You made it! Here’s the fifth and final post in this series on lessons learned from 2018, all of which are based on a webcast I hosted with Microsoft MVP and Windows security expert Randy Franklin Smith. So far, we’ve covered the Spectre and Meltdown vulnerabilities discovered in modern computer chips, the continued need to guard against the serious weaknesses in Adobe Flash, the devastating NotPetya attack felt around the world, and the massive Equifax data breach.
Today, I’m going to switch it up a bit and look at some analysis we did of the software patches released in 2017 and 2018. Here are the key lessons learned.
1. Patches are released frequently, so you need to keep up.
First, let’s review how often patches were released for four widely used applications, Adobe Acrobat Reader, Google Chrome, Adobe Flash and Oracle Java:
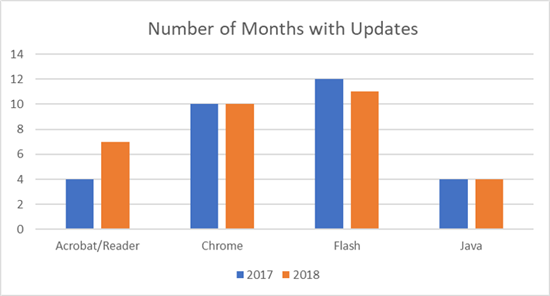
As you can see, the numbers for 2017 and 2018 are very similar for each application, except for Adobe Acrobat Reader, which was patched nearly twice as often in 2018 as the year before. The patch rate for Chrome was rock steady but much higher than Acrobat Reader. And, as I noted in my earlier post, Flash needs virtually constant patching every year.
That brings us to Java, which might look like the most solid application, with just four updates each year. However, that’s because Oracle’s policy is to release security updates on a quarterly basis unless there’s an issue it deems critical enough to merit an out-of-band patch, which didn’t happen in 2017 or 2018. It’s actually rather shocking that a major software company — especially with one that has software as ubiquitous as Java — doesn’t issue updates more often. It’s certainly something for any IT security pro to keep in mind.
2. Zero-day exploits happen pretty often, so patching alone is not enough.
Next, it’s important to ask whether the vendors are proactively discovering and remediating vulnerabilities themselves, or reacting to exploits already being used. Here’s a chart of the numbers month by month for the major third-party applications discussed above and Windows combined:
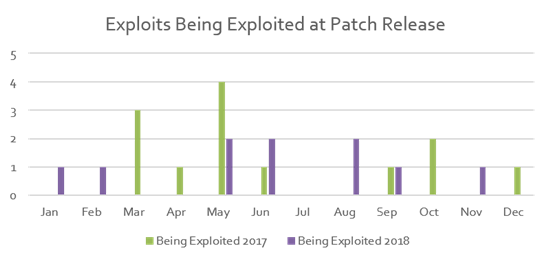
As you can see, during seven months of each year, there were patches released for vulnerabilities that were already being exploited in the wild — which is probably how the software vendor found out about them in the first place. Therefore, no matter how prompt and faithful you are about installing patches, you can’t count on patching alone to keep your IT environment safe.
3. The same types of vulnerabilities remain the most common, so you won’t need to shift your focus.
Security updates are always categorized by the kind of vulnerabilities they address, such as cross-site scripting, spoofing or elevation of privilege. Here’s a breakdown for 2017 and 2018:
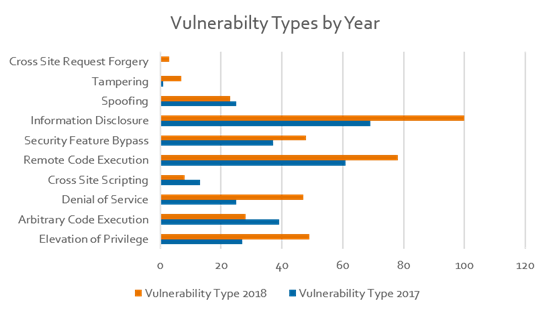
Two things jump out here. The first is that there were more security vulnerabilities overall in 2018 than 2017. The second is that the distribution between the various types stayed largely the same. In particular, the major types of vulnerabilities continue to be information disclosure, remote code execution, security feature bypass, privilege elevation and denial of service. That’s valuable to know, since you can rest assured that the remediation strategies you were working on last year continue to be the right focus this year.
Bottom line
To wrap up this blog series, let’s review the three key takeaways:
- Keep up with new developments, like Spectre and Meltdown. But don’t let every new vulnerability and attack technique rock your world. Instead, focus on the fundamentals of Active Directory management, Active Directory auditing and Active Directory security. As the Maersk and Experian examples illustrate, failure to follow well-established best practices is still all too common, and it’s what really puts an organization at risk of disaster.
- Accept that incidents will happen and remember that it’s really how long it takes you to recover, not the incident itself, that defines the extent and cost of the damage. Back up Active Directory faithfully and be sure you can restore everything, from individual attributes of a particular object all the way up to the operating system level across your entire Active Directory forest.
- The most critical infrastructure component in any Microsoft shop is Active Directory, and the hands-down Active Directory expert is Quest. For nearly 20 years, organizations have turned to Quest software to migrate, manage and secure their on-premises and hybrid Microsoft platforms, including Active Directory and Azure AD, Exchange, Office 365, SharePoint and OneDrive for Business. In fact, we offer the most comprehensive set of Microsoft platform management solutions available, so you can reduce the time and money you spend on management and have more time to drive your business forward.
Thanks for sticking with me to the end! If you haven’t already, be sure to check out our ebook, “Enhancing Active Directory Security & Lateral Movement Detection,” to learn more about how attackers quietly prowl around in your network and what you can do to spot them faster and limit the damage any insider threat can do.


