From Foglight version 6.3 onwards a lot of development has gone into updating the security of Foglight, that could be upgrading various components to the latest versions but also ensuring the agents negotiate the highest security protocols when connecting to, for example, SQL Server.
This means that certain protocols are disabled in the Foglight agent config, which is good news.
The example I found was TLS. TLS stands for Transport Layer Security, a cryptographic protocol that encrypts data in transit between computers and servers. There is a file stored in the agent manager folders called java.security.
On an external Fglam this would be {fglam}\jre\{version}\jre\conf\security\ (JRE 17) depending on the version of JRE.
In this file you would find a list of disabled algorithms:
jdk.tls.disabledAlgorithms=SSLv3, TLSv1, TLSv1.1, RC4, DES, MD5withRSA, \
DH keySize < 1024, EC keySize < 224, 3DES_EDE_CBC, anon, NULL \
However, in an ideal world and if you are a DBA, you are aware of this and well ahead of the game, you have upgraded all your SQL instances to SQL Server 2016 and above and support TLS 1.2.
But we don’t live in an ideal world and there maybe various reasons why you still operate systems on SQL Server 2008/R2, 2012, and 2014.
There is some useful information here from Microsoft:
This article provides information about the updates that Microsoft releases to enable TLS 1.2 support for SQL Server 2017 on Windows, SQL Server 2016, SQL Server 2014, SQL Server 2012, SQL Server 2008, and SQL Server 2008 R2. This article also lists supported client providers. SQL Server 2016, SQL Server 2017, and SQL Server 2019 support TLS 1.2 without the need for an update.
Several known vulnerabilities have been reported against Secure Sockets Layer (SSL) and earlier versions of Transport Layer Security (TLS). We recommend that you upgrade to TLS 1.2 for secure communication.
The reason for this blog is that if you upgrade Foglight you might suddenly find your agents cannot connect to your older SQL Server versions, and yes ideally you will retire your older SQL Servers or apply update patches, but that takes times.
What do the errors look like:
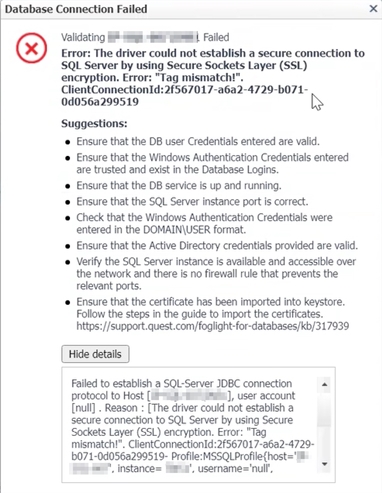
Agent Manager Log:
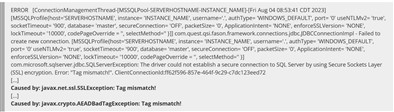

So how can we help? Well basically remove the disallowed protocols from your java.security file.
If you also are unfortunate to still have to support SQL Server 2005 then 3DES_EDE_CBC will also be required to be removed.
ORIGINAL:
jdk.tls.disabledAlgorithms=SSLv3, TLSv1, TLSv1.1, RC4, DES, MD5withRSA, \
DH keySize < 1024, EC keySize < 224, 3DES_EDE_CBC, anon, NULL, \
include jdk.disabled.namedCurves
UPDATED:
jdk.tls.disabledAlgorithms=SSLv3, RC4, DES, MD5withRSA, \
DH keySize < 1024, EC keySize < 224, anon, NULL, \
include jdk.disabled.namedCurves
Then restart your Foglight Agent Manager.
Regarding best practices as per OpenJDK developers (outside of Quest) the workaround is not advisable in production environments since using disabled algorithms degrades the secure communication between the FglAM and the host servers provided the newer algorithms. But as mentioned this might not be a choice.
Another approach is to create another Foglight Agent Manager for your older instances, along with the updated security file and move the agents for these older instances to that agent manager. If you keep the disallowed protocols in your existing agent managers, this will ensure instances that support TLS1.2 will continue to use it.
There are also further considerations if using TLS1.3 relating to supported versions of Windows, such as Windows Server 2019
Further reading:
https://support.quest.com/foglight/kb/4372619/error-tag-mismatch-on-db_sql_server-agent-logs-after-upgrade
https://support.quest.com/foglight/kb/4310338/the-server-selected-protocol-version-tls10-is-not-accepted-by-client-preferences-tls12
https://support.quest.com/technical-documents/foglight/7.1.0/security-and-compliance-guide/8#TOPIC-2071776


