Accounts with excess privileges is a common issue for today’s organizations. Scaling back these permissions is often a challenge. You need data to back up why a certain account is over privileged for its purpose within the organization. Change Auditor can be used to not only help scale back account permissions to exactly what is needed, but also help identify when accounts are being used in ways they were not intended for within your environment.
Limit Privileged Accounts
A major challenge with many organizations is limiting the amount of accounts who are domain administrators. These accounts could be support staff, service accounts running applications, or maybe, end users who say they need this type of access to perform a certain activity. The issue is having the data to show how certain accounts can still perform their job duties without having Domain Admin permissions.
Change Auditor can be used to assist with implementing at least privileged access policy for any privileged account. Simply run a report over an extended period of time showing what your admins are doing with their accounts. Use this data to create an access policy. Using a tool like Active Roles, this policy can be implemented by delegating the appropriate amount of permissions to these users. By doing so, you allow these users to still complete their responsibilities, but without having Domain Admin privileges.
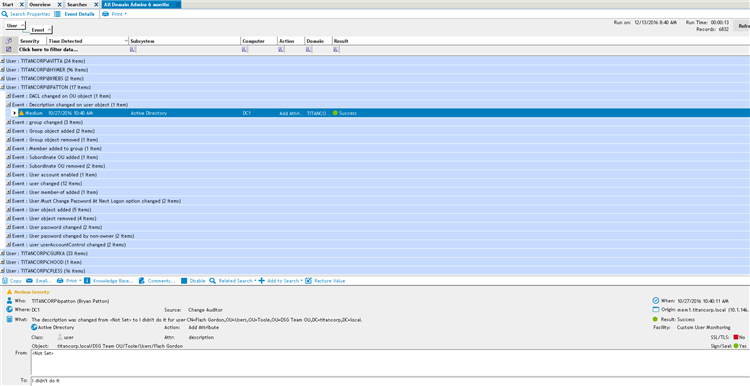
Figure 1: Search on all domain administrator activity over a 6 month period. Events are grouped by User, and then Event to easily show what your domain admins are doing over that period of time.
Alert on User Administration Outside of Identity and Access Management (IAM) Process
Many organizations strive to have an authoritative source of record (HR) to provision and de-provision their users. In addition, access requests and approvals are often required for changing a user’s access. Enforcing this policy is where the trouble comes in. Organizations simply don’t have the data ensure that all user administration is actually done within this process. By utilizing Change Auditors alerting functionality, you can send a real time alert via email any time a user is created/modified outside the IAM Process. This ensures that access granted to your users is approved and authorized, rather than bypassing your security policies.
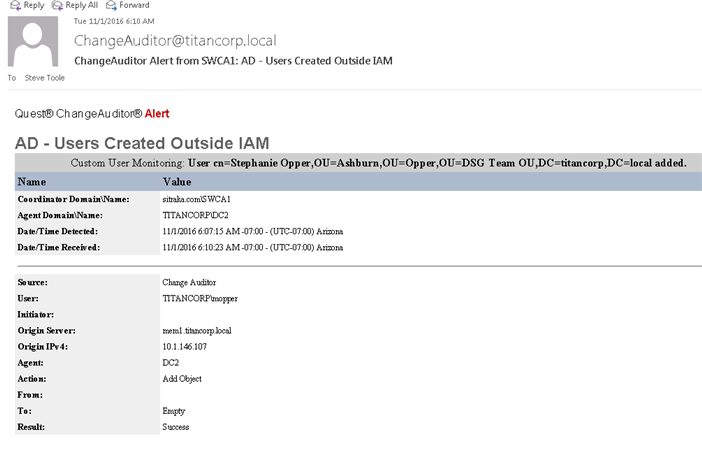
Figure 2: Email alert designed to notify staff anytime a user is created by another account other than the service account used by IAM Solution for user provisioning.
Alert on Unauthorized IAM Service Account Activity
Today, most Identity and Access management (IAM) solutions utilize a proxy account to perform actions on the administrator’s behalf. This is a way to limit the number of elevated users within the organization. Since, all activity is being performed by this proxy account, all activity associated with this account should be initiated from the IAM server. An alert can be set up to notify staff anytime the IAM account is used in another location other than the IAM server. This is useful to make sure the IAM account is not compromised and being used outside the normal IAM process.
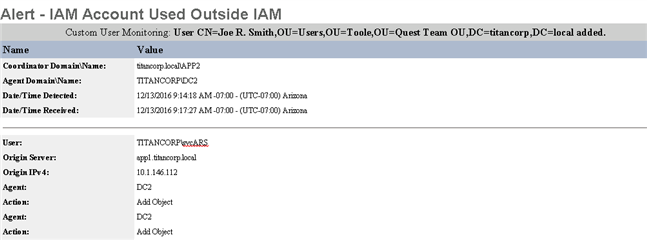
Figure 3: Email alert designed to notify staff anytime the IAM Service Account activity is initiated anywhere other than the IAM server.
Protection Template
A protection template is a way to limit access to objects within your organization regardless of an accounts native permissions. By allowing only your IAM service account access to your users, it ensure only changes initiated by IAM can be processed. This provides security in layers. Regardless if an account has native rights, only the IAM can make the change to a user account. Think about support staff with elevated permissions. These users may have the rights to make changes to user objects, however that is not part of their job duty. Only user changes from IAM ensure there is proper approval associated with the user access change.
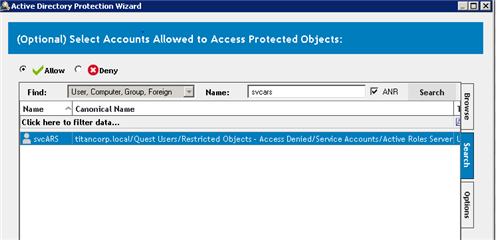
Figure 4: Use a protection template to allow your IAM service account access to the OU where your users are located.
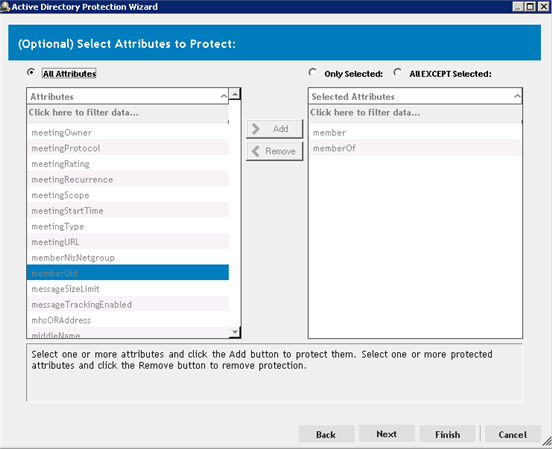
Figure 5: The protection template allows for flexibility. Using the wizard you can protect all attributes of an object, or target specific attributes for a more granular approach.
The most common use case for Change Auditor is simply to provide a view into what is actually occurring on your AD environment. While this does add value, it turns your security posture to becoming reactive in the event of a security incident. By taking advantage of functionality above, it is easy to see that Change Auditor can be used to be proactive in securing your environment.