Managing software assets in a distributed environment isn’t easy. Between compliance requirements, license costs, and security threats, IT teams need reliable tools to stay ahead. That’s where the KACE Systems Management Appliance (SMA) shines—especially through its comprehensive Software Catalog.
Let’s explore how the KACE SMA Software Catalog works under the hood, and how it can directly impact your bottom line and security posture.
What Is the KACE Software Catalog?
At its core, the Software Catalog is a normalized, curated list of software titles that the KACE SMA uses to interpret raw inventory data from endpoints. It distinguishes between:
* Installations (based on file signatures, registry entries, and uninstall keys)
* Recognized software titles (as matched by KACE’s internal catalog)
* Unrecognized or custom apps (for which you can create your own definitions)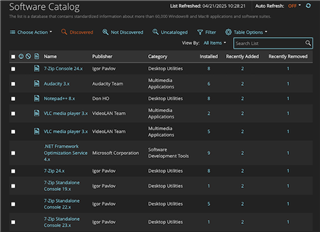
Using the Software Catalog to Save Money
1. Find and Remove Unused Software
With KACE, you can create smart labels or reports to identify software that is installed but never used—especially helpful for expensive, licensed apps.
Use Case:
You find 30 installations of a licensed design tool, but usage data shows only 10 regular users. That’s potentially $15,000+ in savings just by reclaiming licenses.
2. License Optimization
Tie software inventory to your procurement data. The Software Catalog helps you see which license models are in play and match them against actual endpoint data.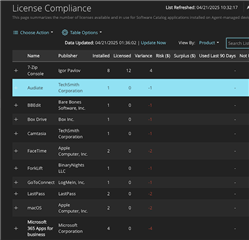
Tip: Pair the Software Catalog with the Asset Management module to track license entitlements and expiration dates.
3. Avoid Redundancy
When different departments install overlapping tools (e.g., multiple PDF editors), it leads to license bloat and more support complexity.
Action: Standardize on a single solution and remove the others using managed uninstalls via scripting.
Strengthening Security with Catalog Intelligence
1. Identify Unauthorized Software (Shadow IT)
The catalog flags any unknown or non-approved software. You can set up notifications or auto-labeling to flag such apps for removal or review.
Bonus: Use the Service Desk integration to generate a ticket automatically when unapproved or blocked software is detected.
2. Track Vulnerable Versions
The Software Catalog, especially when paired with KACE’s patching and custom inventory rules, helps identify outdated or vulnerable versions of critical apps.
Result: Focus your patching efforts where the risk is highest.
3. Audit Readiness
Whether you're prepping for a license audit or validating security compliance, the Software Catalog provides a single source of truth. It’s especially useful when answering questions like:
* How many installs of Product X do we have?
* Which endpoints are running unpatched versions?
* Are there rogue applications in the environment?
Pro Tips
* Enable Software Metering: Get visibility into app usage, not just presence.
* Use Custom Inventory Rules: Extend catalog capabilities to include in-house or less-common software.
* Integrate with Asset Management: Track purchase history, expiration, and usage in one place.
Wrap-Up
The KACE SMA Software Catalog is an essential component for both cost control and cybersecurity. With precise visibility into what's installed and how it's used, IT can make smarter decisions, faster.
Ready to make the most of your software inventory? Dive into the Software Catalog and start tagging, labeling, and cleaning up today.
- 製品情報
- ソリューション
- サービス
- サポート
- トライアル
- パートナー
- コミュニティ



