Currently 30% of companies in the United States are using the NIST Cybersecurity Framework to manage risks with projections of 50% by the year 2020 (https://iapp.org/news/a/the-future-of-the-nist-cybersecurity-framework/).
Quest has a broad portfolio of products that can help with these different stages, but I wanted to highlight how our Microsoft platform management solutions can help with capabilities to manage risk around Active Directory and access to your data.
Identify
Simple questions such as “What is this user allowed to do?”, or “Where does this group have access?” can be quite challenging to answer. Without understanding who is able to do what it is impossible to implement safeguards to mitigate risk in your environment.
A common report many will run is to identify group memberships that provide privileged access. However, I think many organizations would benefit from first identifying what privileged access is. Some may consider any user that can make changes on another user is privileged access, but you could even consider someone that has access to a lot of data or applications a privileged user as well.
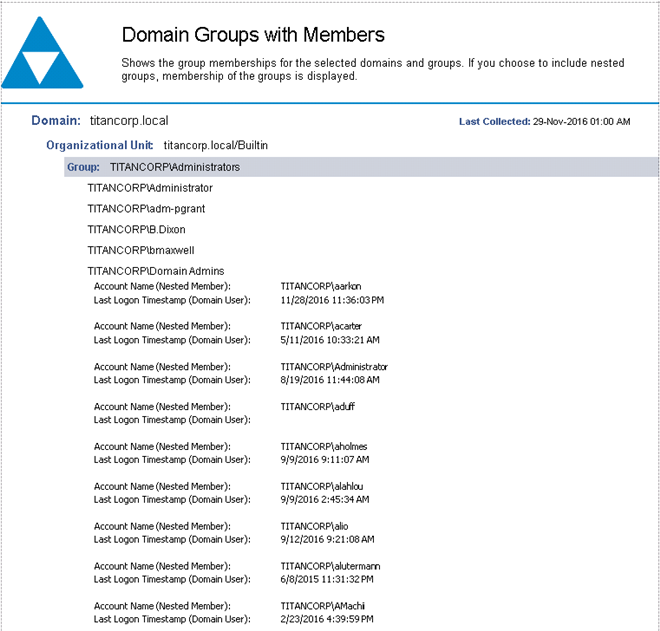
Reports can be automated. Here is an example of a report that can be scheduled and emailed to an auditor on a regular interval that could show “privileged groups” that an auditor wants to validate membership (note that we can also expand out nested group membership):
Caption: Screen shot of Enterprise Reporter
However, what may be extremely beneficial is another report where we can identify users that can make changes on other accounts (not just groups, but perhaps where an individual has delegated rights):
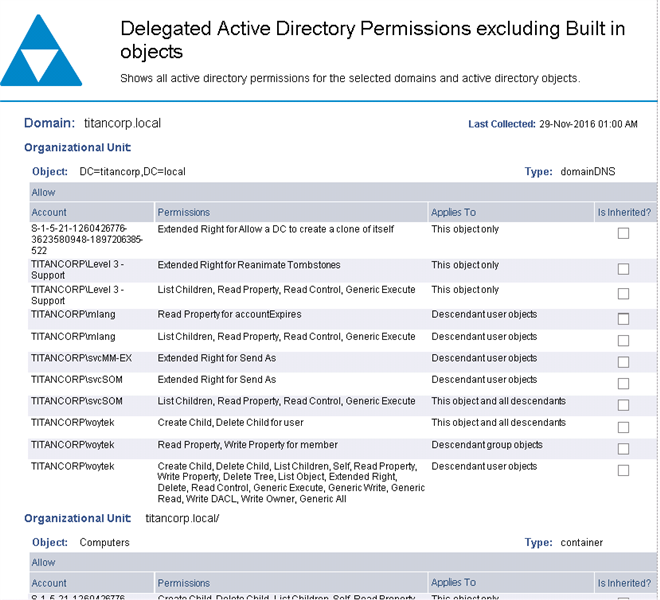 Caption: Screen shot of Enterprise Reporter
Caption: Screen shot of Enterprise Reporter
Identifying these entries may identify some backdoors existing in your environment that you can now remove if unnecessary.
The use of groups is now expanding from not only on-premise Active Directory but now to Office 365 Groups. These groups can provide authorization to Yammer, SharePoint, and other applications, and Quest Enterprise Reporter has the ability to report on this group membership as well to validate who has access (and someone should check to see if these people still need access on an ongoing basis).
