When searching for the best solution for backing up your data, it doesn’t matter whether you are a Fortune 50, Fortune 500 or a small to mid-size organization. What does matter is whether you can find the ideal…
Storage Groups: Your Next Data Protection Bullet
OK – so you may now have an awesome data deduplication appliance in your environment. Using it gives you the peace of mind that data can be quickly backed up and recovered. But what about going further…
Life is about making decisions. Every decision will start with a simple question and assessing the options. What will I wear today? Will I travel by car or by train for my meeting this morning? Simple questions with potentially, a massive impact. You…
Part one of this blog post may be retrieved here.
Part three of this blog post may be retrieved here.
In the previous post we worked together toward laying the foundation for a simple and scalable PowerShell GUI framework for managing Rapid Recover…

In a world where data availability and integrity are paramount to the success of an organization, IT administrators are always looking for the best way to secure their data and keep the business running. One essential component of this strategy is backup…
So we’re finally here, it’s hockey season again. The training camps have concluded and positions are set. The cold weather in the north is setting in and time lace up the pond skates. Each player has a responsibility and they know what job…
Our data and systems are frequently under attack these days. A more traditional attack is from external threats like viruses or hackers trying to gain access from outside of your environment. Threats from inside your environment are on the increase though…

IT professionals today have a great deal on their plate. They are responsible for servers, applications, storage, networking, security, etc. Throw in a Cloud initiative, BYOD, managing a diverse array of endpoints like smartphones and its easy to see…
Are you maximizing your investment of Change Auditor for Windows File Servers? This award-winning solution helps you control and audit changes to Microsoft Windows file servers efficiently and cost-effectively. Change Auditor can also audit and secure…
I like to think I’m a pretty average person. I work Monday to Friday. I’m married. I have a house, cats, a car, and a motorcycle. I love to watch movies and have a passion for BBQ’ing. Pretty much everything I’ve just written is public knowledge and could…
Regardless of which side of the political fence you fall, all of us agree that information is power. To get a sense of this, watch these people try to explain why they’re protesting Donald Trump. The punch line is, they can’t explain it.
…We’ve posted earlier about how hackers get into your systems and steal data from your endpoints, and then how they monetize this stolen information. If you have thousands of unsecured mobile endpoints on your network, it means there are equal numbers…
Windows 10 includes new enterprise security features for authentication and data protection. I’ll cover them in this post, the second in our series on our webinar Under the Hood with Windows 10 Security, for which more than 2,300 sysadmins, IT managers…
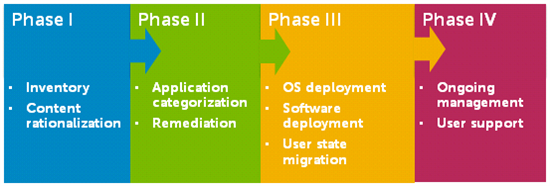
Once you’re acquainted with the landscape and terminology of Windows 10 security, you can turn your attention to Windows 10 migration: moving your servers and endpoints from Windows XP, 7 and 8.
So far in this series about our webinar Under the…
Happy New Year and Welcome Back!
The big question we get when we return from the holidays is always, “What are your New Year’s resolutions?” What makes the question so difficult is that we know that, all too often, the resolutions we make in January…

We’ve all seen the staggering numbers: There are already more than two devices accessing the web for every person on the planet, and analysts predict there will be as many as 100 billion connected “things” in use by 2020. That is a lot of devices to…
Are you ready to manage the massive increase in devices? There are over 2 billion mobile devices shipping every year and over 28 billion IoT devices projected to be active by 2020.
It Doesn't Stop There
More devices means more apps which means an…
A major release of Desktop Authority has been a long time coming. Here are just some of the exciting new features and enhancements included in the latest version:
Off-Network support for domain joined machines
Privilege Manager's application whitelisting abilities has finally met its match, and it's called Blacklisting...
What’s New in Privilege Manager for Windows 4.0?
Blacklist Feature
Are you ready to learn?! Sir, YES SIR!

Howdy, y’all! Ron Colson here from the KACE training team.
I’ve been running the KACE Backyard Boot Kamps (also known as BBK) for a few years now with my awesome colleague Andrew Lubchansky and let…