Many migration customers execute long-running migrations using Metalogix Essentials for Office 365. This blog post covers two main topics in support of these customers:
- Authentication, Authorization, and Permissions
- Configuring Essentials for Office 365 release 2.5
Authentication, Authorization, and Permissions
This section covers authentication, claims based authentication, authorization, and delegated permissions. Claims based authentication is configured in Essentials so that the authenticated user is not required to re-enter their credentials frequently. In addition, we are using an app to delegate permissions to the authorized user.
Authentication is the process of proving you are who you say you are. Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identification, such as to enter a code on their mobile phone. https://docs.microsoft.com/en-us/azure/active-directory/authentication/overview-authentication
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks
A claim is information that an identity provider (e.g. Azure AD) states about a user inside the token they issue for that user. https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-saml-claims-customization
Claims-based identity enables applications to know certain facts about the user, without having to interrogate the user to determine those facts. The facts, or claims, are transported in an "envelope" called a secure token (e.g. access token). Access tokens contain information (claims) that web APIs, such as Microsoft Graph, use to validate the user and to ensure that the user has the proper permissions to perform the operation they're requesting.
Essentials for Office 365 uses bearer tokens - a lightweight security token that grants the “bearer” access to a protected resource. A valid bearer token keeps the user's authentication alive without requiring him or her to re-enter their credentials frequently. The access_token can be used for as long as it’s active - up to one hour after login or renewal. The refresh_token is active for 336 hours (14 days). After the access_token expires, an active refresh_token can be used to get a new access_token / refresh_token pair. This cycle can continue for up to 90 days. Then the user must log in again. If the refresh_token expires, the tokens cannot be renewed and the user must log in again. https://docs.microsoft.com/en-us/machine-learning-server/operationalize/how-to-manage-access-tokens
By default, a user's claims are stored in the authentication cookie.
OAuth is about authorization. Authorization is the act of granting an authenticated user permission to do something.
Azure AD authenticates users and provides access tokens.
https://docs.microsoft.com/en-us/graph/auth/auth-concepts
Delegated permissions are used by apps that have an authenticated user present. For these apps, either the user or an administrator consents to the permissions that the app requests and the app can act as the signed-in user when making calls to Microsoft Graph. https://docs.microsoft.com/en-us/graph/auth/auth-concepts
Configuring Essentials for Office 365 release 2.5
This section describes how Essentials is configured for authentication and authorization.
Prerequisites
A Global Administrator account used to install the app, implement OAuth authorization, and use claims based authentication.
Download and install the latest trial version of Essentials for Office 365.
Note: I uninstalled the Metalogix Essential Migration Client app in the Enterprise Applications view of Azure AD prior to starting configuration.
Install the App and Configure OAuth
Click on Help \ Profile Manager in Essentials for Office 365. Scroll down to the bottom of the screen. Enter the Global Administrator account credentials for the target tenant. Click on Authenticate App to continue.
Note: See the blog post on Using OAuth authentication with Essentials for Office 365 and Content Matrix (if you are using version 2.4 of Essentials).
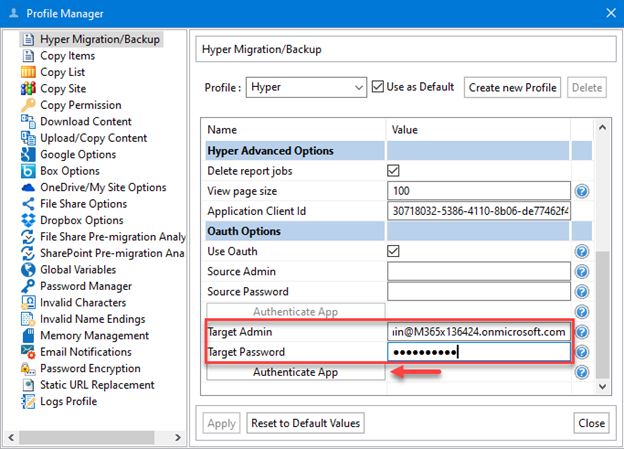
The Authorization For Grant Permissions window opens. Click on the account that you want to sign in with.