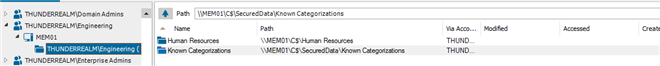
When setting permissions on your unstructured data, you can permission who has access based on a group or another account. Unfortunately the group owner typically has no visibility when a group they are responsible for is used on data. Quest can also identify where a group has permissions across your unstructured data. This could help you in identifying security issues (or even reducing number of groups).
Caption: Screen shot of Security Explorer
Protect
Attack surface reduction can help you protect your environment. This can be by both reducing who has the rights to make changes in your Active Directory, but also by reducing the number of people that have access to your unstructured data. Impacting productivity is a key concern when revoking access so it is vital to create policies to identify who can do what (https://www.quest.com/community/b/en/posts/getting-started-with-least-privileged-access). After creating a policy as to who should be able to do what, Quest has multiple solutions that can ensure that is all your users are able to do. In addition to just allowing someone to perform a task, workflow approval can be configured to ensure several people can approve the task before it is completed to prevent collusion. Also, policies can be implemented to ensure that attributes or GPO’s are configured in a certain way prior to deployment.
In regards to your un-structured data, once you have identify a group or user that may have excessive access (or perhaps you want to find where a group is used and change with another group), you can either delete a permission set across your resources, or just change to another account. Impacting production can be catastrophic so you can also optionally backup the permissions so you can revert to the previous state in the event your change had an adverse impact.
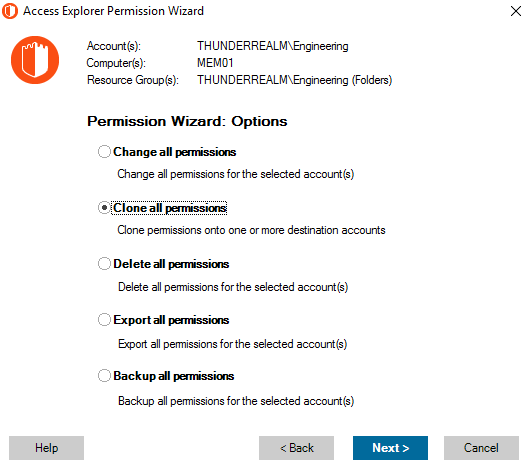 Caption: Screen shot of Security Explorer
Caption: Screen shot of Security Explorer
Detect
Changes constantly happen in an organization. Receiving meaningful information and alerts about the changes occurring helps make informed decisions. Quest has the ability to provide additional audit information than you can receive natively with your on-premise environment, but can also extend out to Office 365 auditing to identify what a user or group has done. Alerting can be configured so that when critical items happen, others can be notified. Sample alerts I have seen some customers configure:
- Changes made by human (if you have identity management products, how many changes should be made directly to AD)
- Service account used out of band (if service should only occur on two machines for an application, alert me when it is used from any other machine)
- Changes made outside of normal working hours
- Permission changes made on unstructured data
- Sensitive data read
Here is an example of who can receive the alert:
 Caption: Screen shot of Change Auditor
Caption: Screen shot of Change Auditor
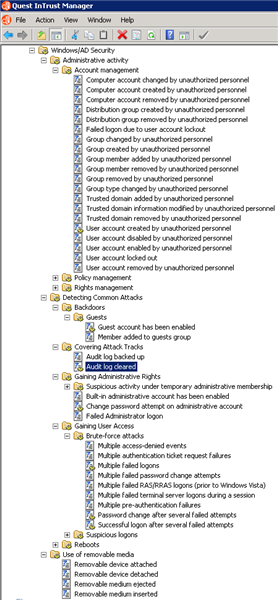
Detection can also occur based on information in native logs. Many times a cyber attacker will try to hide their presence and clear the logs. Quest has the ability to have an agent and cache the logs so we can record what an attacker was trying to hide. Also, Quest can store your log data at a highly compressed rate so you can store it for your retention period.
