Something really cool about honeypots and deception technology, in general, is that you can see a hacker or a penetration tester in action with very little false positive notifications. Deception also can help with detecting yet unknown threats that cannot be captured by detection software beeing it SIEM or EDR or both. Please, tell me you have both in 2020, or at least that you have Quest InTrust
But for deception (honeypots) you need to plot traps first - some highly privileged accounts which are not being used or files/DB that looks like valuable data.
What if such honeypots existed in the system by default and you could be notified if someone tried to go after them? Wait no more - apparently Microsoft is adding a tracing function that will create an event in the Application log if someone is trying to use functionality which represents a known CVE that Microsoft patched. So, keep in mind - this is for PATCHED CVEs. Yes, you need to update your software and install OS updates
Here is how the event looks like:
No fancy EDR required to capture CVE-2020-0601 attempts (after patching). Just ensure you're forwarding Application log events. Currently, CVE-2020-0601 is the only Microsoft code (AFAIK) that calls the CveEventWrite API so event noise is not a concern. https://t.co/DwRqboJA7C pic.twitter.com/JWPnaMaIqB
— Matt Graeber (@mattifestation) January 14, 2020
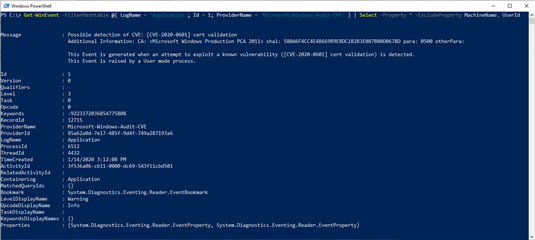
It's definitely not the first time someone proposed to use native events to trace attempts to exploit windows applications and OS vulnerabilities. Project SIGMA, for example, is great in terms of identifying regular events or chain of events that represent a potential attack, but here we get an event which is a security incident by itself - someone tried to exploit a known vulnerability there is no other word for that - this is a potential attack
In Quest InTrust we will research how this event behaves, looks like as of now, only couple of recently patched certificate services utilize this method of notifying about potential attack, but I would expect Microsoft to add this event with any new CVE they fix, actually, all other vendors should follow this, I'll make sure InTrust and other Quest products can start following this practice.