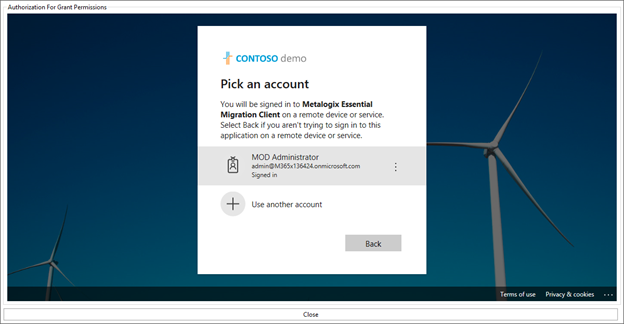
The list of delegated permissions are displayed. Click on the checkbox for Consent on behalf of your organization and then click on Accept.
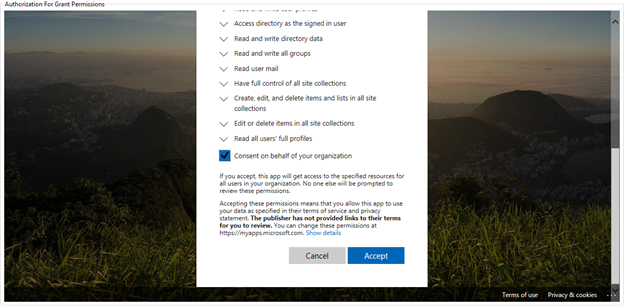
The window below appears to indicate that you have signed in. Click Close at the bottom of the window to continue.
Close the Profile window to continue.
You will see the Metalogix Essential Migration Client app in the Enterprise Applications view in your Azure AD directory.
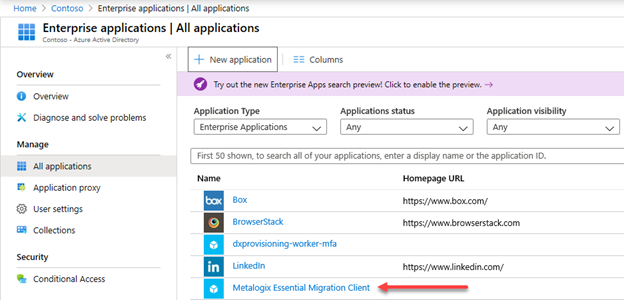
Implement Claims Authentication
Next, I will configure for a file share migration to Microsoft Teams using the Global Administrator account.
Click on Drives \ Copy File Share \ Copy File Shares to Microsoft Teams.

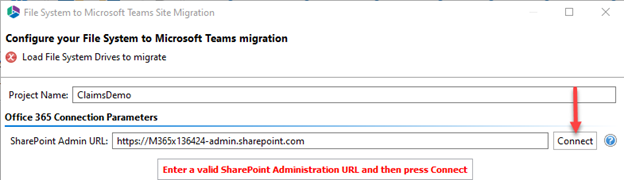
Add a Project Demo name, the SharePoint Admin URL (e.g. https://tenant-admin.sharepoint.com), and click Connect.
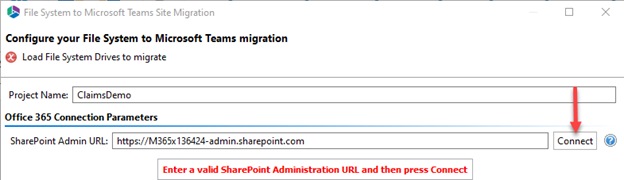
Add a Project Demo name, the SharePoint Admin URL (e.g. https://tenant-admin.sharepoint.com), and click Connect.
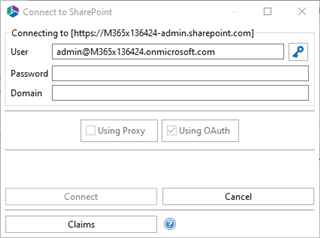
Add the Global Administrator account user email address (password is not required) and click Claims.
