If your Active Directory objects aren’t constantly changing, then something is probably wrong with your company.
There’s a continuous process of creating, modifying and deleting almost everything in a normal organization, like users, shares, group memberships, policies, resources and computers.
Worse than all the changes is the nagging likelihood of an AD audit, when an auditor will walk up to your desk and ask you a few choice questions about changes in your AD:
- Who logged in and made the changes?
- What changes have been made?
- What are the users doing with their access?
- When was the change made?
- Where did this happen? What workstation?
If you’re not set up to answer such questions easily, then you face a lot of scrambling to demonstrate compliance, let alone react quickly to a data breach. And even if you can pull event details together, they don’t always answer those questions in a straightforward manner. You may not see a security problem coming until it’s too late.
IT Security Search and Change Auditor
I’ve been posting for the last few days about IT Security Search, a search engine for Quest® platform management products. IT Security Search aggregates the output of Change Auditor, InTrust, Enterprise Reporter, Recovery Manager for Active Directory and Active Roles.
You enter simple, natural language words and phrases into IT Security Search, review the search results and drill into them. Last time I wrote about the way IT Security Search uses data from InTrust to shed light on a security breach, and this time I’ll describe how it uses data from Change Auditor.
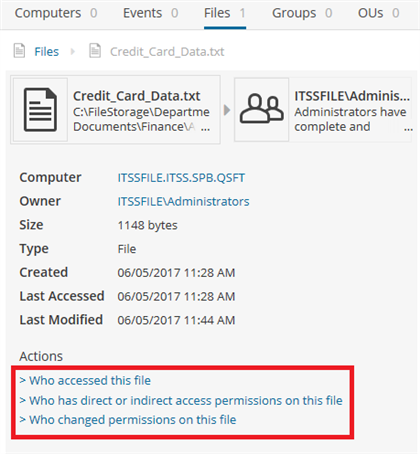
IT Security Search had taken us to a file called Credit_Card_Data.txt:
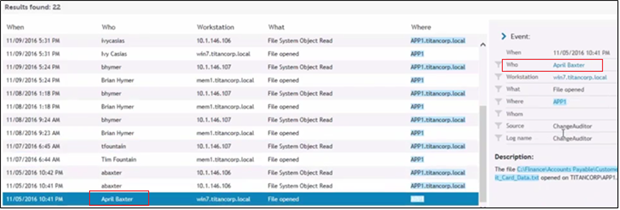
When I click on “Who accessed this file,” I see all the AD entries associated with it in my selected time period:
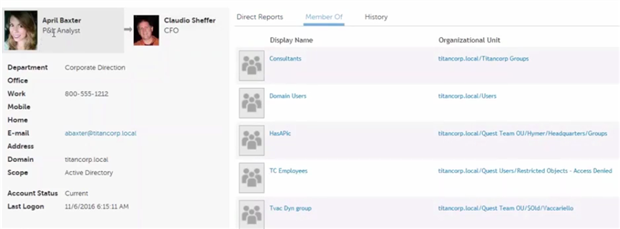
I recognize the users in the Who column, except for April Baxter at bottom. Not only did April open the file, but she did so it at 10:41 p.m. on a Saturday night. That strikes me as potentially fishy, so I click on her name at right to find out more about her:
Her Active Directory object shows me her status and the groups to which she belongs. I see no reason why she should be poking around in a credit card file on a Saturday night.
That is the kind of suspicious, compelling information IT Security Search can put at your fingertips when you’re researching a breach. Based on the time stamps, permission changes and file access events collected by Change Auditor, you can perform forensics through a single window. And, combined with the data from other Quest platform management products, you can cut a surprisingly sharp forensic trail through almost all of the activity on your network.
On-premises and cloud-based AD auditing
With Change Auditor you can set up ongoing auditing and alerts for sensitive changes; for example, to privileged groups, to groups with access to confidential data and to disabled admin accounts that become re-enabled.
Change Auditor audits both on premises and in the cloud, reaching AD/Azure AD, Exchange/Exchange Online, SharePoint/SharePoint Online, Windows servers/OneDrive for Business, and Skype for Business, along with other applications such as your NAS/SAN devices, SQL servers. By extension, IT Security Search makes data from both on-premises and cloud-based resources available for investigation through its interactive search engine. You can see, track and audit all of the changes taking place in your environment.
Next steps
Best of all, IT Security Search costs nothing beyond the licensing costs for the Quest platform management products it runs with. Paired with Change Auditor, it’s a fast, effective way to perform IT forensics in your Windows environment.
Start today your 30-day trial of any of these solutions: Change Auditor, InTrust, Enterprise Reporter, Recovery Manager for Active Directory and Active Roles. Individually or in combination, they generate and pull information from disparate systems and devices that IT Security Search correlates into a single web interface for easier auditing and analysis.
In my next post, I’ll describe Windows reporting and deep dives into access, groups and permissions, powered by IT Security Search and Enterprise Reporter.