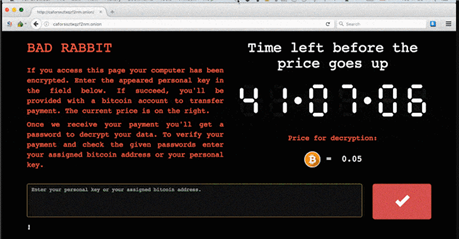
The Bad Rabbit ransomware cyber attack hit last week in Russia and Eastern Europe, targeting news media companies and some transportation companies such as Airport of Odessa in Ukraine. In a nutshell the tactic that bad guys are using is as old as WannaCry and others – find a way to compromise your security (either by phishing technique or by using known vulnerability, or both), install itself on the affected machine, use another vulnerabilities or stolen or captured credentials to hijack other computers and network storage systems, and start the encryption process. This time as a way inside the network it was a fake Adobe Flash installer and known SMB vulnerability. Reports suggest that hackers used different technique to avoid detection by known threat detection solutions, filenames and other IDs were also different from what were identified during similar attacks in the past. In particular, files are being renamed by “Bad Rabbit” using the “*.encrypted” extension.
With Ransomware attacks becoming the new normal when it comes to cybersecurity intrusion methods, are you prepared to withstand such a threat. Do you have a solution? Do you have a tool to fight the threat yourself or do you just depend on a vendor to evaluate the threat and deliver a new instructions for you to protect?
Threat detection and environment assessment tools are critical. However, more and more security professionals recognize a need of pen testing and red/blue team exercises, which have a goal of teaching you how to react when bad guys are trying to avoid being detected by a threat detection, antiviruses and SIEMs.
With Quest InTrust, we have a tool that can help you fight such an enemy using “stealth” mode. You just have to tweak and author InTrust’s real-time alerts and response action to match the current threat, and when you see how lateral and avoid maneuvers of hackers or pen testers work, you can adjust your response strategy.
Again, of course it’s important to have solutions like Antivirus or specialized Threat detection, as this reduces the risk of being under attack. But there is still should be an additional layer of protection for this one particular case when someone very clever tried to avoid being detected or when it’s a new threat and you have to learn as you go. Collecting and consolidating native Windows and Linux event logs is exactly what you need to help fight a threat that is new and doesn’t match any pattern or adjusted its behavior to be undetected.
I would also recommend to take a look on our IT Security Search application. Since InTrust data is fully indexed you can perform an investigation yourself, be always in the know what is happening on your systems quickly and without much learning. It’s just like Google – just start typing in the search field and perform fast IT forensics and security auditing.