I wrote an article for the Windows Server News newsletter about a year ago on Active Directory Modernization called “Understanding AD Mod”. You can find the original story here: http://www.wservernews.com/newsletters/archives/understanding-ad-mod-14215.html
When it was originally written, it was done in a way to be generic and not favor any one company. I decided to revisit the article and add some additional content, specifically the tools that my company (Quest) would use in each phase of the modernization. The updated artile is below.
People are starting to use a new term in the IT world, Active Directory Modernization or AD Mod. AD Mod is really just a new twist on an old project. Much of what came to be called AD Mod came from Active Directory consolidation / migration. When Company A buys Company B, the easiest way to get connectivity and start working together is setting up a trust relationship between the two directories. Then the fun begins as work starts to move objects from one domain to the other in an effort to get rid of one domain.
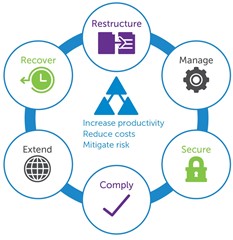 AD Mod is really the same thing, without the merger or divestiture. Think of your existing environment. How many forests do you have? More than one? Very possible for a number of reasons. Now think of the domain structure. How many domains to you have? More than one? Two? Three? More?
AD Mod is really the same thing, without the merger or divestiture. Think of your existing environment. How many forests do you have? More than one? Very possible for a number of reasons. Now think of the domain structure. How many domains to you have? More than one? Two? Three? More?
In the early days of Active Directory, we created multiple domains for a variety of reasons. Security boundaries, keeping Research separate from the rest of the company. Geo-political, laws in some countries required extra domains. Internal Politics. Network and bandwidth restrictions. Regardless of the reasons we had back then, many of those reasons no longer apply, allowing us to collapse the complicated structure that we have today into one that is much more rational.
So how to begin? AD Mod is much more of a journey, than a process. One we don’t need to stop at a certain point. Also, we do not need to start at a specific step. The graphic to the right outlines the processes that we should go through. So where do we start?
Recover
I prefer to start an AD Mod project in the Recover step of this model. We are about to move a lot of objects around. Collapse and remove potentially multiple domains. We can plan and plan but things still go wrong. So let’s make sure, in case of some unforeseen event, we can get back to a good state easily. Now I am not talking about a standard server backup. We want a backup for the Active Directory that will allow us to recover objects down to the attribute level. (If the backup program can also help you in event of a disaster recovery, even better.)
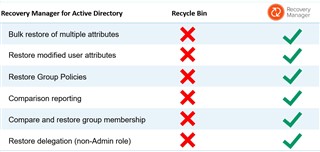
You may be thinking that you can get away with the AD Recycle Bin. Think of the Recycle Bin like the one on your desktop, it is for deleted items. We are going to move and modify items, not delete them. Also, your AD must be at a functional level of Windows Server 2008 R2 for Recycle Bin to work.
So if the Recycle Bin is not the answer, what is? Enter Recover Manager for Active Directory (RMAD). RMAD will allow you to backup the current AD, system state, Group Policies, AD integrated DNS zones, etc. on one or more domain controllers. From the RMAD console, any object, down to any individual attribute can then be restored. For example, as part of the domain consolidation, an admin runs a scripts that is supposed to add the new company email alias to all accounts. But they did not test, and accidently set everyone’s email to “user@company.com”. RMAD will allow the bulk restoration of that single attribute. The table below compares what RMAD provides above and beyond the Recycle Bin.
The next step up from the base RMAD product is what we call Forest Edition. This version provides 2 very useful tools that can assist you. The first is Active Directory Virtual Lab (ADVL). ADVL allows you to create an exact replica of your domain on an isolated network (either VMWare or Hyper-V) that you can test all your steps in. The second tool is the Forest Recovery. This tool scripts a complete AD forest recovery in the event of disaster.
Restructure
The restructure faze is nothing more complicated than an AD migration. This is where we will collapse domains and move objects around. Everything you think of in a migration applies here. Moving objects and collapsing domains is straight forward using todays migration tools. The big thing to plan for here is the applications from the domain to be removed. Most Windows apps will continue to work just fine.
Quest is the leader in migrations tools for both AD migrations and email migrations. I’m not going to spend a lot of time here, you can find more information on the migration portfolio here: https://www.quest.com/solutions/migration-and-consolidation/
Where more time needs to be spent is on non-Windows applications that use the active directory as an LDAP directory. We need to find them and how they are calling into the directory, and how they are calling into the directory. Next, we need to mitigate these applications by either fixing the app directly or by implementing a virtual directory server that will capture the calls to the directory and redirect them automatically to the new directory.
Manage
The management of your directory is something you are already doing today. However, there are some things that you may want to consider adding to your environment. Monitoring tools. The AD is one of the most critical systems in any environment. But no one notices it until there is a problem. If you do not already have systems in place to monitor the health of Active Directory, consider them now.
One of he key tools that Quest provides to monitor the health of your Active Directory is called Active Administrator for Active Directory Health. Full details can be found here: https://www.quest.com/products/active-administrator-for-active-directory-health/
To summarize, Active Administrator for Active Directory Health ensures the health and availability of AD with troubleshooting and diagnostics tools that monitor performance to maintain user productivity. Active Administrator for AD Health helps you:
- Get real-time diagnostic data from a centralized AD health dashboard
- Eliminate learning curves associated with AD performance monitoring
- Pinpoint the root cause of AD problems before they impact users
As your organization gets larger, and you have more people modifying the directory, it becomes harder to maintain consistency with the naming conventions that we want to enforce. So why not start to automate this? People think identity management systems when we talk about this kind of automation. And IdM systems are large, complicated and take a long time to implement. However, there are tools that will allow us to begin the journey and automate the management of AD attributes without having to fully implement an identity solution. If you’ve ever been thinking about identity solutions, this is a good place to start as you can show immediate value to your organization and then implement the harder parts later.
