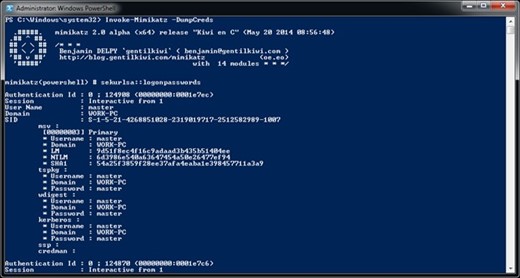
Probably everyone in the IT world heard at least something about mimikatz – a PowerShell library for performing targeted attacks in Microsoft Windows infrastructure. There are numerous other PowerShell toolkits developed to help attackers to recon, to…
- 製品情報
- ソリューション
- サービス
- サポート
- トライアル
- パートナー
- コミュニティ