Encrypting Ransomware is a family of malicious software (also known as malware) designed to take files on a PC or network storage device, encrypt them, and then extort money in the form of a ransom to unlock the files. This sophisticated type of attack is becoming a growing problem and is affecting organizations of all sizes. While Quest Software doesn’t have a product that will prevent ransomware, we do have many products that can help.
Enterprise Reporter
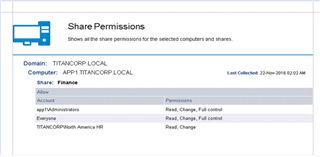
Enterprise Reporter is a reporting tool used to perform a baseline assessment to determine who has access to what within your organization. By performing this baseline assessment, you will be able to determine what systems are vulnerable. In the case of ransomware look for open network shares within your environment. Since everyone can access open shares, it will be easy for ransomware to spread, and ultimately, encrypt those files leaving them unavailable to the organization.
Figure 1: The built-in “Share Permissions” report allows you to discover open shares on your network.
Change Auditor
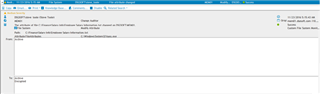
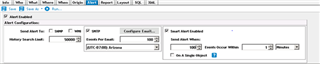
Ransomware is designed to encrypt as many files as it can in the shortest time possible. By using the “Smart Alert” feature within Change Auditor, you will be able to set a threshold when a certain number of the same event occur within a given time frame. This important feature can prove to help save big money by alerting you to take action when an abnormal amount of files are being encrypted/modified by the same user in a short period of time.
Figure 2: Change Auditor provides before and after values making it easy to see and alert on files being encrypted.
Figure 3: This is an example of the smart alert feature ready to take action when 100 file changes occur within one minute which could simulate ransomware. This threshold may vary based on your organizational needs.
InTrust
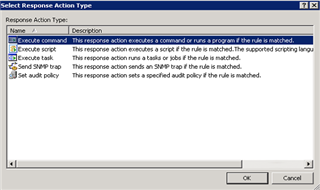
InTrust is a log management solution that provides a framework to build response actions based on events that occur on your system. For example, InTrust could be used to execute a script to disable a user or remove his share permissions when certain conditions are matched that are associated with a ransomware attack. By using this automatic remediation functionality, you can stop a ransomware attack in its tracks and greatly reduce the scope of the attack.
Figure 4: The “Select Response Action Type” menu within InTrust provides flexible options to execute based upon an event occurring.
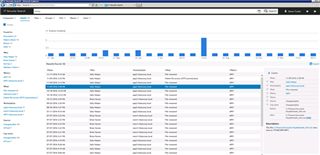
IT Security Search
IT Security Search provides a common interface to all the Quest Software products mentioned. With a quick search, you will be able to correlate all relevant data from Enterprise Reporter, Change Auditor and InTrust to identify the scope of the ransomware attack. This information is critical to determine how far the attack has spread and exactly what files need to be recovered.
Figure 5: IT Security Search provides a google like search to drill down into what has occurred on your network.
There is always a potential for any security incident or attack to occur within your organization. It is impossible to stop them from occurring 100% of the time as the bad guys only need to get it right once to be successful. By utilizing the functionality that these tools provide, you can mitigate the risk as well as the damage incurred of being a victim of a ransomware attack. The products described are all part of the Security and Compliance tools offered from Quest Software Microsoft Platform Management solutions. For more information about our solutions, click the link below to check out our page.