In my previous blog post, I explored the first step in mitigating the insider threat — understanding and controlling privilege across the environment — and reviewed how Quest Enterprise Reporter Suite, Security Explorer and Change Auditor can dramatically simplify the process of implementing and maintaining the least-privilege principle to minimize the damage any rogue or careless insider can do.
Today, let’s explore a second critical best practice for managing the insider threat: controlling your Group Policy objects (GPOs). As you probably know, GPOs are collections of policy settings that enable you to do a lot of cool things: control password complexity requirements, prevent users from accessing parts of the system, rename the Administrator account or reset its password, deploy custom registry values, and much more. In fact, it’s hard to overstate the power of Group Policy in a Microsoft environment. A single errant setting in a GPO can quickly lock users out of business-critical applications, and just one malicious change could cause malware to run when the system starts up, leading to crippling data loss or system downtime.
Because GPOs are complex, they can be difficult to manage using native tools. But as a comprehensive change auditing solution, Change Auditor fully audits and alerts on changes to Group Policy, with all the critical details, including who made each change and exactly which setting was changed. It can even protect critical GPOs from being changed at all— a huge security benefit.
Quest also offers a solution built specifically for workflow-driven, version-controlled GPO management: GPOADmin. GPOADmin integrates fully with Change Auditor and enables you to automate a wide range of GPO management tasks, such as comparing different versions of a GPO side by side and rolling back any problematic changes in seconds. In fact, GPOADmin enables you to granularly control who can do what throughout the environment. You can easily implement workflow processes to ensure that each change is properly reviewed and approved before it is deployed, as well as test GPO changes before deploying them in production. You can even specify whether a change should be implemented when it is approved or on a specific schedule. All changes are audited and tracked, so you’ll know exactly who changed what, when the change happened, and what was changed.
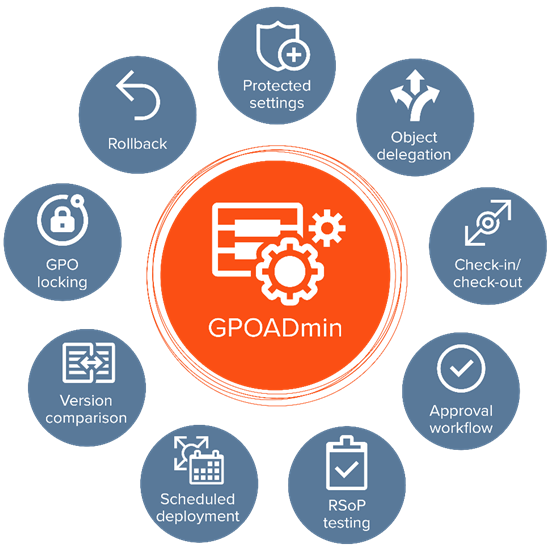
GPOADmin simplifies GPO management and administration to help you mitigate the insider threat.
There is one more key best practice in mitigating the insider threat: keeping admins in their lanes. If you can’t wait for my next blog post to hear about it, or you want to get the full scoop on all three best practices for mitigating the insider threat, check out our free ebook, “How to Mitigate the Insider Threat: Best practices — and practical tools — for protecting your environment.”



