Quest InTrust 11.3.2 maintenance release happened last week. One of the main features is improved and expanded support for Linux OS. Let me focus on this topic and provide some details about how InTrust can be used to setup truly centralized and feature-rich log management for Linux OS.
In a modern Hybrid Active Directory infrastructure majority of services, servers and workstations are windows based, but there are still some application which are using another platforms, some applications such as cloud platforms for developing and testing applications may not be windows as well. InTrust is well prepared to collect event log information from all popular platforms you may see in the wild. For this particular post we will focus on Linux platforms, but more or less the same is true for other UNIX-like systems.
Linux OS Family
Linux is popular as a server and cloud operating system, as a container platform and among vendors distributing solutions as virtual appliances. Sometimes among hardware vendors as well and software vendors who need highly customizable OS for their software. Linux has variety of distributions and different versions which can suit any specific need, some vendors choose to develop and contribute to the OS they are distributing their applications for.
Some Linux distributions such as Ubuntu became popular enough as a workstation OS as well (12% according to 2016 Stack Overflow survey)
To perform log management and monitoring, InTrust agent can be deployed on the following Linux distributions
 |
 |
 |
 |
 |
| SUSE Linux Enterprise Server | Oracle Linux | Red Hat Enterprise Linux | Debian | Ubuntu |
How log mangement for Linux OS works
Please, check Installation manual for more detailed information on how to install an InTrust agent on Linux OS.
The agent has been pre-compiled for the correct Linux OS and architecture and can be deployed easily by running the installation script. The script contains binary components which will be installed in a form of a daemon and supporting tools. The script also creates init scripts and configuration necessary to intercept Syslog messages
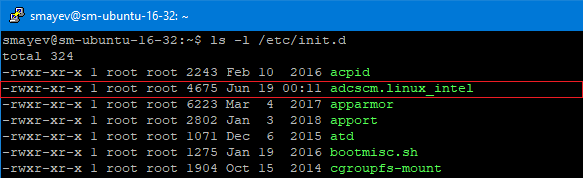
The agent will intercept all events sent to a syslog or rsyslog daemon, processes them according to real-time monitoring rules and compresses for future delivery to the InTrust server in accordance with the corresponding event log gathering schedule
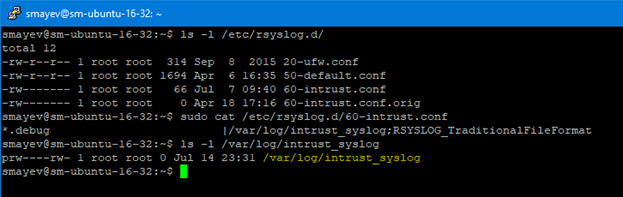
Keep in mind that InTrust agent installation is non-intrusive for the existing configuration, so if you need to disable file-based logging because you are sending everything to InTrust – you need to do this manually. In the example above you will need to remove 20-ufw.conf and 50-default.conf from /etc/rsyslog.d
Simplified event flow chart in the Linux OS with deployed InTrust log management agent:
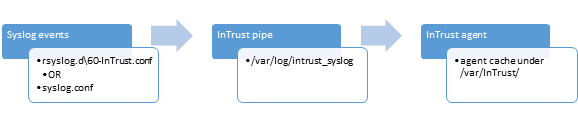
InTrust agent compresses event log data with highly efficient 20:1 compression ratio and then once instructed by the server uploads compressed and encrypted logs thus significantly reducing network traffic from agent to server. It’s close to 20:1 reduction compared to native even log forwarding traffic such as syslog
Centralized Log and Monitoring Management
Once Linux agent is deployed, each Linux and UNIX computer can be centrally managed via the InTrust server.
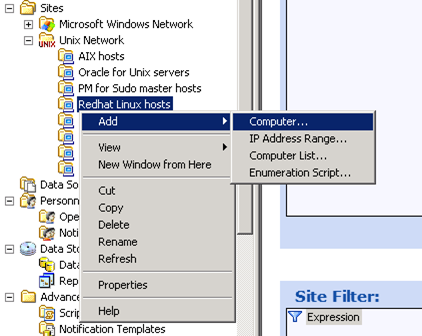
When agent is registered it can be seen under the Agents node
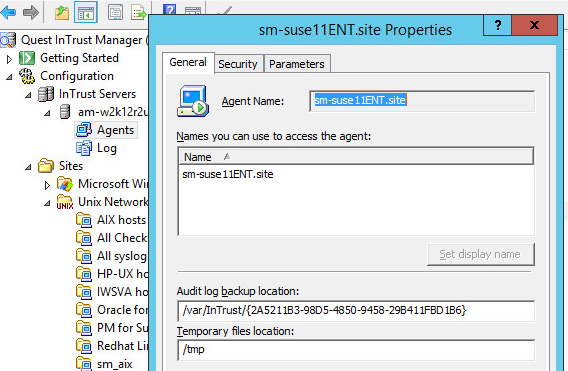
Now an agent can be added to a site (special group of computers for which you can assign policies)
There are several pre-defined datasources which define how InTrust agent collects and processes the data on the Linux agent.
