The Marriott/Starwood data breach of 500 million customers is bringing renewed attention to IT integration due diligence in mergers and acquisitions (M&A), especially as it relates to Active Directory, migrations and Office 365 tenant to tenant migrations.
In part 9 of my blog series 10 predictions for 2019: What's in store for Windows and Office 365 pros, we will dive into the continued popularity of the M&A spree, what’s at stake in the race to IT integration, the pitfalls (Such as the one Marriott ran into), and resources to learn how to avoid these pitfalls by others who have gone through an M&A or a migration and consolidation project.
Mergers and acquisitions will increase in 2019 & divestitures are still in vogue
2018 was a banner year for larger, more complex mergers and acquisitions, targeting $5 trillion for the entire twelve-month period. According to Deloitte’s fifth M&A trends report:
- 68% of executives at US firms and 76% of leaders at domestic private equity firms saying their M&A activity deals will increase in number and size.
- Divestiture activity had a 22 point swing upwards in activity between 2016 and 2018.
Given Wall Street’s comfort with the midterm elections and the Trump tax reform that allows US firms to repatriate overseas cash for business growth (i.e., acquisitions), even more migrations will surely take place in 2019.
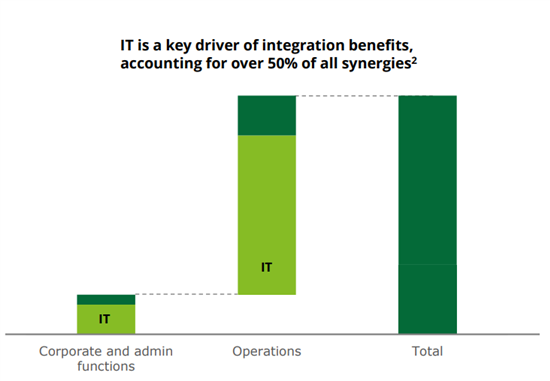
Synergy: Why organizations rush the IT integration of an M&A
M&As seek one thing – synergy. Synergy is the idea that two companies’ combined value and performance will be greater than each individually. The sooner they can achieve synergy, the sooner they realize improved financial performance.
Back in 2015, the CEO of Marriott said the acquisition of Starwood Hotels would deliver $200 million in annual cost synergies by leveraging back-office and operational efficiencies. In fact, 50% of cost synergies are identified within IT operations (Deloitte); so when IT integration goes South and misses its deadlines, an organization will see higher costs than anticipated on their M&A balance sheet. And it’s this pressure that is placed on the IT team to quickly and efficiently execute the rationalization and integration of systems in the race towards Legal Day 1 (LD1).
IT integration pitfalls to avoid in Active Directory migrations and Office 365 consolidations
In the glow of anticipated synergies, IT due diligence at every stage of the deal is forgotten and sacrificed for business agility. Let’s look at a few places where organizations can set up their IT integration for failure with Active Directory and Office 365 migrations and consolidations.
- Establishing an Active Directory trust before performing a cybersecurity analysis. As soon as you start trusting another environment, you’ve increased your attack-surface by allowing a bad guy that's already in the newly trusted environment to traverse laterally into your environment (see Starwood and Marriott).
- Using dirty data adds complexity, cost, and increases security risks. Most AD infrastructures are 10-15 years old with lots of growth and sprawl, so you could be spending way more time moving data that doesn’t need to or shouldn’t be move. And the pressure to merge systems without disruption means a lot of organizations rely too heavily on SID history, which is the equivalent of not changing locks on a house you just bought.
- Not establishing the scope of the migration for LD1. Under scoping (like forgetting about all those B2C accounts in the cloud that need to migrate for LD1 access to critical customer systems) or over scoping (like moving user accounts for employees who are part of HR’s workforce reduction) will significantly impede your cost synergies and/or timelines.
- Not accounting for the complexity of moving legacy apps across ADs. For home-grown applications that are AD dependent, moving them becomes a law of diminishing returns. It appears infeasible to move, so you leave the old directory to work with the legacy environment and set up some sort of coexistence. Guess which one won’t get patched, will get out of sync, will be the security risk?
- Trying to get by with native tools. While native tools are free, they have limited functionality and simply cannot scale to the size and complexity of most AD and Office 365 migrations (and there isn’t one for tenant to tenant migrations).
- Not building in room and backups for the unexpected: Even organizations that successfully avoid all the previous pitfalls are not home free. Things will go wrong. If you can’t roll back migration tasks, you can’t quickly correct those issues and the business will suffer.
Lessons learned: Active Directory and Office 365 migrations
As you can see, there are many ways for the IT integration portion of an M&A to go sideways – and that wasn’t even the complete list. You might be dismayed at this point. But there is good news on two fronts.
- First, this is not untraveled territory by any means. Plenty of organizations have already undertaken AD migrations and consolidations and Office 365 or Azure AD tenant to-tenant migrations, and you can learn quite a bit from their experience.
- Second, while migrations differ in their specifics due to things like the platforms involved and the volume of data being moved, the same basic best practices apply to nearly every migration.
Here are two resources you can use to learn from others who have traveled this road before. These resources will help you survive and thrive in your next M&A.
Active Directory Migration: Seven Lessons Learned
We asked our Active Directory (AD) migration customers to share what they learned through their own migration experiences. Here are the top seven lessons learned that might help you as you plan your own AD migration.
Office 365 tenant-to-tenant migration: Common pitfalls
In this informative white paper, we’ll explore what’s involved in a tenant-to-tenant migration and then a few common pitfalls you might encounter during your project so you can avoid them and be the hero that delivers a successful migration.


