In recently released Update 1 for InTrust 11.4.1 there is a hidden gem – Suspicious process was started rule, it allows detection of hidden steps that ransomware and malware would do to achieve persistence, hide their tracks and disable protection of the targeted system, by responding to such an alert you have good chances of stopping an attack before it makes any damage.
How to enable the rule
To make it work you would need to enable it in the InTrust Manager, for this you need to enable All Windows server site by adding computers into it
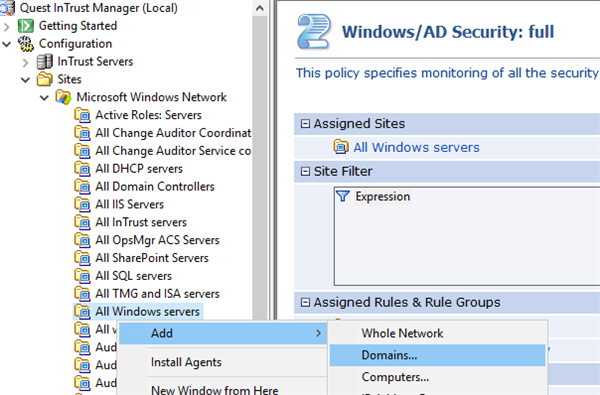
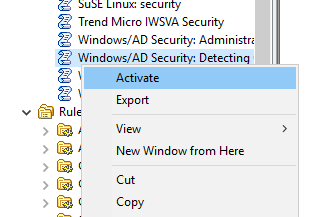
Then activate the corresponding Real-Time monitoring policy
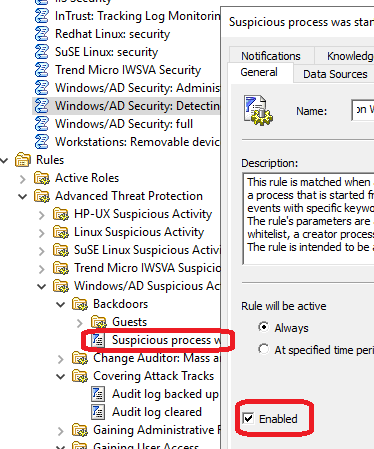
Enable the rule
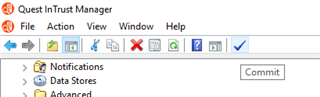
And don't forget to click the commit button once done, to apply the changes
The rule is using process tracking capabilities of Windows OS, unfortunately, workflow for enabling these events is less than ideal. You need to enable 3 different settings of the GPO
- Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy > Audit process tracking
- Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Detailed Tracking > Audit process creation
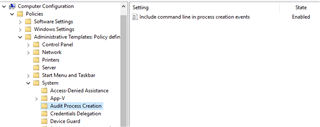
- Computer Configuration > Policies > Administrative Templates > System > Audit Process Creation > Include command line in process creation events
1.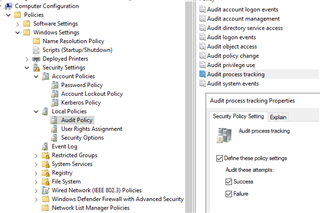 2.
2.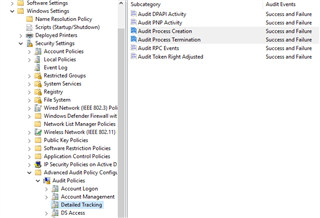 3.
3.
Example
Once enabled, these InTrust rules allow you to detect unknown threats which in the course of their attack chain are demonstrating behavior that is known to be bad.
For instance, we’ve checked recently described Dridex malware. Luckily, because of HP’s Bromium project https://www.bromium.com/dridex-threat-analysis-july-2019-variant/ we know in details how it works
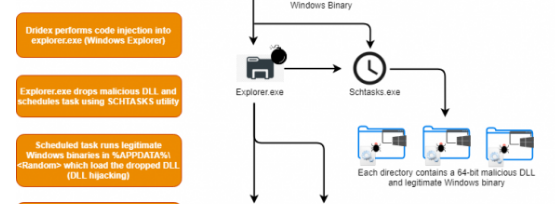
On the persistence step in the chain of its actions, Dridex uses schtasks.exe to ... create a scheduled task. Usage of this command-line utility considered to be highly suspicious behavior as well as another thing that it is doing – Dridex launches svchost.exe with parameters that go to User’s folders or parameters that look like “net view” or “whoami” commands. Here is a piece of the corresponding SIGMA rule
detection:
selection1:
CommandLine: '*\svchost.exe C:\Users\\*\Desktop\\*'
selection2:
ParentImage: '*\svchost.exe*'
CommandLine:
- '*whoami.exe /all'
- '*net.exe view'
condition: 1 of them
Details about the InTrust rule
In InTrust we’ve decided to include all of the suspicious behavior in one rule because most of these actions are not specific for particular ransomware or threat but rather actions which are suspicious and in 99% of cases are being used for bad purposes, such list of actions includes but not limited to:
- processes executing from unusual locations such as user temp folders
- well known system process with suspicious inheritance – some threats could try to use the name of system processes to remain undetected
- suspicious executions of administrative tools such as cmd or PsExec – when they use local system credentials or suspicious inheritance
- Suspicious shadow copy operations – usual behavior for ransomware before encrypting the system, it kills backups
- Via vssadmin.exe
- Via WMI
- Registry dumps of whole registry hives
- Lateral movement by remote process initiation using commands such as at.exe
- Suspicious local group operations and domain operations using net.exe
- Suspicious firewall operations using netsh.exe
- Suspicious ACL manipulations
- BITS usage for data exfiltration
- Suspicious WMI manipulations
- Suspicious scripting commands
- Attempts to dump secure system files
The combined rule that we’ve created works very well in detecting threats such as RUYK, LockerGoga, and other ransomware, malware, and toolkits for the cyber offense. We’ve tested the rule in real deployments to minimize false positives although, thanks to SIGMA project, most of these indicators are known to be effective and usually produce minimal noise.
Because it’s a monitoring rule in InTrust you can perform a script as a response action on this behavior, you can use one of the built-in scripts or create your own and InTrust will automatically deploy it.
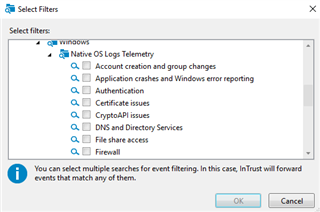
Also because it’s InTrust you can check all of the related telemetry surrounding the event – PowerShell scripts, process executions, Scheduled tasks manipulations, WMI administrative activity and other – make sure you are collecting logs defined our best practice filters for SIEM forwarding, we’ve identified most important event log telemetry that should be used for forensic investigation in a security incident situation.
Besides suspicious process creation we’ve added the following new rules:
- PowerShell downgrade attack - when someone is using an old version of PowerShell on purpose - older version didn't have auditing capabilities
- High-privileged logon - when accounts which are members of s specific privileged group (such as Domain Admins) accidentally or because of security incident login interactively on endpoints
In this update, we also added new ransomware extensions for the Ransomware detection rule that should work in an unlikely :) event nothing else worked and ransomware started to encrypt your File Server – you’ll need to use Change Auditor for File Server to generate the required telemetry. Check how this works in a video.


