One of the tools that Active Directory administrators have to help mitigate brute force hacking attempts is the account lockout. Typically configured in a Group Policy, the account lockout policy tallies the number of failed authentication attempts for an account, and if it exceeds a threshold locks the account and prevents it from being used.
Typically account lockouts are caused by an end user forgetting a password, or not realizing their keyboard is caps locked and exceeding the bad password threshold. While annoying for the end user it is generally an easy to understand and straightforward problem for front line IT support to assist with.
But this isn't always the case. The world of technology is changing, and many users use their credentials across multiple devices and desktops. And more and more applications are leveraging Active Directory security, which adds another point where credential failure may be occurring.
These kind of lockouts, where the cause isn't obvious, is challenging for front line support to troubleshoot. Often, these lockout events are escalated to the Active Directory administration team to deal with.
But with Quest, many of these sort of tickets can be handled by first line support. This makes everyone happier - users get a faster time to resolution, front line support gets greater power to resolve, and administrators are able to focus on other tasks.
So how do we enable first line IT support to better troubleshoot account lock events?
Audit the Account Lockout Events
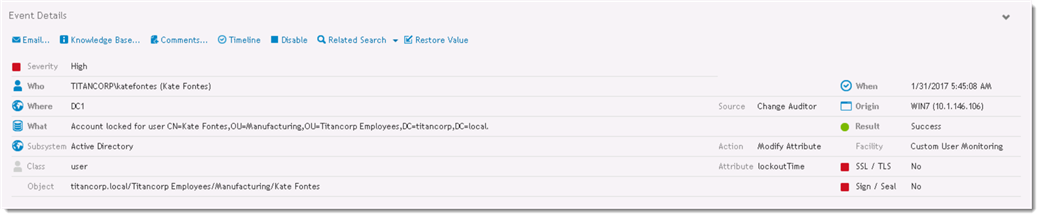
Quest Change Auditor audits Active Directory account lockouts without relying on the Active Directory security log. It generates an event that looks like this when an account is locked out:
The event is focused on providing the five Ws: Who, What, When, Where, and the originating Workstation. The events are designed to be clear and concise - just the facts.
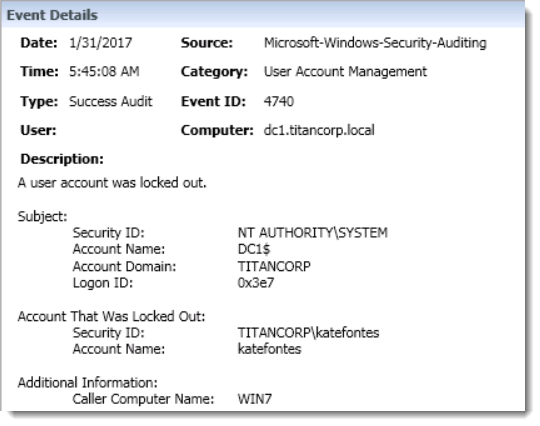
Quest InTrust captures and presents the native security event that provides very similar information:
What we are looking for in Change Auditor is Workstation and in InTrust is Caller Computer Name. These indicate the source system where the account was locked out from, and is usually the key clue to finding the source of the account lockouts. ChangeAuditor and InTrust will attempt to provide this information whenever possible.
Sometimes it is also useful to be able to examine individual account authentication failures as well. InTrust is a particularly good tool for this, as it is uniquely capable of handling the extraordinary volume of failed authentication events that are in a typical Active Directory domain.
Both Change Auditor and InTrust can audit lockout and authentication issues in large environments. These both contain powerful reporting systems with features that allow them to be used for a wide variety of purposes. Many customers use these reporting systems to help troubleshoot account lockout issues, but there is an even faster and more focused way of accessing this audit data.
Use IT Security Search to Quickly Search for Account Lockout Events
Quest's IT Security Search is a component that provides a simple search engine style interface to data gathered by Quest's Enterprise Reporter, Change Auditor, InTrust, and Recovery Manager for Active Directory. If you are licensed for any one of these products, you are entitled to use IT Security Search in your environment. It works through a web browser, and access is controlled through Active Directory security.
