For those who are unfamiliar with Change Auditor, it is the auditing solution offered by Quest. The solution offers a wide range of auditing capabilities to help provide a view into what changes are occurring within your environment. Unfortunately, the more I interact with my customers, the more I start to realize that very few are using the product to its full potential. I wanted to take some time to inform Change Auditor customers about the functionality within the product that always seems to impresses when shown, but is rarely implemented.
The “ANY” License
One of the features I see overlooked in most implementations are the events contained within the ANY License. First, let me explain how you obtain the “Any” License. By owning ANY module of Change Auditor, you get the “Any” License as part of that purchase. Just to reiterate, as long as you own one module of Change Auditor, you are entitled to the features within the “Any” License.
By filtering on the “Any License” within the Audit Events section you will see all of the different events that are associated with this license. One of the most powerful (and most overlooked) capabilities associated with this license is the ability to audit local computing. The “Any” license provides the ability to deploy agents on ANY member server. Once deployed, you can monitor changes to local groups, users, services as well as registry settings. In addition to the functionality just described, it also provides you the ability to audit VMware related events as well as any changes happening within Change Auditor itself to ensure all changes are tracked.
Figure 1: Event Classes associated with the “Any” License. Note the local computing (groups, users, services and registry) and VMware auditing associated with this license.
Multi-Entity Search
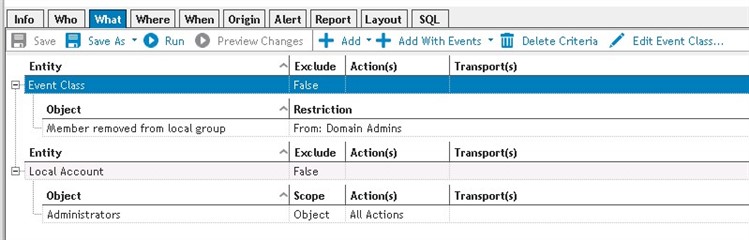
Another aspect often overlooked is the ability to do a “Multi-Entity” Search with Change Auditor. A real-life example of this was a customer wanted to be alerted anytime the Domain Admins group was removed from the Local Administrators group on a member server. Reason being, apparently some business “administrators” would do this every once in a while which would deny the real administrators access. This issue was easily addressed by setting up a multi-entity search to send an alert when this activity was detected. To set up such an alert, simply add two elements to the “What” criteria (image and description below). Obviously this example was specific to the organization who implemented it. However, the point I am trying to make is how powerful multi-entity searches can become once you think about how they can be applied to your environment.
Figure 2: Multi-Entity Search with an “Event Class” entity focused on the From value of ‘Domain Admins,’ as well as a “Local Account” entity that is focused on the ‘Administrators’ group. Both must match for this alert to trigger.
The Protection Template
The Protection Template is a powerful tool offered by Change Auditor. It allows you to protect Active Directory Objects (Users, Groups, GPO etc…), Exchange Mailboxes and Folders/Files from being changed by users and system processes regardless of its native permissions. Think about all the users in your environment. Users with Domain Admin privileges can most likely make any change they want in your environment, or read any file they would like regardless if it is part of their job duty or not. The Protection Template allows you to protect certain objects even from the most powerful of users within your environment.
Coming from a security background this is a feature that I absolutely love. The problem is, one of two things are typically occurring when I engage a customer on it. The first, and most common situation is that the customer is unaware of the functionality and therefore has not implemented it. The second, the customer has it implemented, but is really abusing the feature by protecting WAY too many objects. My recommendation, use this feature to protect critical groups (Domain Admins for example), Users or Folders/Files that could cause harm if unintentionally changed or deleted.
Figure 3: Protection templates can be used on any AD object, ADAM, GPO, Exchange Mailbox and Windows File System regardless of the native permissions associated with the account trying to access it.
IT Security Search
IT Security Search (ITSS) acts as a “Google-Like” search engine for all IT Security related events occurring within your environment. By owning Change Auditor (or Enterprise Reporter, InTrust or Recovery Manager) you get ITSS for free. ITSS easily integrates with the products mentioned above and provides a single pane view into the data contained within them. By having the ability to correlate data between these products it provides a very capable forensics tool to easily search on anything happening in your environment. An important thing to mention is that ITSS becomes more powerful based on the Quest products feeding it. By only having Change Auditor, you will be limited to seeing Change Auditor events and not the data contained in the other products (Folders, Files, Users, Groups and Shares for example would come from Enterprise Reporter).
Figure 4: By searching on any string, you will see all the Events, Files, Groups, OUs, Shares and Users that contain those characters to easily understand what is occurring in your environment.
The most common use case for Change Auditor is providing a view into platforms that were previously difficult, if not impossible, to audit. However, Change Auditor provides the ability to accomplish much more than simply providing a view. I am hoping that by highlighting the functionality above, Change Auditor customers can gain more value out of their current implementations.
The Author would like to recognize Brian Hymer and Robert Tovar for their contributions to this content.