During recent conversations with our Quest® Customer Advisory Board, one security team leader said “we don’t want a lot – we want it all” with regard to which security logs they needed to be able to collect and analyze. That’s smart thinking today. Hackers are getting more sophisticated by the minute coming up with new ways to breach your network and compromise privileged accounts. If you want the ability to thoroughly investigate incidents, if you need IT forensics for any situation, and if you want to ace compliance reviews, then you need to collect every log with security value.
Most organizations we meet with rely heavily on SIEM tools to collect, correlate and analyze log data from a variety of systems across the entire IT infrastructure to identify and report on security threats and suspicious activity. According to the Cybersecurity Insiders 2019 SIEM Report, 86% of organizations are satisfied with the effectiveness of their SIEM platform, which should come as no surprise since SIEM tools really are a key piece to any good, in-depth defense strategy.
But, the 2019 SIEM Report also revealed that 31 percent of organizations are overwhelmed by too many false positive alerts. Using SIEMs to check EVERY log with security value can be overwhelming and costly. Of course, collecting logs is vital to detecting, analyzing and preventing security breaches, but not every log has to be sent through your SIEM.
Gartner recommends using a central log management approach to better manage your existing SIEM solution investment if scaling existing collection and analysis capabilities is not feasible due to budget or architectural constraints. Send the most valuable event logs through your SIEM, and then store the rest in an affordable archive and search repository.
That’s where the new version of InTrust comes to the rescue!
Bridge the gap between compliance and analytics with Quest InTrust
InTrust is truly a unique event log management solution that helps bridge the gap between collecting and storing data long-term for compliance purposes and providing up-to-date events for threat hunting and analytics. Already a long-time leader in native event log management for Windows environments, InTrust now delivers easy and reliable integration with Splunk, QRadar, ArcSight and any other SIEM tools supporting common Syslog formats (RFC 5424, JSON, Snare).
You can store long-term event log data with InTrust, and then use our new pre-built filters to forward only high-value security data to your SIEM to reduce costs, minimize event noise and improve threat- hunting efficiency and effectiveness.
The new InTrust 11.4.1, available for trial download here, now provides a set of event forwarding filters, following best practices from many industry resources.
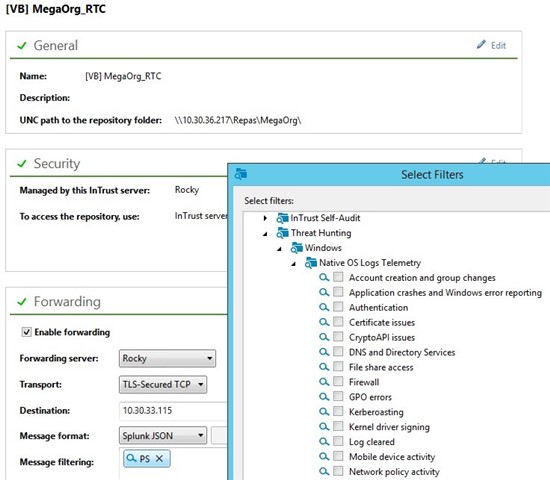
TLS-Secured TCP is also the newest and most preferred transport option to ensure Windows or native event data reliably transfers to your SIEM tool of choice in near-real time.
More importantly, by storing long-term data in InTrust and limiting SIEM data to what’s required for analytics, organizations can save big on licensing costs annually. InTrust’s unique storage technology allows for tens of years of data, indexed and always available. And with InTrust’s predictable per-user license model, you can collect and store as much data as you need in a highly-compressed repository, 20:1 with indexing and 40:1 without, all for a flat fee.
In the end, you can save on storage costs by up to 60 percent, satisfy data retention policies, and ensure continuous compliance with HIPAA, SOX, PCI, FISMA and more.
Check out a webcast on-demand to hear from Microsoft MVP and Windows Security Expert Randy Franklin Smith and Bryan Patton from Quest as they describe, discuss and contrast the different ways you can handle your log data.
You’ll also get a look at how you can send logs to InTrust using the new best practices filters, and learn how Change Auditor can feed high value security events to your SIEM without all the noise of the native logs.

