Hello,
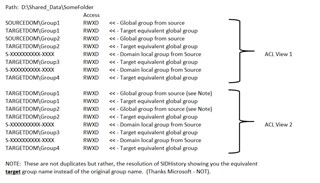
Post inter-forest migration, source user objects migrated in target domain along with sidhistory and those source user objects were deleted. Source group objects were copied in target domain along with sidhistory. Most of the resource have been migrated on file servers in target domain. Most of those resources have domain local groups(source domain groups) applied on ACL. Target domain global groups (containing target domain user objects) are nested inside domain local groups(source domain groups).
1. While resource processing, do I need to remove global groups(target domain) from domain local groups(source domain) and append it on resource ACL? Resource process to append or replace is only applicable on resource ACL?
2. Is this mandatory to add target users to source groups in resource processing? Can I perform both (add target users keeping source users intact) as well as (replace source users with target users) in source groups
Since groups are copied and membership of those groups are also populated with target users which were already migrated, as an alternative is this possible to apply/add target groups on security descriptors(SD) instead of adding target users to source groups?
3. Can I also run ADPW against target domain? If yes, then what are possible scenarios where ADPW should be used against target domain?
4. What are other tasks for performing resource processing as per my above mentioned situation?
Thanks & Regards,
Shawn Douglas