Syslog events gathering
Syslog datasource is very powerful and contains pre-defined rules for parsing some known event log entries, such as logons and sudo usage. You can add custom parsing rules as well. You need to specify Regular Expression query and assign extracted values to the corresponding well-known event field or use Insertion Strings if necessary.
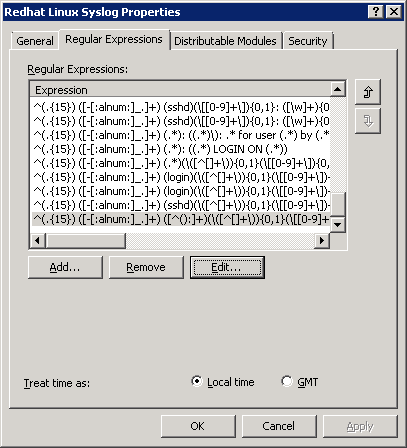
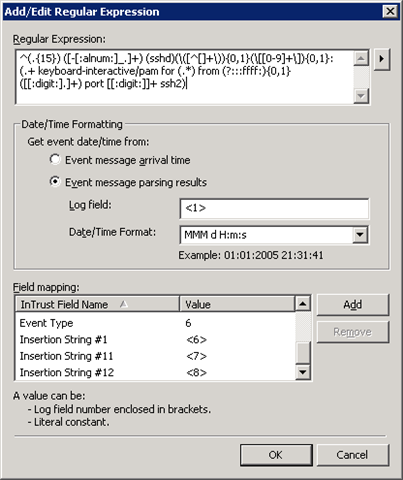
To make your desired changes non-intrusive for the original InTrust configuration, you can setup another datasource by copying the original one, then you can modify it and switch the datasource in the event log gathering job.
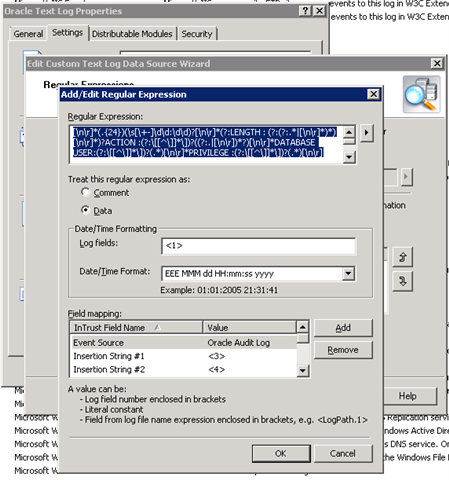
Text log file event gathering
Custom Text log file provider can be used to collect any event from any log file which exists on the Linux OS agent. You can check Oracle audit log datasource as an example of log management for file-based event logs. As you can see you have very powerful InTrust parsing framework which can be customized and targeted to a different sites with different number of Linux OS agents
Configuration files Integrity monitoring
Configuration file integrity monitoring datasource can be used to monitor integrity of *.conf files or virtually any other file in the Linux or UNIX OS. There are couple of datasources (one generic with predefined syslog.conf file monitoring and another one user and group management monitoring) with preconfigured gathering jobs (to keep records of every change) and with pre-defined alert rules to catch the unwanted actions
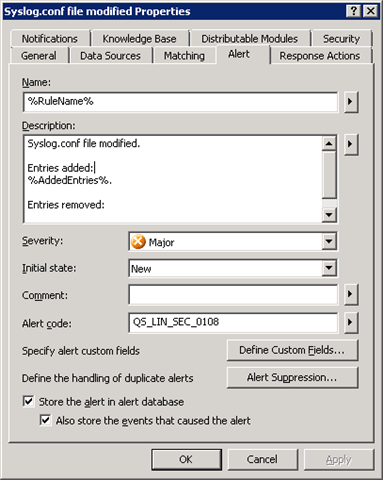
To enable the InTrust event log monitoring rule – make sure it’s enabled in rule’s properties. And that the corresponding monitoring policy is active and target site contains desired Linux OS agents
Summary
InTrust can be very efficiently used to perform centralized log management for broad versions of Linux OS distributions. It has highly efficient, secure and reliable even log gathering with reduced network traffic throughput requirements as well as monitoring engine to perform file integrity monitoring, which can generate alerts and perform response actions. Actually, such response actions could orchestrate Linux OS management tasks and perform issue remediation.
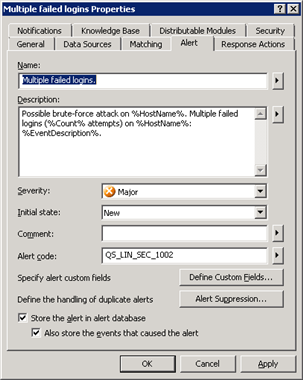
Centralized log management server allows easy deployment of new monitoring alert rules and event log parsing patterns for any number of connected Linux agents. And for both syslog event flow and text-based log files.
You can specify different sites for Linux agents, assign more detailed, stricter log management and monitoring policies for sites with more critical machines, after that configuration will be automatically delivered to the endpoints.
You can take your Linux environment under full control and bring all the spread-out log sources into a single repository and create unified monitoring and log management rules and policies for your heterogeneous Linux and UNIX environment.
What to know more about InTrust? Check our cool videos about InTrust beeing used alongside Change Auditor to protect agains ransomware and on how you can enable InTrust to protect agains PowerShell-based attacks


