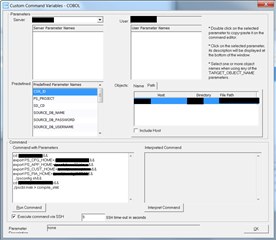
Is it possible to add a feature to the custom command post migration set-up that would restrict users from changing the variables defined in the custom command. We restrict our end users from using the UNIX account that allows the ability to SSH. If we define a custom command the user can put any command in the "command with parameters" window and compromise our server after selecting the run button during the post migration process. We would like the ability to define the command but only allow the end user to execute the custom post migration as-is, preventing the user from adding or changing these variables.
This is a great feature but completely useless for us because of this security concern.