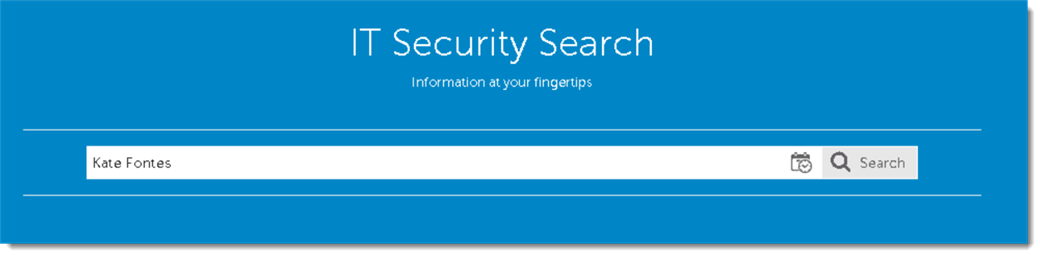
So in our account lockout scenario, a simple way to start investigating would be to browse to the IT Security Search web site and simply type in the user's name into the search box:
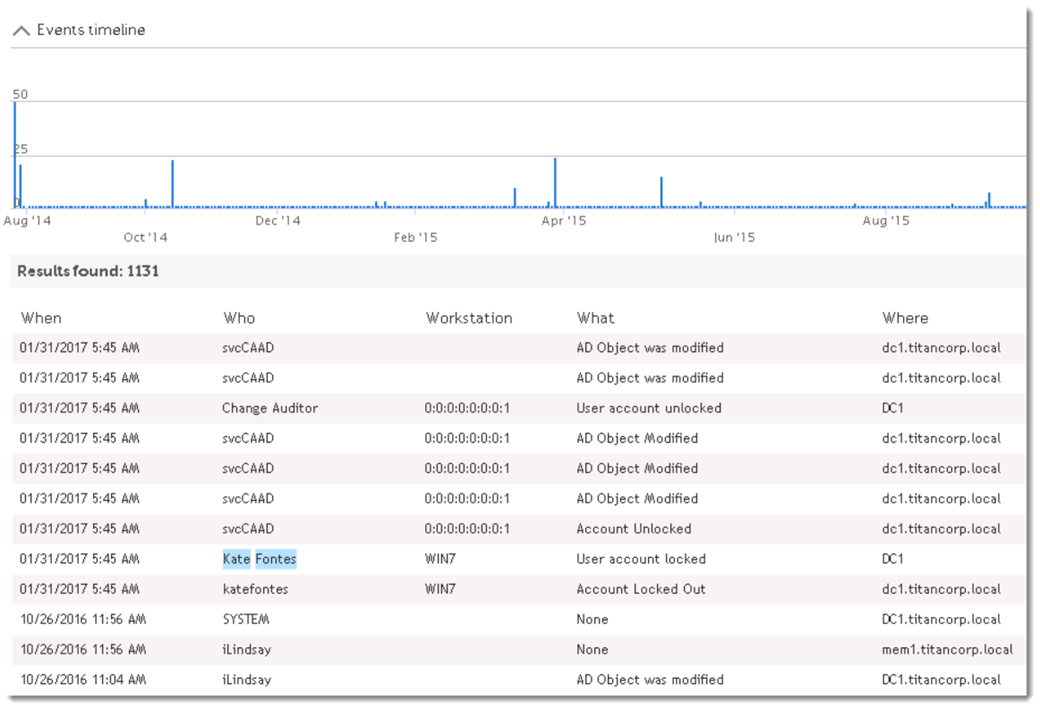
This can return a lot of information! There are simple ways to focus the events to make it easier to find what we are looking for.
