Microsoft Platform Management
Migration, modernization and cyber resilience for hybrid Active Directory and Microsoft 365. Active Directory and Entra ID are the lifeblood of your business. Because these solutions manage access to the critical applications that keep your organization operating, protecting them must be a top-level priority. The Quest portfolio of solutions fuels true business continuity by helping you migrate, modernize and strengthen cyber resilience of your Active Directory, Entra ID and Microsoft 365 environments.
 02:19
02:19
Why Active Directory and Entra ID?
Active Directory and Entra ID act as the heart of any board-level strategic objective, including mergers and acquisitions, reducing cyber security risks, demonstrating compliance or accelerating digital transformation by moving workloads to the cloud. But when directory services are made unavailable by cyber attacks or errors, risks become reality: Your business halts, growth opportunities stall, reputation suffers and costs quickly mount.
Reduce risk. Operate with resilience. Grow with confidence.
Migration and Modernization
When migrating and modernizing IT environments, it’s essential that the process be a non-event for end users. Yet without the right guardrails in place, these migration projects can take on a life of their own. But Quest has the broadest portfolio to help conquer any migration, modernization, consolidation or restructuring scenario, whether you need to integrate due to a merger or acquisition (M&A), digitally transform to Microsoft 365, or reduce attack surfaces across Active Directory or Entra ID.
- Accelerate Microsoft 365 adoption with faster, more predictable and more reliable migrations – speeding digital transformation to leverage market-changing technology such as AI.
- Decrease M&A integration risk with predictable and secure migrations that finish on time, on budget and with minimal disruptions.
- Reduce the attack surface, increase operational efficiency, and improve security and compliance posture by minimizing on-premises infrastructure.
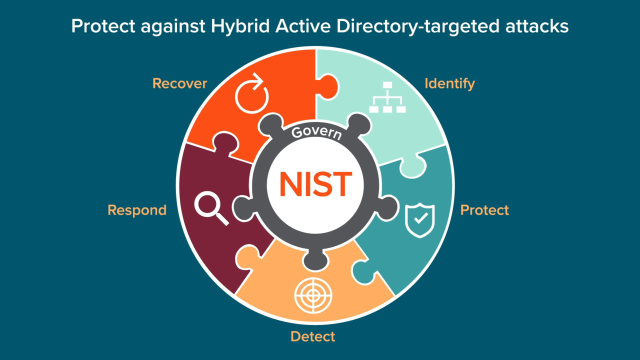
Cyber Resilience
To effectively defend against attacks targeting Active Directory and Entra ID, organizations must take steps to mitigate risk at every stage of the kill chain. Quest provides solutions that align your Active Directory and Entra ID security controls to the NIST cyber security framework and regulatory requirements, thereby increasing resilience while mitigating gaps that adversaries can exploit. These solutions give your Active Directory / Entra ID and security teams the ability to discover and eliminate potential attack paths to critical Tier Zero assets, detect and block suspicious activity, and quickly recover from events that threaten Active Directory / Entra ID, like ransomware.
- Reduce attack surface by proactively identifying and mitigating Active Directory/Entra ID vulnerabilities and misconfigurations.
- Prevent malicious attackers or insider threats from compromising vital Tier Zero Active Directory/Entra ID assets.
- Detect and alert on suspicious or anomalous behavior immediately to respond faster when Active Directory or Entra ID are compromised.
- Accelerate incident investigations to limit potential damage and reduce risk of exposure.
- Recover Active Directory / Entra ID services and vital business assets 90% faster while saving over $19M from ransomware attacks
