The first of my eight predictions for 2021 was that ransomware victim organizations will face government lawsuits. Indeed, as I noted in my previous post, authorities like the U.S. Department of the Treasury (USDT) have already announced they will file civil suits against organizations that pay the ransom to get their data back, along with the cybersecurity consultants assisting in the recovery efforts, intermediaries brokering the deal with the ransom gangs, and even any insurance providers who encourage the payout. Let’s dive into why this is happening and what it means for you and your organization.
Ransomware attacks are becoming far more common — a whole lot more expensive.
First, the why. It’s common knowledge that ransomware is on the rise, but unless you’re really paying attention, you might not know just how bad the problem is. No matter which research you trust, the statistics are grim. For instance, Check Point Research found a 50% increase in ransomware in Q3 2020 compared to the first half of the year, while Bitdefender recorded a whopping 715% year-over-year increase in the total number of ransomware reports globally. North America is being particularly hard hit; according to Lumu, 69 percent of companies there said they suffered at least one ransomware attack.
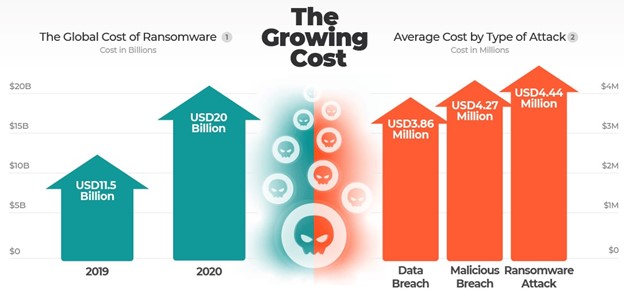
Meanwhile, ransomware is becoming far more disruptive and damaging. Hackers are increasingly likely to follow through on their threats to leak the data they’ve stolen if the victim doesn’t pay, which sends a clear signal to future victims that they must pay up pronto. In addition, the size of the ransoms is skyrocketing: As shown below, Lumu pegs the global cost of ransomware attacks is now $20 billion, up from $11.5 billion just last year, and the average cost of one attack is a staggering $4.44 million — more than the total cost of a data breach.
Organizations are failing to report ransomware attacks
All too often, ransomware victims avoid reporting the attack to authorities. Europol posits many reasons for this. Approaching law enforcement to start a criminal investigation is generally not a priority for victims, who see paying the ransom as the quickest avenue to restoring business operations. Others simply don’t believe authorities can help (even though they do have access to known decryption keys and other tools). Organizations are also concerned that making the incident public is likely to damage their reputation and cost them revenue. Finally, ransom is usually paid in cryptocurrency, which makes it easier for the victim organization to conceal the transaction. Whatever their reasons, some businesses are choosing to hire private security firms to investigate attacks and negotiate ransom payments, even though 17% of victims who pay the ransom never get their data back.
Alarmed and frustrated, authorities respond — but leave many questions unanswered.
This combination of a huge amount of cybercrime evolving into an extremely effective “business model” and the failure of victims to report attacks leaves authorities in an unhappy position. They can’t get an accurate handle on the scope of the problem, learn from one attack to help mitigate the next, or attempt to catch and prosecute the perpetrators. As a result, we’re seeing policies like the one from the USDT to take action against victim organizations that pay a ransom, along with anyone who helps them do it.
However, in 2021, we will see a host of questions emerge about how these types of policies will play out, including the following:
- Which rules apply to which organizations? How will laws and rules in one country be enforced on organization that are based elsewhere? Is every organization that operates in the U.S. in any way at all subject to USDT lawsuits?
- Can you face multiple penalties? What if multiple law enforcement agencies, either within a given country or in multiple different countries, decide to come after you? Will you, for example, face both U.S. penalties and EU penalties?
- Exactly who is liable? The USDT advisory states that it applies to “Companies that facilitate ransomware payments to cyber actors on behalf of victims, including financial institutions, cyber insurance firms, and companies involved in digital forensics and incident response.” The word “including” implies the list is not comprehensive, so who else might be in scope? Shareholders? Individual executives, such as CTOs and CFOs?
- What about other consequences? Lawsuits and fines are one thing, but there is also the specter of criminal charges against victim organizations. Recently, German police launched a homicide investigation after ransomware disabled computer systems at a hospital and a patient died before she could be transferred to another facility. Authorities are currently going after the hackers, but could the victim organization face charges as well? What if forensic analysis finds that their defenses against the attacker were insufficient? Similarly, authorities can hold a victim organization liable for breaking the law if they send a payment to a country that the U.S. has sanctioned over national security concerns — even if the victim is unaware that the payment is going to a sanctioned entity.
To reduce your risk, follow IT best practices!
One thing is crystal clear: In 2021, organizations will be smart to up their game when it comes to preventing, detecting and recovering from ransomware infection. Specific best practices include:
- Take regular backups, make sure they are usable and store them where ransomware can’t touch them.
- Ensure you can quickly restore from your backups, whether it’s individual files or entire Active Directory forests.
- Rigorously enforce the least-privilege principle to limit the reach of malware using stolen credentials.
- Educate all your users about cybersecurity threats and defense best practices. Filter incoming email and block attachments to reduce the number of threats that reach them.
- Restrict code execution, use of removable drives and local administrator access using tools like Group Policy. Monitor those GPOs for changes or, better yet, prevent them from being altered in the first place.
- Keep all your software up to date with the latest patches.
Stay tuned…
That’s it for my first prediction for 2021! Stay tuned for an in-depth discussion of my second one: Forget headline-making data breaches and DoS attacks; the battle for your organization’s reputation is going to be waged in a whisper campaign.