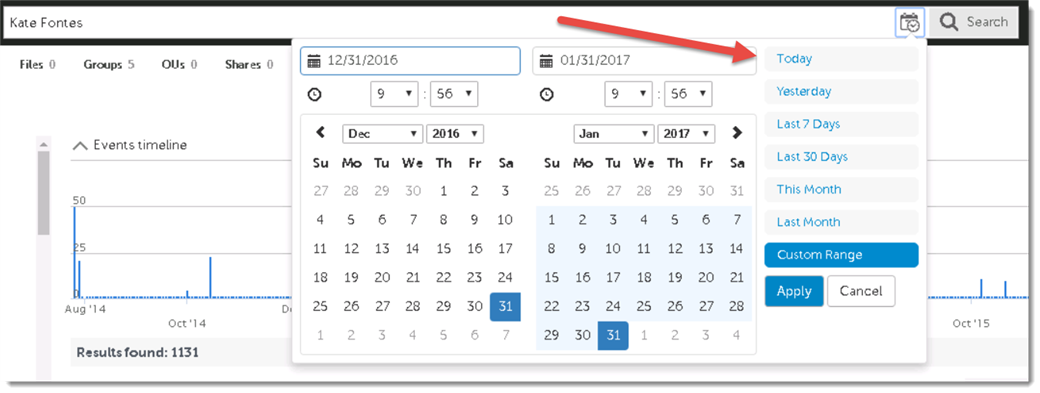
First off, by clicking the calendar icon next to the search bar we can easily restrict the timeframe of events returned to the current day.
Now, from here, we could easily click on the facets, or filtering categories, to the left in order to further filter the search results. But we can also edit our initial search to provide more focused results as well.
For instance, we can see that when we initially searched for our user's name, it returned any connected event, whether it was initiated by the user or not. Account lockout events appear in Change Auditor as being initiated by the user, so let's search on that by entering who:"Kate Fontes" into the search bar:
It is fine to use the full name, but if there is a space you will want to enclose it in quotes.
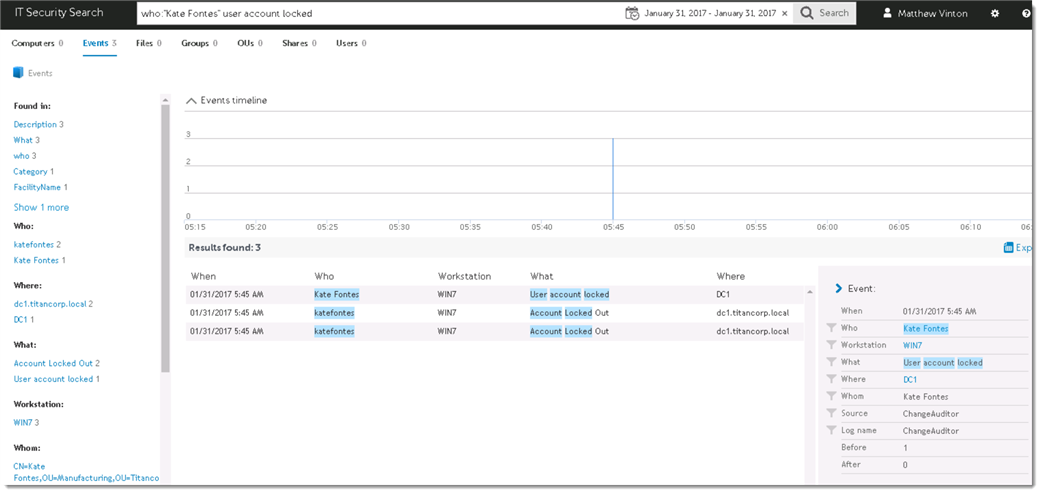
We can further filter this is as well if there are still too many events. The following search will return only events from our user with a relevant message: Who:"Kate Fontes" User Account Locked:
Once the appropriate event has been found, clicking on it will provide details on the timing and if possible the originating system. Armed with this information, front line support can better troubleshoot account lockout events.
To download IT Security Search, log into the support portal using your Quest credentials. If you own Recovery Manager for Active Directory, Change Auditor, InTrust, or Enterprise Reporter you will find the download for IT Security Search listed with the downloads for your product.