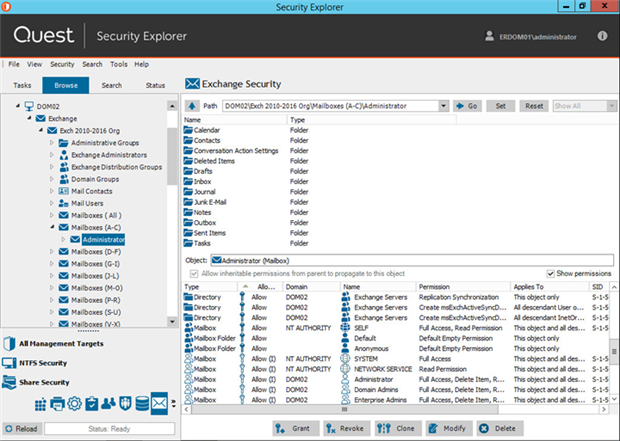
Exchange: Manage Exchange and related Active Directory permissions
Security Explorer lets you find, manage and report on permissions for Exchange objects like mailboxes and mailbox folders. Here’s a view of all the Exchange objects associated with the Administrator account:
You can make changes to access control directly from the UI, which means you don’t need to manage Exchange security in Active Directory and on the mailbox folders stored on each Outlook client. You can also get along without a handful of other tools like Exchange Management Console, Exchange Management Shell, Active Directory Users and Computers (ADUC), Public Folder Management Console and utilities in Outlook.
Unless you’re into that whole stick shift thing.
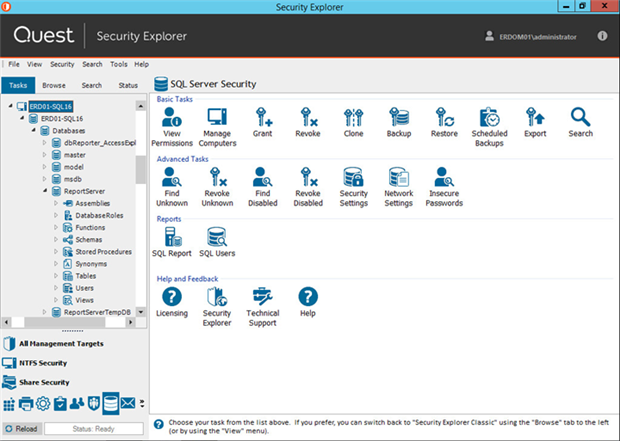
SQL Server: Assess, manage and improve security
And speaking of stick shift, how quickly can you verify the integrity of an SQL Server and certify that it is compliant? That includes making sure you know exactly who has fixed server roles like sysadmin, serveradmin, securityadmin and processadmin.
How easily can you find the SQL user accounts with blank or insecure passwords? Display the security level of all SQL objects? Find all of the locations to which a given user or group has access? Security Explorer makes tasks like those a lot easier:
The thing about SQL Server is that its security model has multiple levels of nesting. SQL logins can be linked to local or domain accounts, or to integrated SQL accounts. Database users are then linked to SQL logins. Next, database users can be granted direct access to database objects, or they can be associated with a database/server role, which in turn is granted access. Finally, access can be granted to stored procedures or directly to the underlying tables, schemas and views.
The whole thing is just crying for an automatic transmission.
Security Explorer exposes SQL Server security in a way that is easy for non-DBA admins to understand, when they need to quickly find and lock down access to SQL resources.
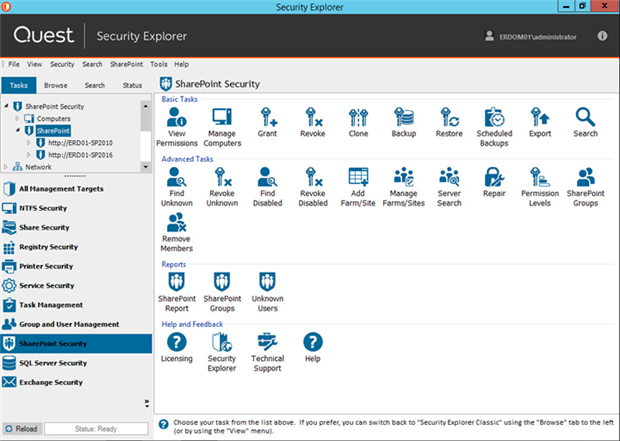
SharePoint: Control groups and permission levels
If you can manage SharePoint security with a stick shift, then be my guest.
From a single console, Security Explorer lets you identify all SharePoint sites and centrally manage security and group memberships on them. You can manage better and faster when you’re not waiting for SharePoint web pages to refresh.
In my next blog post, we review 4 tasks we've automated for you with Security Explorer.
Your turn
Ready to take the automatic transmission for a test drive? Download the 30-day trial version of Security Explorer and see how easily you can manage Windows permissions for servers, users and groups everywhere in your organization.