The Connect to SharePoint window is displayed. Click Next at the bottom of the window to continue.
The Connect to SharePoint window closes and the configuration screen is displayed again.
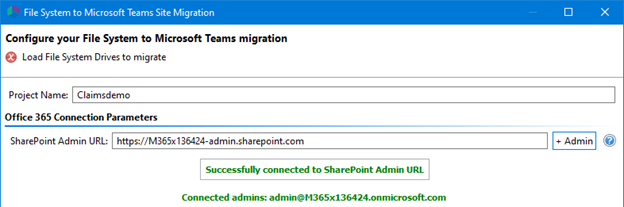
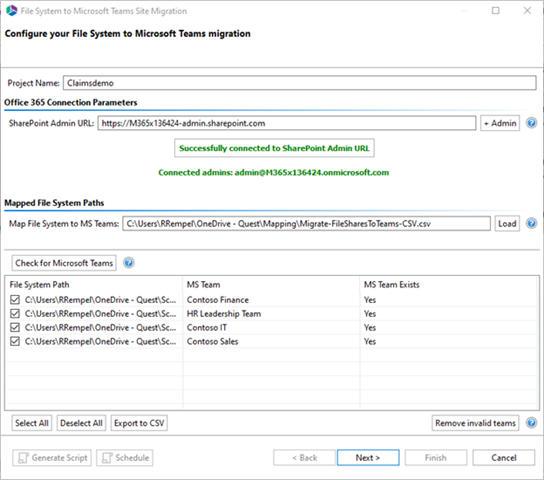
I continue with configuring the migration as I did in my earlier blog post: Your Office is Locked Down and You Need to Access Files On-Premises? I map the drive to Teams, load the mapping file, check for Microsoft Teams, and click Next to start migrating the files.
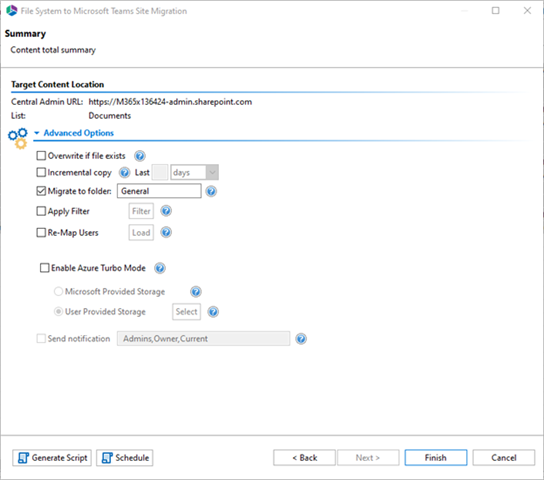
The Summary screen is displayed and I set the filters. Click Finish to continue.
The progress window displays the migration progress.
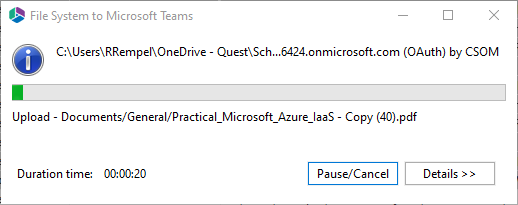
The content is migrated successfully.
Summary
To summarize, this blog post reviewed the key points of authentication, authorization, and permissions. We also reviewed how to install the App, configure OAuth, and implement claims authentication.
The benefit of using claims is that the valid bearer token keeps the user's authentication alive without requiring him or her to re-enter their credentials frequently.
Note:
- OAuth is only supported for Hyper Migration and Hyper Backup.
- OAuth doesn’t work with SSO.
- "resume" will automatically use the original mechanism of authentication when resuming a job.
Please note that we recommend using the Global Administrator account for migrations. There are some limitations to what a SharePoint Administrator can do within SharePoint Online for content migrations.
Next Steps
Read the Essentials for Office 365 User Guide for the configuration steps to migrate to SharePoint Online and/or OneDrive.
Download a trial of Metalogix Essentials for Office 365
Contact Sales when you are ready to buy licensing to proceed with your full migration.


