Hello Support Team,
I've general question related to usage of ADPW tool.
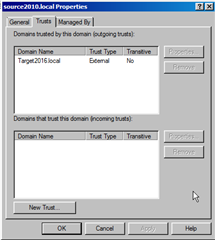
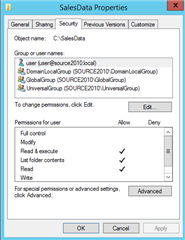
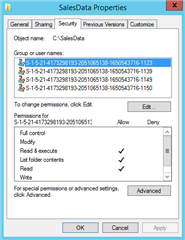
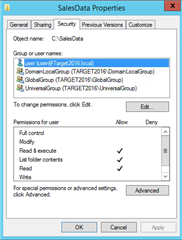
Question: If resource is secured with Source Domain Local groups only && Resource Server (Source domain) has been moved to Target domain, then do I still need to process Source Domain Local groups using ADPW in order to add the Target objects to the Source Domain Local groups?
Please answer and explain.