What images does the phrase “insider threat” conjure up in your mind? A disgruntled admin actively sabotaging your systems just before penning a resignation letter? A highly privileged contractor installing spyware that will keep exporting sensitive data to him long after his project is complete?
Those scenarios are real enough, but the truth is, the insider threat is much broader than that. After all, it doesn’t take admin-level permissions to inflict some serious damage. An executive might pinch a few trade secrets to enhance her candidacy at a competitor, and an accountant might be tempted to peek at a salary spreadsheet and even share some key tidbits online. Moreover, just about anyone can make honest or careless mistakes, like opening malicious attachments or falling for a whaling email. And, of course, hackers can get control of legitimate user or admin credentials, transforming themselves in the blink of an eye from outside attackers into insider threats. In fact, the insider threat is so pervasive that a full 63 percent of respondents to a recent Quest survey said they had experienced an insider attack in the previous 12 months.
Ready to up your game against the scourge of the insider threat? The first step is to implement a foundational security best practice: Understand and control privilege across the IT environment. Restricting each user’s permissions to what they need to do their job minimizes the power of that account to do damage — whether it’s in the hands of a careless or disgruntled account owner, or a malicious outsider who has stolen the credentials.
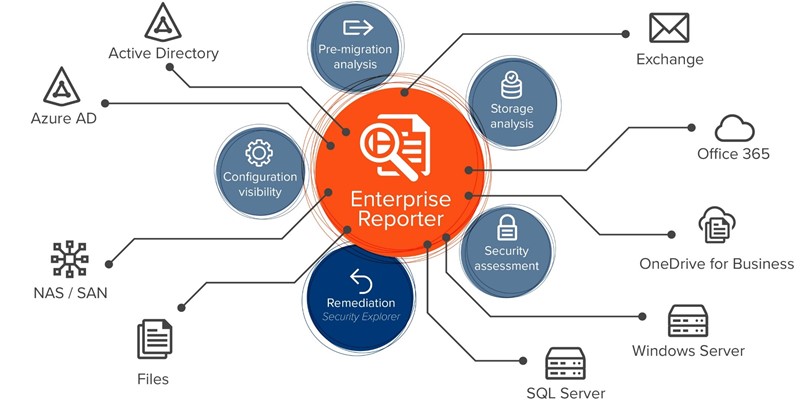
But how can you get a clear picture of who has access to what — and ensure you keep that picture up to date? Quest offers several best-in-class tools that can help. Enterprise Reporter Suite collects data from across your on-premises, cloud or hybrid environment, clears up the complex tangle of permissions that results from group nesting and privilege delegation in Active Directory, and delivers a complete and accurate view of entitlements. For example, you can easily see a list of all AD accounts that can change group membership, which accounts they can change and how they got that access. Even better, Enterprise Reporter Suite includes Security Explorer, which enables you to quickly grant, revoke, clone, modify and overwrite permissions. This combination of reporting and on-the-spot remediation helps you combat the insider threat by making it much easier to understand who can do what across the environment and quickly remove any excessive or otherwise inappropriate permissions to enforce the least-privilege principle.
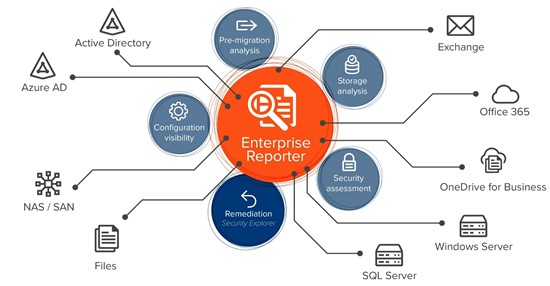
Together, Enterprise Reporter and Security Explorer make it easy to understand and right-size permissions across your hybrid environment.
Of course, once you have a clear picture of access rights in your environment and have cleaned up excessive permissions, you need to audit all entitlements closely to quickly spot any improper modifications. Change Auditor makes it easy to stay up to date on changes across your environment, including changes to access privileges. For example, you can report on all changes to the local Administrators group on Windows servers to make sure no one is elevating their rights without justification. Moreover, Change Auditor can proactively alert you when changes are made to critical groups or other objects — and even protect those objects from being changed in the first place. That way, you can not only get permissions in order, but keep them in order.
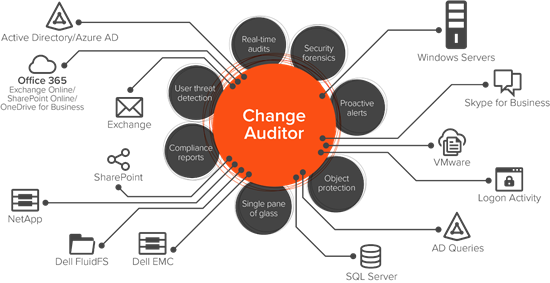
Change Auditor keeps you informed about changes across your hybrid environment, and can even protect critical objects from being changed in the first place.
Of course, understanding and controlling privilege across the IT environment is just the first step toward mitigating the insider threat; you also need to control your Group Policy objects (GPOs) and keep admins in their lanes. I’ll outline both of these best practices in upcoming posts, or you can get all the details right now by downloading our free ebook, “How to Mitigate the Insider Threat: Best practices — and practical tools — for protecting your environment.”