Change Auditor’s much anticipated 7.1 release is here – and we’re excited. Change Auditor’s capabilities give customers the peace of mind they deserve, and the latest release further expands on these capabilities with new features added to Change Auditor for Logon Activity.
Change Auditor for Logon Activity allows you to promote better security, auditing and compliance in your organization by capturing, alerting and reporting on all AD logon/logoff and Azure AD sign-in activity. With the 7.1 release, logon activity auditing includes the following capabilities:
- Auditing of successful and failed Kerberos authentications
- Auditing of successful and failed NTLM authentications
- Capturing the version of NTLM, to help identify applications using older versions of the protocol
- Detecting potential Golden Ticket use
So, how do these new features benefit you?
Let’s dive in.
Golden Ticket Detection
Change Auditor for Logon Activity audits anytime a user or application authenticates to the AD domain using Kerberos or NTLM. Bad actors create a Golden Ticket, which allows them to impersonate a privileged user without being detected. A Golden Ticket, also called Pass-the-Ticket, is one of the few well-known Kerberos vulnerabilities, so letting them go unchecked could spell disaster.
With the 7.1 release, now you can quickly audit and alert Kerberos tickets with lifetimes that exceed the domain policy, which could indicate a potential Golden Ticket attack.
No More NTLM Worries
Many organizations want to get rid of NTLM authentication, and we can’t exactly blame them. NTLM authentication – which comes in two versions – is pretty weak and can leave a lot of gaps in your security. Unfortunately, there are applications that still use it, so being able to properly audit NTLM events is critical.
Change Auditor 7.1 allows you to detect applications utilizing NTLM authentication and see what version they have (NTLM 1 vs. NTLM 2), which will help you cover any potential gaps down the road.
Quest On Demand Audit Integration
As you may know, On Demand Audit is our Azure-hosted SaaS that provides visibility and insight into all configuration, user and administrator changes made across AD, Azure AD and Office 365. With it, you can quickly investigate incidents with responsive search and interactive data visualization, and store audit history for up to 10 years in the Quest On Demand tenant.
With the release of 7.1, Change Auditor now integrates with the On Demand Audit Hybrid Suite for Office 365 to view all AD logons/logoffs, Azure AD sign-ins and Office 365 activity together. This means you can view all activity, authentications and alerts in a simple, clean dashboard – which makes security a lot more efficient.
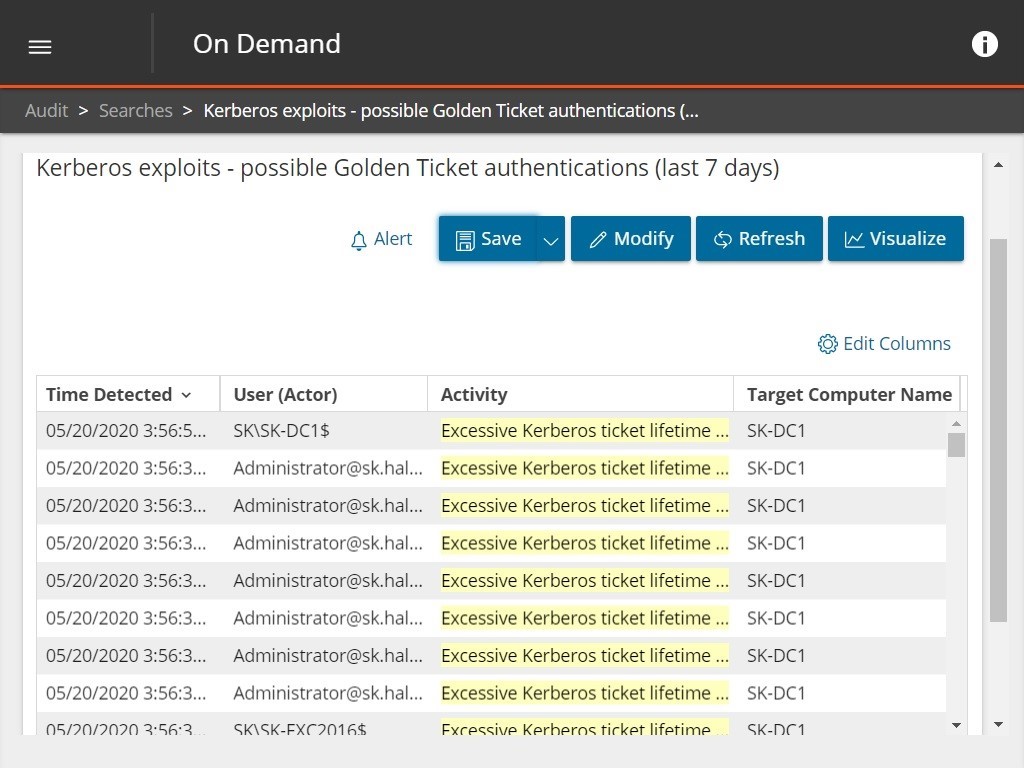
Here you can see an example of how you can identify potential Kerberos exploits by searching for all cases of excessive Kerberos ticket lifetime.
Check out this video and see how On Demand Audit helps you keep track of everything without overwhelming you.


