Hi,
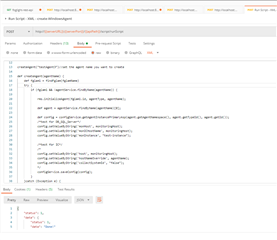
I have created a custom rest api to add a SQL instance to Foglight. I am doing a post call and within the api code are the internal function function calls that work on the installer. I am hitting a few hurdles on the way and seek some help if possible
1) The API code is able to register and create the agents both the DB_SQL_SERVER and the associated spi but then errors out with message - "VERBOSE [http-exec-51] script.system:dbwc_mssql_installer.monitorInstances - com.quest.qsi.fason.framework.installer.exceptions.InstallerServiceException: Could not create agent DB_SQL_Server on FglAM xxx: Not authorized to manage agents". Soon after it unregisters those agents.
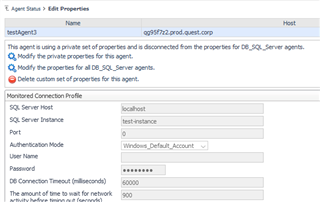
2) If I try to enable OS monitoring, my API code fails with error - no credentials found for host xxxx. I think I am unable to populate credentialIDs for DBSS_Installer_OS_Credential topology object correctly in the code.
<type name='DBSS_Installer_OS_Credential' extends='DataObject'>
<annotation name='Keywords' value='DB_SQL_Server'/>
<property name='credentialIDs' type='String' is-many='true' is-containment='false'/>
<property name='lockboxPassword' type='String' is-many='false' is-containment='false'/>
<property name='osUserName' type='String' is-many='false' is-containment='false'/>
<property name='osPassword' type='String' is-many='false' is-containment='false'/>
<property name='authenticationMode' type='DBSS_Installer_DB_Authentication_Mode' is-many='false' is-containment='false'/>
</type>
Thanks