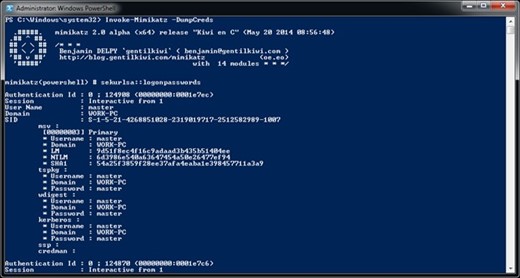
Probably everyone in the IT world heard at least something about mimikatz – a PowerShell library for performing targeted attacks in Microsoft Windows infrastructure. There are numerous other PowerShell toolkits developed to help attackers to recon, to stay undetected and to perform attacks.
Some of the attack vectors can be identified by clever threat detection software that monitors user behavioral patterns to catch any anomalous activities that could indicate a threat or compromised accounts. However, mimikatz is also constantly evolving and other vectors have been added that can help an attacker stay completely undetected from immediate threat detection.
It’s important to remember that you can never “solve” security with one process, one tool or one action. You need to have a complete layer of protection that includes many key components, such as threat detection, event log management and real-time auditing, to ensure your systems and data are protected against even the most experienced hackers/red-team groups.
In this mimikatz example, Quest InTrust can provide an additional level of monitoring that could help catch usage of PowerShell kits earlier in the process. Even if the attacker managed to avoid threat detection and UBA algorithms, either by reverse-engineering user’s behavioral patterns or by avoiding DC-targeted traffic, InTrust will record the attacker’s actions from the very beginning. This means that any attempt by an attacker to stay undetected will be recorded by InTrust, raising the level of awareness of your security team to a maximum. Some of such attacks are being planned and executed in stages for months and months. By using InTrust which captures the PowerShell trail, you can highly increase chances of noticing dangerous actions.
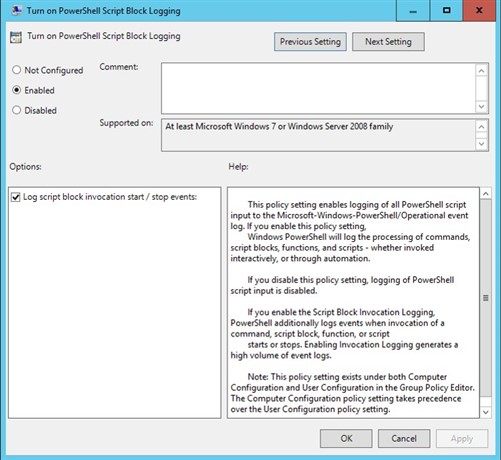
How this works - there is a special audit policy in the Active Directory that allows you to log PowerShell commands launched by users in your IT environment. It’s a script block logging policy in the GPO (Policy\Computer Configuration\Policies\Administrative Templates\Windows Components\Windows PowerShell\Turn On PowerShell Script Block Logging).
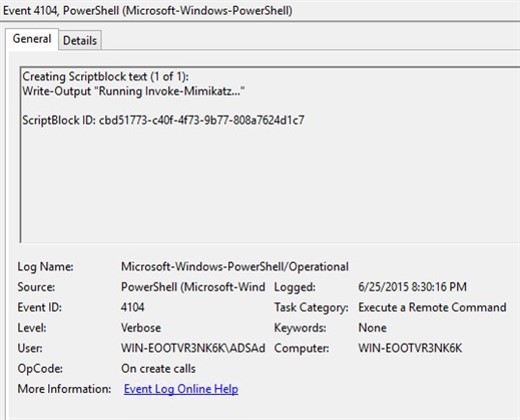
When enabled, all PowerShell command executions are going to be logged in Microsoft-Windows-PowerShell/Operational Event Log, which means InTrust can easily collect these events, parse and present for fast investigation using, for example, IT Security Search. There you will be able to correlate this data with any other activities happening on the same workstations or with the same user account. For example, you could correlate risks raised by Change Auditor with what a user actually tried to do in PowerShell, or correlate the data with AD objects and permissions collected by Enterprise Reporter.
Needless to say, this script block logging is capable of capturing even obfuscated commands, so we can see what a hacker wanted to execute even if he/she tried to hide their intentions by encoding the command. Here is an example:
But besides being able to have a protected, secured and well-compressed PowerShell audit trail, InTrust provides an ability to perform response actions on certain PowerShell commands. You can, for example, immediately disable users who are invoking known PowerShell recon toolkits, such as PowerSploit or anything else that is unwanted such as Invoke-Mimikatz command or its traces in the script blocks.
Stay tuned and we’ll publish more information on how these types of PowerShell attack vectors can be captured, investigated and mitigated with Quest InTrust.