Greetings, my name is Pat Adee with Quest Software. There have been discussions over the use of the SPAN (also referred to as Mirrored) port of network switches for monitoring network data to the FxM Appliance. Although TAPS have been around since the early 90’s, switch manufacturers addressed the need of adding a definable port to monitor traffic between interfaces on the switches. By adding aSwitch Port ANalyzer (SPAN), manufacturers have been able to simultaneously direct conversations from individual switch interfaces or VLANs to a specific interface. This allows a simplified method of monitoring traffic without the need of obtaining extra hardware or inducing network interruptions.
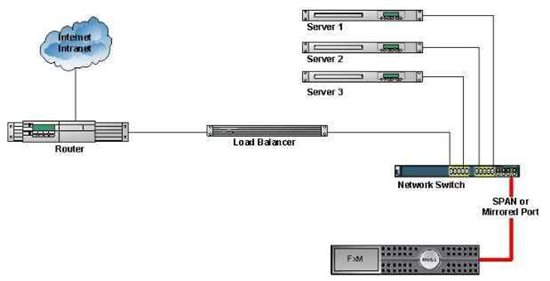
Figure 1: Using the SPAN Port
All FxM Appliances are available with 10/100/1000 copper and/or Multi-Mode Fiber interfaces. SPAN Ports can be either Copper or Fiber depending on the switch and the speed is limited by the port configuration. Referring to Figure 1, the FxM Appliance attaches to the SPAN port and is able to monitor all the traffic that is passed to the SPAN port. The benefits with using the SPAN port include:
- On-the-Fly configuration
- No network downtime
- Zero cost of implemenation
However, Quest has found several limitations to using this method to monitor traffic: Some limitations include:
- Dropped packets due to speed overloading (multiple interfaces going to a single interface)
- Dropped packets due to corrupted data or improper packet size
- Simultaneous porting limitations (restricted number of interfaces allowed to be mirrored)
- Missed interfaces to monitor (didn’t know which port(s) to mirror)
- SPAN port not scalable (as traffic increases over time, more traffic gets dropped)
- SPAN Ports have low priority (switch vendors put more emphasis on serving users needs)
The result of these shortfalls are incomplete or partial sessions. In Secure sessions (those using SSL), a single dropped packet will typically cause the entire session to be dropped or ignored by the FxM as it will be an incomplete session. For these reasons, Quest highly recommends the use of Network TAPs for the FxM Appliance.
Using Network TAPs
By using Network TAPs, the limitations of the SPAN port mentioned earlier are addressed.
- No dropped packets (passive monitoring)
- Corrupted or improperly formatted data will get passed
- 100% of User Traffic to Server is collected
- Operates at line speed
Disadvantages of using TAPs would include:
- Scheduling for network outage (needed to place the tap)
- Some would argue that network taps present a single point of failure but most taps on the market today are classified as passive. Meaning if they lose power, they still allow traffic to flow to the server, just not to the appliance. Redundant power supplies are also options for some taps
- Cost of purchasing TAPs
- May require Channel Bonding to get bi-directional traffic.
- In other words, two taps per connection (normally found with fiber) may be necessary to get ingress and egress traffic. This is dependent on the TAP manufacturer
When it comes to collecting 100% of the traffic, TAPs are the only way to go. This is especially important if your business needs to satisfy Data Security Compliance and Lawful Intercept requirements.
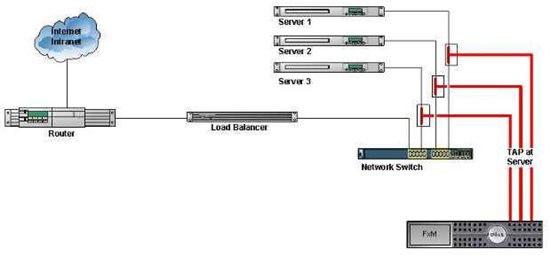
There are several configuration designs available when using TAPs. Using Figure 2, one location for placement is on the individual server(s) that are to be monitored. FxM Appliances are available with up to 4 Monitor ports depending on the Appliance. This would allow for monitoring up to 4 servers. This method also has greater control when scheduling network outages. Since some server environments are redundant, to place a tap would not cause an application outage. This configuration is also advantageous when the servers are in a server farm at a single location.
Figure 2: TAP at Server Connection
Figure 2 above is fine if you are only monitoring a few servers. If your environment consists of multiple servers and/or multiple server farms, the ideal TAP location would be either before or after the Load Balancer. This configuration is demonstrated in Figures 3 and 4. By placing the TAP at these locations, you minimize the number of TAPs necessary to collect the data. A benefit with monitoring the data before the Load Balancer (reference Figure 3), you will be able to observe the individual IP addresses (requester of data) and have a better understanding of User Traffic locations. However, the Load Balancer’s IP address may take on the appearance as the Web-Server providing the response to the requested information. If your preference is to follow which servers are responding to the users request, refer to Figure 4.
Figure 3: TAP in front of Load Balancer
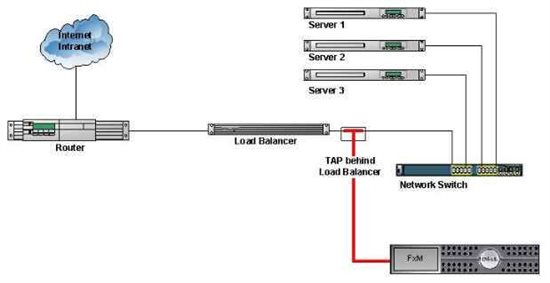
By placing the TAP behind the Load Balancer (Figure 4), you will be able to see which servers are responding to the requested information. However, the limitation here would be understanding who is requesting the information. The Load Balancer typically will appear as the user address making the requester of data appear as a single user. With the Replay functionality of the Foglight Experience Viewer (FxV), you still have the capability of using specific session information (cookies, sessionid’s, etc..) to understand each request.
Another possibility to address recognizing the Users location depends on the type of Load Balancer you are using. For example, if you are using F5 Networks’ Big IP, you can enable “x-forward-for” so that the user IP is included in the packet information. Other possibilities include instrumenting requester information into a custom field embedded in the application. Both methods are common when monitoring user traffic.
Figure 4: TAP behind Load Balancer
Some common Network TAP manufacturers include (but not limited to):
NetOptics http://netoptics.com/
Datacom Systems Inc. http://www.datacomsystems.com/products/network-taps.asp
VSS Monitoring http://www.vssmonitoring.com/
Gigamon Monitoring Switches http://www.gigamon.com/
In Summary:
Quest strongly recommendations the use of Network TAPs for all installations! During evaluations (POC) and FxM only deployments (non-SSL environments) will a SPAN port be reasonably acceptable to use. But Quest’ experience is you will get the best results with the use of Network TAP’s.
For further information regarding the use of Network TAP’s, End User Monitoring or any other Quest Products, please contact your local Quest Sales Team or visit http://www.quest.com/ for more information.