If you are not looking to get into a full IdM solution, you can start with a solution that works on the Active Directory specifically. Quest / One Identity Active Roles provides the ability to setup role-based access into AD to limit what administrators can do. As well, Active Roles can assist with
- True RBAC into AD by admin role
- Simple account provisioning; including enforcing naming standards
- Account de-provisioning workflows to smoothly decommission accounts and groups
- Automatic group creation and membership based on rules
- Overcomes many native-tools limitations
- Manages identities for Exchange Online, Lync, SharePoint Online and many more
- Provides a single, intuitive tool for hybrid environment
See Active Roles information here: https://www.oneidentity.com/products/active-roles/
Ready to step up to a full identity solution? Then look no further than One Identity’s Identity Manager: https://www.oneidentity.com/landing/8188.
Secure
Growing organizations have more fingers in the AD cookie jar. So we want to control them. There are a few things to consider to help secure AD. First, consider 2 factor authentication. 2 factor has evolved from the fobs that we’ve had to carry around all the time. Now you can get software tokens that can be put on your laptop or phone. Some of them never expire as well.
Quest provides a 2-factor authentication solution called Defender. Find out about it here: https://www.oneidentity.com/products/defender/.
Next, look at all the administrative, root and service accounts that you have out there. If you have not already looked at managed service accounts in AD, do it now. Service Accounts tend to be one of the weakest links in our security posture. The password gets set once, and no one wants to change it because of worries that something will stop working. And too many people know that password.
Next consider putting the rest of your administrative accounts (administrator (both domain and local), root passwords from Unix, Linux, routers, etc.) into a password safe. There are two kinds of tools to look at here. First, is just a password safe. This will allow administrates to “check-in” and “check-out” administrative passwords for the systems they need. You want a system that will allow for workflows for approval of the request, time limits on the request, and the password to automatically be set to an unknown password when the request is finished.
Some systems will alternately allow you to check out a session, instead of the password. This is a great option of 3rd parties that may need access to do maintenance, but nothing more. They can make the request, but instead of getting a password, they are presented a session (RDP, Telnet, etc.) to the system they need. Usually you can also control what commands the admin can run. And some systems will allow the entire session to be recorded.
One Identity Safeguard provides a single architecture for privileged access management that is delivered on a secure hardened appliance. This architecture greatly simplifies deployment and management, and accelerates the time to value. Safeguard enables you leverage a unified policy engine and management tools to securely grant access to privileged passwords and sessions. The Safeguard appliance is built specifically for use with the Safeguard software, which is preinstalled and ready for immediate use. The appliance is hardened to ensure the system is secured at the hardware, operating system and software levels. This approach protects the privileged management software from attacks while also simplifying deployment and management.
https://www.oneidentity.com/one-identity-safeguard/
The last thing to think about is providing Role Based Access Control into the AD itself. We have lots of people that need some level of authority in to the AD (think OU admin) but in AD directly, we have to potentially give more rights than we really want (the admin can see the entire AD structure). Tools available today will allow you to “firewall” off the AD and assign much more granular permissions then can be assigned natively. For example, you have an administrator that you want to manage all of the sales people in your organization. However, the AD is designed by location and each location contains more than just sales people. Natively, you would need to over-permission the admin to do the job. Using additional tools, we can create “virtual” OU structures, so I can create a “Sales OU” that contains all sales reps, no matter what location. I can then give my admin rights to just see the new Sales OU and just manage the attributes I want them too.
See the reference to Active Roles above!
Comply
When the auditor asks, “Who put Bill into the Domain Admins group?” how do you answer? If you are auditing the changes to AD, this is a very simple answer. Run a query, find the record for Bill being added to the group, and look to see who did it. Auditing can also help you find anomalous activity that may be a security issue. I have one customer that is using auditing to help them figure out how and when users are locking themselves out.
Quest provides 2 solutions to audit activity in your environment. The first is Change Auditor (https://www.quest.com/landing/8187). Change Auditor watches the activity on your systems and records the changes in a SQL database for easy reporting and alerting. The second solutions is called InTrust (https://www.quest.com/products/intrust/). InTrust will gather Windows Event Logs and Unix \ Linux SYSLOG and store them in a highly compressed file archive.
Extend
Now that we have a well built and secure AD, why not extend it out to UNIX, Linux and Macs? Ever wanted to apply GPOs to your Macs? These are all now possible with tools that will allow us to bridge the AD environment over to the non-AD world. This is especially helpful on the UNIX / Linux side where you no longer have to create a new account on every machine that a user needs access to, they just use their existing AD credentials.
The One Identity Privileged Access Suite for Unix (https://www.oneidentity.com/products/privileged-access-suite-for-unix/) can help you secure and unite your Windows AD environment and you Unix, Linux and Mac environments.
Summary
Modernizing your Active Directory is a journey, not a destination. The phases I outlined above can be done in any order, and there is no requirement to do them all. However, if you do go down this path there are many advantages including reduced costs, tighter security and happier users. Feel free to contact me for more details!
About Me:
Ian S. Lindsay Blog: www.ianlindsay.us Twitter: @ilindsay760 Email: ian.lindsay@quest.com
I have been in the IT industry for over 30 years. As a Strategic Systems Consultant for Quest, I am responsible for providing solutions and architectural guidance to core customers in the Central and East districts. My experiences range from software development on UNIX to designing enterprise network infrastructures using the latest technologies. Prior to joining Quest, I was a Sr. Technology Strategist with Microsoft for almost 14 years. I was responsible for the healthcare customers in Microsoft's Pittsburgh account team.

