The cyber-security community is buzzing about this recently unveiled vulnerability in Windows Textservices Framework.
"Project Zero: Down the rabbit hole" https://googleprojectzero.blogspot.com/2019/08/down-rabbit-hole.html by a security researcher Travis Ormandy (https://twitter.com/taviso)
In a nutshell - all Windows versions are affected and hackers can do everything with it: spy on users and administrators typing their passwords, launch processes with system privileges, and many others. There is a special tool that can be used to research the vulnerability "ctftool" and we can count days until the code is available in the popular exploitation toolkits.
The way it works - it uses a text services subsystem of Windows OS (which is responsible for all sort of things around displaying handwriting tools, helper text inputs for Asian languages and all other text input related stuff) as a proxy to then use any process in the OS again as a proxy to launch another sub-processes or to spy on text operations such as password typing.
This is bad, but fortunately, Microsoft already released a patch https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1162.
Obviously, it will take time to upgrade all of the possible systems in the infrastructure and on top of that it's not entirely clear what exactly Microsoft fixed (https://bugs.chromium.org/p/project-zero/issues/detail?id=1859#c24).
I think it's a perfect time to remind everyone that Quest InTrust allows you to enable native log collection for the huge number of endpoints without necessarily requiring any additional license (BTW, we've released an ROI calculator for InTrust). The product can be used to collect security log from all endpoints in your infrastructure and once process auditing is enabled via GPO - all events about process launches. They all will be sent to InTrust's event log repository with 20:1 compression ratio.

Don't forget to enable command line string in these events
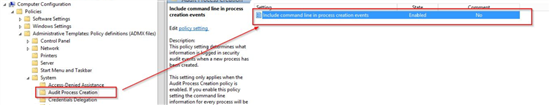
I think this is the most important risk mitigation thing you can do in a situation like that - when some very critical and exploitable vulnerability arises - just enable auditing of all process executions. For many SIEM tools, this could be a challenge because you have to be able to deploy agents on all endpoints and manage increased event throughput and storage. Again - check our ROI calculator - this works perfectly for almost any SIEM out there.
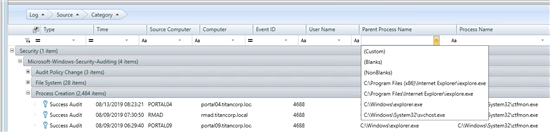
With InTrust, you'll be able to see if someone used ctftool (that's the easiest thing someone would do to exploit any vulnerability - re-use the code that has been used to demonstrate the vulnerability).
The vulnerability allows spawning of child processes under other processes launched with SYSTEM privileges. But InTrust enables you to spot ALL of such spawning in the entire infrastructure, which is a very powerful monitoring tool to have in your arsenal. InTrust watches all of the suspicious parent processes for the ctfmon.exe or suspicious location for the service. Even if you patched it, who knows if bringing your copy of vulnerable service is not a thing?
We are also researching if this text services subsystem produces its logs. We can see that ETW trace providers exist as "logman query providers" on my system demonstrated.
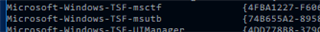
But this is not something that can be enabled easily on a global scale.
Also such sources available in the Windows event log sources list.
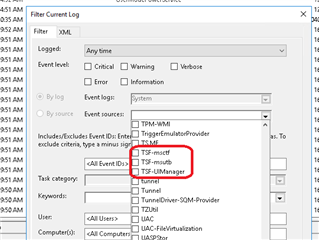
We were not able to identify exact events that these sources may generate yet, but again, I find it very comforting that if they start producing something after the patch or when we know that these log providers could be enabled with GPO for example - you can capture this on a global basis with InTrust.
But again want to remind the most important thing - sheer ability to do global(for the whole infrastructure) process tracking is priceless in my opinion. And this is easy with InTrust.