Caption: Screen shot of InTrust
Respond
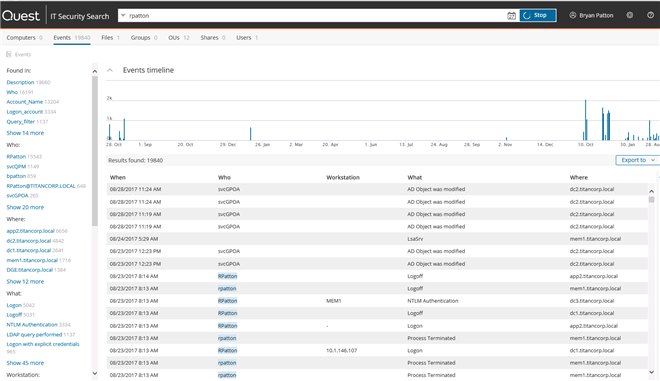
When responding to an incident or security breach, it is vital to have insight to everything that is occurring immediately. Security teams with experience at all levels can benefit by doing a simple search (in this example “rpatton”) and showing all activity on that account based on any log with the ability to click on a hyperlink and see related information regardless of which Quest product contains the information. IT Security Search can help expedite obtaining information to assist you in seeing the chain of event to identify what to do next.
Caption: Screen shot of IT Security Search
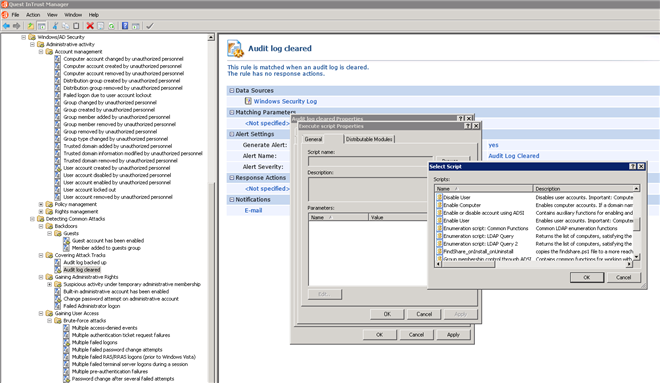
Our other capability around response is to identify what you want to happen when you see an event occur. In the screenshot below, I can configure a script to execute automatically when the audit log is cleared. One example may be to email the security department, but perhaps I want to disable the account that cleared the logs and email their manager. This can be an automated response based on what you define.
Caption: Screen shot of InTrust
Recover
Availability is a core component of security. While Quest does have operational tools to help with AD health checks, Recovery Manager for Active Directory should be considered to help with any organization. The on-premises AD and Azure AD recycle bin both have some capabilities to help with recovery, but many times changes are made at the attribute level that can affect your organization. If the object isn’t deleted, you can’t restore an attribute. If a GPO is modified, you can’t restore the GPO with the recycle bin.
Active Directory is the primary authentication source in most organizations. Quest can provide full Active Directory forest recovery (perhaps schema gets corrupt) and can also build out a virtualized lab that mimics your production environment.
In addition to your Active Directory, Quest can also restore your file/folder permissions from a previous state. Perhaps you are cleaning up the groups on your data, you can backup with Quest and restore in the event someone no longer has access.
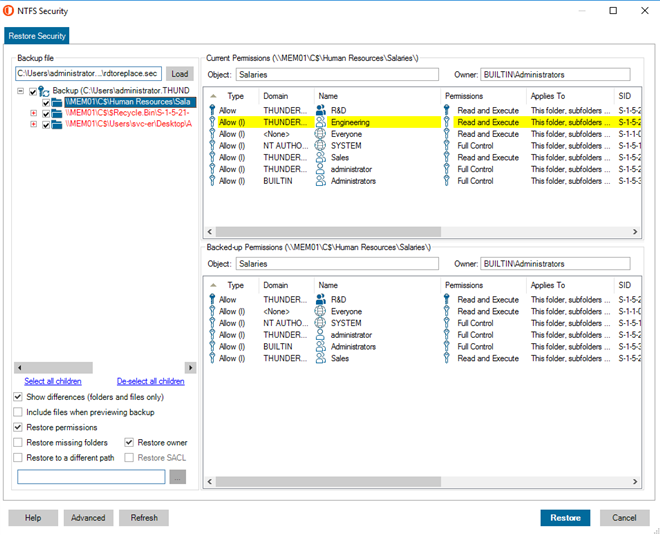 Caption: Screen shot of Security Explorer
Caption: Screen shot of Security Explorer
If you would like to learn more about any of these capabilities, please reach out to your local account executive and we would be happy to have a discussion about your needs!