The Application User Interface is simply Role Based Access control to the Function and Features of the Change Auditor when using client, it restricts access to the client interface based on permission, it is also known as User Interface Authorization.
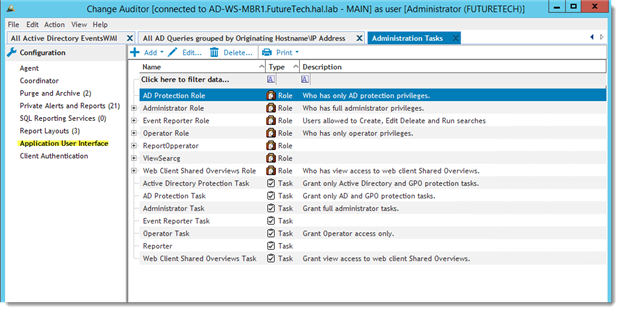
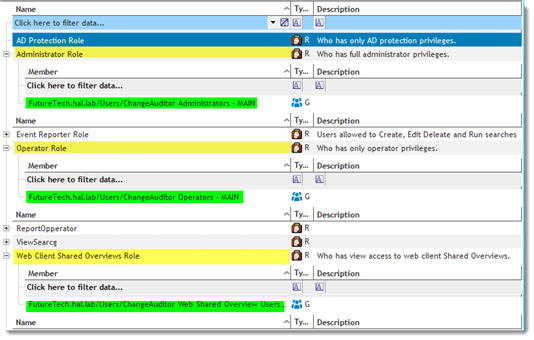
The User Interface Authorization structure is made up of three objects, Operation, Task and Role. The user functions of Change Auditor are subdivided into smaller parts called Operations, examples of these are “Enable Report”, “Disable Report, and Edit Report”. Many related “Operations” can be combined to create a “Task”, for example, a Task called “Report Operator” may be created with Enable, Disable and Edit Report operations because they are related. If one or more Task is assigned to a user or Group of users and given a name, a “Role” is created. Please see links at the end of this document for instructions on creating Tasks and Roles.
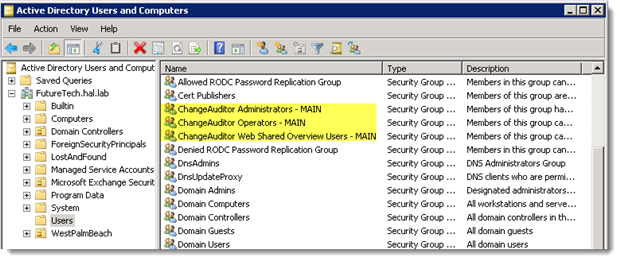
AD Protection, Administrator, Operator and Web Client Shared Overviews Roles are inherent or built-in to this user interface. During installation ChangeAuditor Administrators, ChangeAuditor Operators and ChangeAuditor Web Shared Overview groups are created in Active Directory and added to the respective roles in the Application User Interface.
At the core of the Application User interface is the Authorization Manager RBAC Framework. This role-based management model enables administrators to assign users to roles and provides a central location to record permissions assigned to each role.
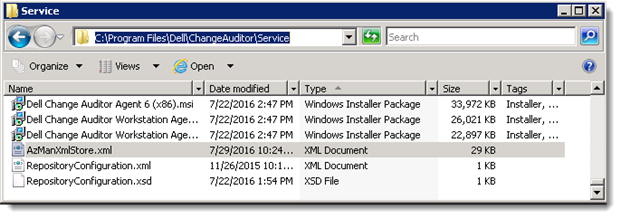
The permission settings in the User Interface Authorization are called Authorization policies, and are stored in the Authorization Policy Store. Change Auditor uses a local XML file store called AzManXmlStore.xml located in the installation path of the Coordinator.
Another object found in the User Interface Authorization section is the Application Group, Application Groups are associated with the Authorization Manager and are specific to an application, in this case to Change Auditor.
Application groups are typically stored with the Authorization Policies in the Policy Store, the significance of this group is that an Administrator in the User Interface, does not necessarily need to be a domain administrator to create this group, they only need access to the Policy Store.
It is possible for this store to become corrupt causing the permission to work incorrectly to the point of preventing access to Change Auditor. At this point it may be necessary to create a new store by renaming the current AzManXmlStore.xml and running a repair on the Coordinator in Programs and Features of the Control Panel, this will create a new file with only the default Policies.
Another option would be to edit the AzManXmlStore.xml file using the Authorization Manager Microsoft Management Console (MMC) Snap-in.
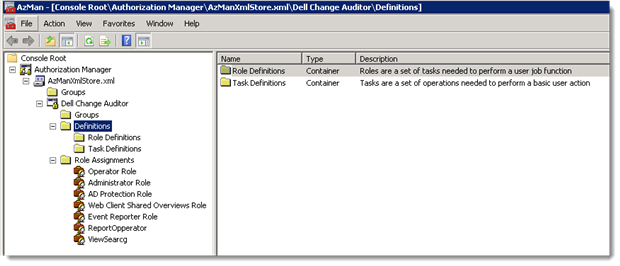
Used cautiously and with the correct knowledge, the Authorization Manager MMC Snap-in can be used to create or repair policies external to the Change Auditor Application User interface.
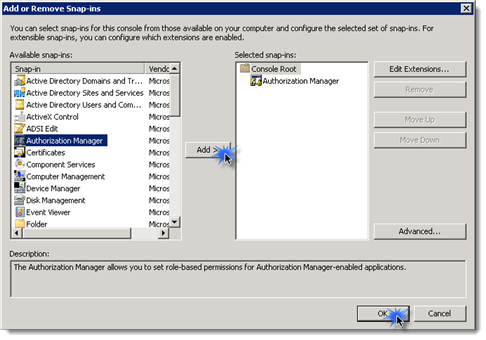
To run the Authorization Manager execute mmc.exe and select “Add/Remove Snap-in” from the file menu, select the “Authorization Manager” snap-in and click “Add” | “Ok"
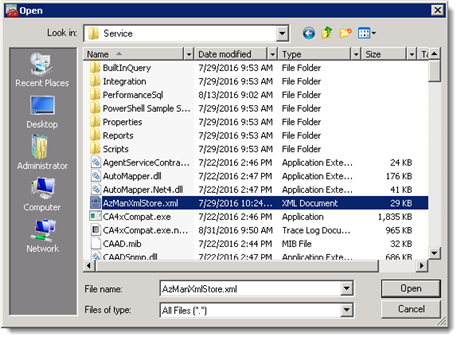
To load the AzManXmlStore.xml file select “Open" from the file menu and select the file.
All the policies configured in the Change Auditor Application User Interface should be visible in the XML store. In a multi-Forrest/Coordinator environment each Policy Store is unique to each Coordinator and is not synchronized across Coordinators.
CAUTION:
The AzManXmlStore.xml file is locked to other user when the first user opens it with the MMC snap-in or Change Auditor client. Improper changes to this file can lead to irreversible corruption.
Additional reading:



